5G Initial Context Setup and Security Mode Command Explained: Step-by-Step 5G Core Signaling

Understanding the 5G Initial Context Setup and Security Mode Command
In the 5G Core Network (5GC), once a device successfully registers and establishes a session, the network needs to set up the radio access (RAN) and core for securely managing the user’s data. This is where the Initial Context Setup and Security Mode Command come into play.
These steps are essential for enabling User Equipment (UE) to communicate securely with the network. They ensure that encryption and integrity protection are in place while the necessary PDU session resources are set up for data transfer.
The diagram above shows the signaling flow involving:
UE (User Equipment)
gNB (Next Generation NodeB)
AMF (Access and Mobility Management Function)
SMF (Session Management Function)
UPF (User Plane Function)
Let’s dive deeper into this process.
Overview of the 5G Initial Context Setup
The Initial Context Setup procedure kicks off with the AMF after a successful registration and PDU session establishment. Its main goal is to equip the gNB with all the necessary info about the UE, which includes:
UE identifiers (AMF and RAN IDs)
Security keys and algorithms
PDU session resources
Quality of Service (QoS) parameters
This setup makes sure that both the RAN and Core are in sync, ready to efficiently handle signaling and user plane data for the UE.
Key Network Entities in This Procedure
Entity - Function
UE (User Equipment) - The device connecting to the 5G network.
gNB (Next Generation NodeB) - The 5G base station that manages the radio interface and user traffic.
AMF (Access and Mobility Management Function) - Responsible for registration, connection management, and mobility.
SMF (Session Management Function) - Manages PDU sessions and works with the UPF.
UPF (User Plane Function) - Forwards user data and enforces QoS.
Step-by-Step Breakdown of the Signaling Flow
The diagram shows the following steps:
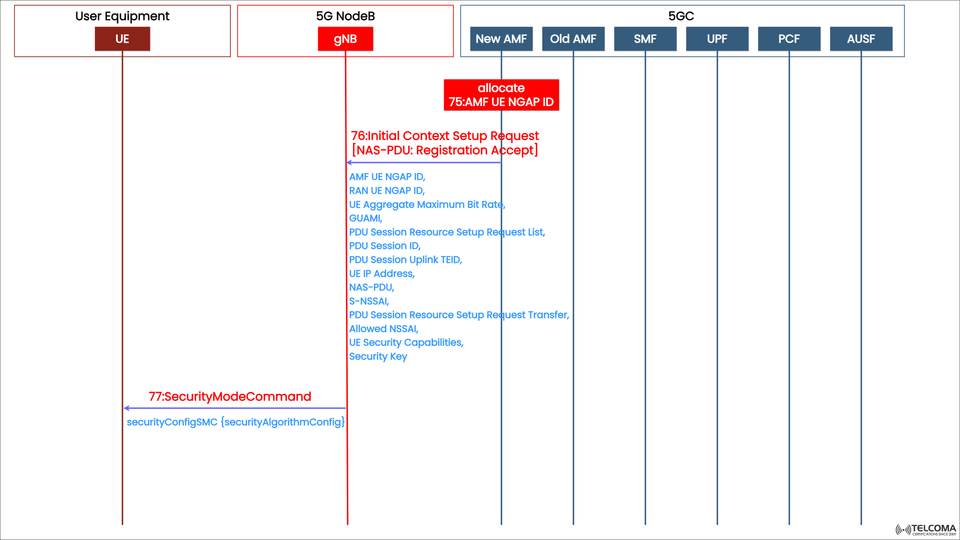
Step 75: Allocate AMF UE NGAP ID
Entity: AMF
Purpose: Assign a unique AMF UE NGAP ID to identify the UE within the AMF.
This ID helps the AMF manage signaling sessions and link NAS (Non-Access Stratum) messages to a specific UE context.
The NGAP (Next Generation Application Protocol) takes care of the signaling between the AMF and gNB, making sure everything is well-coordinated for setting up the UE context.
