5G NAS Authentication and Security Procedure Explained | Step-by-Step 5G Core Process

5G Standalone NAS Authentication and Security: A Step-by-Step Overview
In 5G Standalone (SA) networks, NAS Authentication and Security is key to making sure only legitimate users can access network services. After the User Equipment (UE) kicks off the registration and chats with the Access and Mobility Management Function (AMF), the Authentication and Key Agreement (AKA) process gets rolling.
This process is mainly handled by the AMF, the Authentication Server Function (AUSF), and the Unified Data Management (UDM) within the 5G Core (5GC).
Let’s dive into this phase in detail, using the signaling flow shown in the diagram.
Getting to Know NAS Authentication and Security in 5G
The NAS (Non-Access Stratum) layer takes care of communication between the UE and the 5G Core (5GC) when it comes to mobility and session management. In 5G, NAS authentication ensures:
Mutual authentication between the UE and the network
Integrity protection for control-plane messages
Generation of session encryption keys for secure communications
The 5G Authentication framework, outlined in 3GPP TS 33.501, builds on LTE by adding:
SUPI/SUCI for privacy protection
Flexible authentication methods (5G-AKA or EAP-AKA’)
A split between AUSF and UDM for better security management
High-Level Look at the NAS Authentication Flow
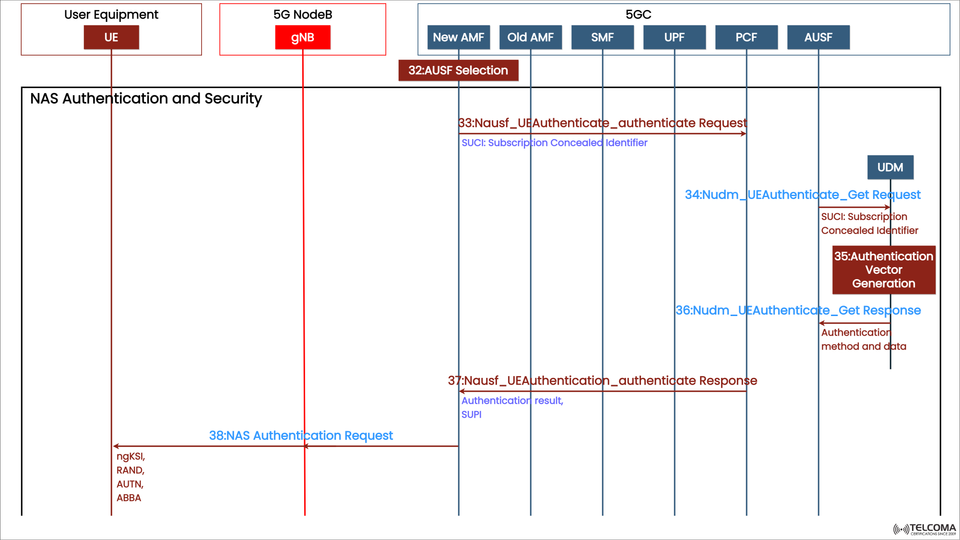
The NAS Authentication and Security procedure kicks off once the UE's identity (SUCI) has been confirmed. The steps in this flow are shown in the diagram:
Step Message/Procedure Direction Purpose
32 AUSF Selection
AMF Selects AUSF for authentication handling
33 Nausf_UEAuthenticate_authenticate Request
AMF → AUSF Sends SUCI to AUSF for authentication
34 Nudm_UEAuthenticate_Get Request
AUSF → UDM AUSF queries UDM for authentication data
35 Authentication Vector Generation
UDM Generates authentication vectors
36 Nudm_UEAuthenticate_Get Response
UDM → AUSF Returns authentication method and data
37 Nausf_UEAuthenticate_authenticate Response
AUSF → AMF Sends authentication result and SUPI
38 NAS Authentication Request
AMF → UE Sends authentication challenge to UE
Now, let’s break these steps down further.
Detailed Breakdown of 5G NAS Authentication Procedure
Step 32: AUSF Selection
After the AMF gets the UE context and the SUCI, it must pick the right AUSF.
AUSF Responsibilities:
Manages UE authentication logic
Works with the UDM to get subscriber data
Validates authentication vectors and responses
The AUSF is chosen based on the Serving Network ID (SNID) and Home PLMN (Public Land Mobile Network) info. This helps ensure authentication requests go to the right home network for each subscriber.
Step 33: Nausf_UEAuthenticate_authenticate Request
Once the AUSF is picked, the AMF starts the UE Authentication Request by sending a Nausf_UEAuthenticate_authenticate request to the AUSF.
Key Parameters in This Request:
SUCI (Subscription Concealed Identifier): This is an encrypted UE identifier derived from SUPI
Serving Network ID: This indicates which PLMN is serving the UE
Authentication method: This specifies whether to use 5G-AKA or EAP-AKA’
At this point, the AUSF doesn’t know the SUPI yet. The SUCI will need to be decrypted by the UDM in the next steps.
Step 34: Nudm_UEAuthenticate_Get Request
After the AUSF receives the authentication request, it reaches out to the UDM using a Nudm_UEAuthenticate_Get request.
