5G Core Network Architecture Zoom-In: Functions, Interfaces, and Security
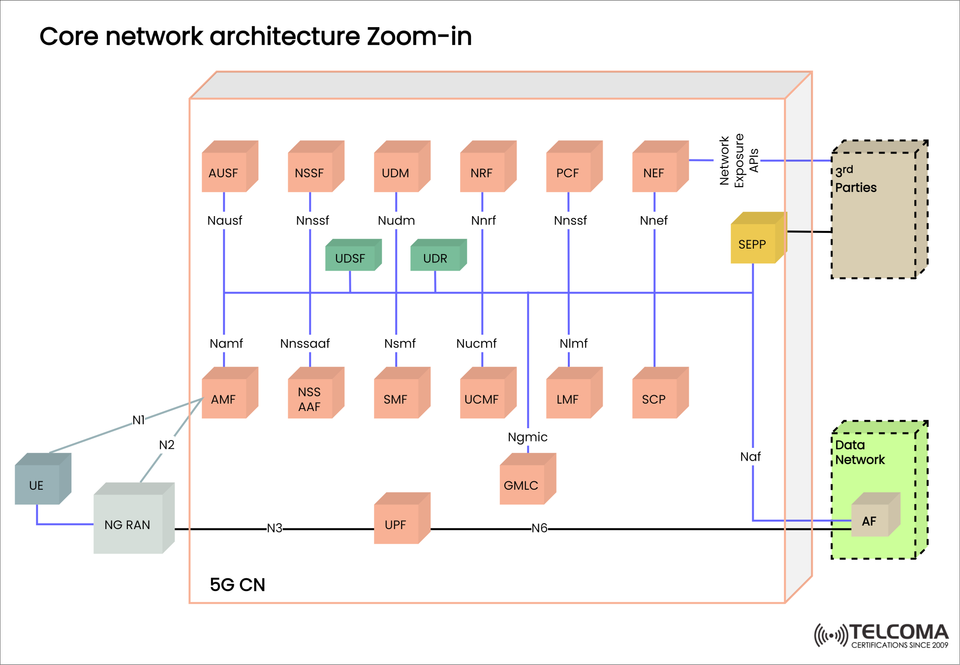

The 5G Core Network (5GC) marks a significant evolution from earlier versions, crafted with cloud-native principles, service-based architecture (SBA), and virtualization in mind. Different from the EPC we had in 4G, the 5GC introduces modular network functions (NFs) that interact through standardized APIs, which helps in achieving flexibility, scalability, and security.
The diagram we uploaded, Core Network Architecture Zoom-in, provides a close look at the functional blocks of the 5G Core, showing how they work together and connect to external networks and applications.
Key Components of 5G Core Network
Built on Service-Based Architecture (SBA), the 5G Core (5GC) allows each function (NF) to provide services to others through APIs. Here’s a breakdown of the main components:
- UE (User Equipment)
This is the end device, such as a smartphone, IoT sensor, or a connected car.
It connects through the NG-RAN (Next Generation Radio Access Network) using N1 (NAS signaling).
- NG-RAN (Next-Generation RAN)
This part manages radio connectivity between the UE and the 5GC.
It connects to the AMF via N2 (control plane) and to the UPF using N3 (user plane).
- Access and Mobility Management Function (AMF)
This function is in charge of registration, connection, mobility, and authentication for UEs.
Interfaces: * N1 with UE * Namf with other NFs
Replaces part of the MME from 4G EPC.
- Session Management Function (SMF)
Responsible for session establishment, modification, and release.
Allocates IP addresses to UEs and enforces policy with the PCF.
Connects with the UPF using the N4 interface.
- User Plane Function (UPF)
This is key for data forwarding and routing.
It manages QoS, packet inspection, traffic steering, and connects to external data networks (DN) via N6.
- Unified Data Management (UDM)
Comparable to HSS in LTE but with advanced features.
Stores subscription profiles, authentication data, and policies.
- Authentication Server Function (AUSF)
This handles authentication procedures with SUCI/SUPI identities.
Works closely with the UDM.
- Policy Control Function (PCF)
Provides policy rules and QoS enforcement.
Similar to PCRF in LTE but offers richer, more dynamic control.
- Network Repository Function (NRF)
Functions as a service registry for all NFs.
It allows for dynamic service discovery and load balancing.
- Network Exposure Function (NEF)
Securely exposes network capabilities through APIs to third parties.
Lets developers integrate 5G features into their applications.