Step 76: Initial Context Setup Request
Entity: AMF → gNB
Message: Initial Context Setup Request
NAS-PDU: Includes Registration Accept
This part is crucial. The AMF sends a detailed setup request to the gNB, including various parameters:
Key Fields in the Message:
AMF UE NGAP ID – UE identifier within AMF
RAN UE NGAP ID – Identifier within the gNB
UE Aggregate Maximum Bit Rate – Total bit rate allowed for the UE
GUAMI (Globally Unique AMF Identifier) – Identifies the AMF instance
PDU Session Resource Setup Request List – Lists PDU Session IDs and related information
PDU Session ID – Identifier for the session
Tunnel Endpoint ID for uplink data
UE IP Address – Assigned during session setup
NAS-PDU – Contains the Registration Accept message
S-NSSAI (Single Network Slice Selection Assistance Information) – Helps with slice selection
Allowed NSSAI – Lists the network slices the UE can use
UE Security Capabilities – Shows supported algorithms
Security Key – Key derived for encryption and integrity protection
This request allows the gNB to establish both control plane (N2) and user plane (N3) resources for the UE.
gNB Actions After Receiving Initial Context Setup Request
When the gNB gets the Initial Context Setup Request, it will do several things:
Assign a RAN UE NGAP ID to uniquely identify the UE in the RAN.
Prepare the radio bearers (DRBs) using QoS and slice information.
Map RAN and Core network identifiers.
Send the Initial Context Setup Response back to the AMF (not shown in the diagram but part of the complete process).
This ensures that the UE context is set up in both RAN and Core, ready for secure communication and data flow.
Step 77: Security Mode Command
After the context is set up, the AMF needs to make sure communication with the UE is secure using the Security Mode Command (SMC).
Entity: gNB → UE (forwarded from AMF)
Message: Security Mode Command
Purpose:
To activate the security algorithms agreed upon for encryption and integrity protection of NAS and RRC signaling messages.
Key Parameters:
security Config SMC: Contains
security Algorithm Config: Specifies the selected encryption and integrity algorithms.
Kgnb (Security Key): Derived from the key hierarchy using KAMF.
The UE checks this command, implements the algorithms, and sends back a Security Mode Complete message (in the coming steps).
Importance of the Security Mode Command
The Security Mode Command (SMC) is vital because it makes sure all future communication between the UE and the network is safe from eavesdropping or tampering.
It activates two main mechanisms:
Ciphering (Encryption): Protects the confidentiality of messages.
Integrity Protection: Ensures message authenticity and prevents any modifications.
This is where the communication shifts from unsecured to secured signaling, safeguarding all NAS and RRC messages that follow.
Recap of the Signaling Flow
Step | Message / Action | Entities Involved | Purpose / Description
75 | Allocate AMF UE NGAP ID | AMF | Assign unique ID for UE context in AMF
76 | Initial Context Setup Request | AMF → gNB | Provide UE context, session, and security data
77 | Security Mode Command | gNB → UE | Activate encryption and integrity protection
Role of Each Component in Context Setup
AMF (Access and Mobility Management Function):
Allocates identifiers (AMF UE NGAP ID)
Supplies security keys and policies
Coordinates with SMF for PDU session resources
gNB (Next Generation NodeB):
Configures radio and bearer resources
Syncs UE identifiers and session data with the AMF
Implements QoS and slice information received
UE (User Equipment):
Receives the Registration Accept message
Uses the security algorithms as instructed
Starts secure NAS and RRC communication
Significance of the Initial Context Setup Procedure
This procedure is crucial during the 5G connection setup phase, ensuring:
Context Synchronization: The AMF and gNB keep identical UE contexts.
QoS and Slice Enforcement: Facilitates proper allocation of network resources.
Secure Signaling Activation: Guarantees protection for future communications.
Efficient Data Plane Activation: Sets up for immediate PDU session data exchange once security is established.
Conclusion
The 5G Initial Context Setup and Security Mode Command procedures connect the dots between registration and secure communication.
With awesome coordination among the AMF, gNB, and UE, the network allocates identifiers, sets up session resources, and enforces encryption.
These steps are essential for ensuring the reliability, security, and efficiency of the 5G network, allowing the UE to smoothly transition from accessing registration to full data connectivity.
For telecom professionals, getting a grip on these flows is super important for optimizing 5G RAN-Core integration, troubleshooting registration problems, and making sure network security compliance is up to snuff.