Purpose:
To grab authentication vectors and subscriber security data.
To send the SUCI to the UDM for decryption.
The UDM deploys its internal key management system to pull the actual subscriber identity, SUPI, from the SUCI with the Home PLMN’s private key.
Step 35: Authentication Vector Generation
Once the UDM retrieves the SUPI, it prompts the Authentication Credential Repository and Processing Function (ARPF) to create authentication vectors.
Each authentication vector (AV) contains:
Field Description
RAND Random challenge generated by the network
AUTN Authentication token for network validation
XRES* Expected response for verification
K_AUSF Key for future NAS and AS security
ABBA Anti-bidding down parameter for algorithm protection
The vector ensures mutual authentication, meaning both the network and UE confirm each other's legitimacy.
Step 36: Nu dm _ UE Authenticate _Get Response
The UDM sends the authentication vectors back to the AUSF via a Nu dm _UE Authenticate _Get Response message.
Response Includes:
Authentication method (5G-AKA or EAP-AKA’)
RAND, AUTN, XRES, K_AUSF, and ABBA parameters
With this info, the AUSF can validate the UE’s response later and give the AMF the necessary challenge parameters.
Step 37: Na us f _ UE Authenticate _ authenticate Response
Now that the AUSF has the authentication info from the UDM, it processes this data and sends a Na us f_ UE Authenticate _ authenticate Response message back to the AMF.
This message contains:
SUPI (derived from SUCI after decryption)
Authentication result (pending verification)
Authentication vector data for generating the challenge
The AUSF also keeps the XRES* for later verification once the UE sends back its authentication response.
Step 38: NAS Authentication Request
Next, the AMF starts the NAS Authentication Request toward the UE.
The message includes:
ngKSI (NAS Key Set Identifier) – Identifies the key set in use.
RAND – Random number for challenge.
AUTN – Authentication token from the network.
ABBA – Used to prevent algorithm downgrading.
When the UE gets this message, it takes the following steps:
Uses its stored authentication key (K) to verify AUTN.
Computes its response (RES*).
Sends a NAS Authentication Response back to the AMF.
If RES* matches the XRES* at the AUSF, the UE is successfully authenticated.
AUSF and UDM’s Role in 5G Security
The AUSF and UDM play pivotal roles in the 5G security framework:
Component Function
AUSF (Authentication Server Function) Manages authentication logic, interacts with AMF and UDM, validates UE responses.
UDM (Unified Data Management) Stores subscriber data, decrypts SUCI to get SUPI, and generates authentication vectors through ARPF.
Their collaboration ensures a secure and privacy-preserving authentication process that aligns with 5G security architecture.
Security Features in NAS Authentication
The 5G NAS Authentication phase brings in several enhanced security features compared to LTE:
SUCI-based Identity Protection: Keeps subscribers’ identities safe from IMSI catching through encryption.
Mutual Authentication: Both the UE and the network check each other’s validity.
K_AUSF Derivation: Enables the generation of subsequent keys for NAS and AS layers.
Algorithm Negotiation Protection (ABBA): Blocks downgrade attacks.
Network Slice Awareness: Links authentication with a specific network slice or NSSAI.
These upgrades ensure that 5G adheres to strict privacy and cybersecurity standards.
Common Authentication Methods: 5G-AKA and EAP-AKA’
5G includes two main authentication methods:
Method Description Used In
5G-AKA Derived from LTE-AKA with a new key hierarchy; uses K_AUSF. Mobile operators with SIM-based authentication.
EAP-AKA’ Uses the Extensible Authentication Protocol; allows Wi-Fi or non-3GPP access integration. Non-3GPP or hybrid networks.
The AUSF picks the method dynamically based on subscriber and network setup.
Quick Look at Key Parameters
Parameter Meaning
SUCI Subscription Concealed Identifier for privacy.
SUPI Subscription Permanent Identifier, decrypted by UDM.
RAND Random challenge sent by the network.
AUTN Authentication token that ensures network authenticity.
XRES, Expected response used by AUSF for validation.
RES, UE’s calculated response to the authentication challenge.
K_AUSF Master key for future NAS and AS security.
ABBA Parameter for anti-bidding down algorithm protection.
Why NAS Authentication is Key in 5G
The NAS authentication phase is the security backbone of the 5G registration process. It ensures that:
Only authorized devices can connect to the network.
Subscriber data stays private and encrypted.
All future communications (NAS and AS layers) are integrity protected.
Without this layer of trust, later procedures like session establishment, PDU setup, and mobility management could face vulnerabilities.
Conclusion
The 5G NAS Authentication and Security process is crucial to the 5G Standalone architecture. By combining AUSF selection, SUCI decryption, and mutual authentication, the network guarantees secure, privacy-respecting registration.
With advancements like 5G-AKA, EAP-AKA’, and K_AUSF key hierarchies, 5G delivers strong security and builds subscriber trust like never before.
For telecom engineers and enthusiasts, getting a grip on this stage is key to understanding how 5G protects user identity, data integrity, and network reliability.