- Security Edge Protection Proxy (SEPP)
Secures communication between different PLMNs (operator-to-operator).
Guarantees end-to-end encryption of signaling traffic.
- Other Supporting Functions
NSSF (Network Slice Selection Function): Chooses the right slice for the UE.
LMF (Location Management Function): Gives location-based services.
UDSF (Unstructured Data Storage Function): Temporarily stores data.
SCP (Service Communication Proxy): Manages communication between NFs.
UCMS (Unified Communication Management Function): Helps manage communications across domains.
GMLC (Gateway Mobile Location Center): Functions as a gateway for location data.
How the Architecture Works
The UE connects to NG-RAN and sends registration requests to the 5GC.
The AMF authenticates the UE with assistance from AUSF and UDM.
The NSSF picks a slice, making sure resources are allocated properly.
The SMF sets up a session and configures the UPF.
The UPF routes traffic to external data networks (like the Internet or enterprise apps).
The NEF and SEPP make sure network services are securely exposed to external parties.
This flow that’s both modular and service-driven allows for dynamic resource allocation, flexible slicing, and secure multi-service operation.
Interfaces in the 5G Core
InterfaceConnectsPurposeN1UE ↔ AMFNAS signalingN2NG-RAN ↔ AMF Control planeN3NG-RAN ↔ UPF User planeN6UPF ↔ Data Network External data trafficN4SMF ↔ UPF Session and forwarding rules Service APIs NFs ↔ NFs Service-based interactions
Advantages of Service-Based 5G Core
Flexibility: NFs can scale independently.
Cloud-Native: Can be deployed in private, public, or hybrid clouds.
Security: SEPP, NEF, and SUCI offer enhanced protections.
Network Slicing: Custom slices for IoT, URLLC, or eMBB.
Exposure via APIs: Lets telecom capabilities drive enterprise innovation.
Comparison: 4G EPC vs. 5G Core
Aspect4G EPC5G Core Architecture Node-based Service-based (SBA)Virtualization Limited Full NFV/Cloud-native Slicing Not supported Native support Exposure Minimal Secure APIs via NEF Identity Protection IMSI exposed SUCI/SUPI encrypted Scalability Rigid Highly dynamic
Challenges in Core Network Deployment
Integration complexity with existing 4G/3G networks.
Interoperability issues across vendors with standardized APIs.
Security risks when exposing APIs to third-party access.
High operational overhead in managing network slices.
Future Directions of 5G Core
AI-driven orchestration for network slices.
Edge-native functions closer to users.
Quantum-resistant cryptography for improved security.
Ensuring seamless migration with 6G research.
Security in the 5G Core Network
One of the big improvements in 5G Core (5GC) compared to LTE EPC is its security by design. The architecture includes several layers of security to fend off threats while still allowing trusted third-party integration.
Key Security Enhancements:
Subscriber Identity Protection (SUCI/SUPI): This feature keeps permanent subscriber identifiers safe through encryption.
SEPP (Security Edge Protection Proxy): This secures communications between different PLMNs with end-to-end encryption for signaling.
Mutual Authentication: Involves user equipment, the network, and application servers to stop any spoofing attempts.
Network Slicing Security: Each slice comes with its own security policies to safeguard enterprise and IoT use cases.
API Security via NEF: This ensures that third-party access adheres to strict authentication and authorization protocols.
These features make the 5G Core much tougher against cyber threats, especially as the number of devices connected rises into the billions.
Orchestration and Virtualization in 5G Core
The cloud-native framework of the 5G Core enables operators to dynamically deploy, scale, and manage resources. This is made possible through NFV (Network Function Virtualization) and SDN (Software-Defined Networking), paired with smart orchestration.
Core Concepts:
Microservices-based NFs: Each network function is divided into microservices, making independent upgrades and scaling easier.
Containers over VMs: Using lightweight deployments boosts efficiency and portability.
Service Communication Proxy (SCP): This enhances communication between network functions, balancing the load and improving resilience.
AI-driven Orchestration: It allows for predictive scaling based on traffic loads, movement patterns, and quality of service needs.
Conclusion
The Core Network Architecture Zoom-in showcases how 5G brings a cloud-native, service-based, and modular design that transforms telecom networks into flexible digital platforms. By integrating authentication, policy control, secure inter-operator communication, and API-driven exposure, the 5GC is geared up to fuel the next wave of digital innovation—from IoT ecosystems to autonomous vehicles and smart cities.
