5G NAS Authentication and Security Procedure Explained: Step-by-Step Message Flow

5G NAS Authentication and Security: A Step-by-Step Breakdown
In the 5G Standalone (SA) setup, keeping things secure is a major focus. Before any data session kicks off, the User Equipment (UE) has to verify its identity to the network. This involves a series of authentication and key agreement processes managed by the Access and Mobility Management Function (AMF) and the Authentication Server Function (AUSF) located in the 5G Core (5GC).
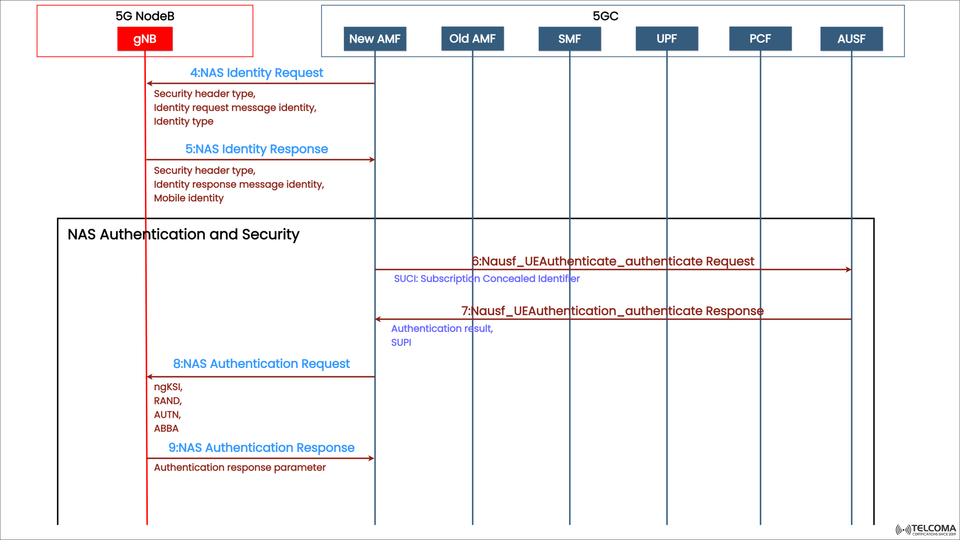
The diagram above shows the flow of NAS Authentication and Security messages, illustrating how the UE and network build mutual trust and generate encryption keys for secure communication.
Let’s take a closer look at the steps involved in this vital 5G operation.
Overview: The Importance of NAS Authentication in 5G
The Non-Access Stratum (NAS) is the protocol layer that handles signaling between the UE and the AMF. It operates above the Access Stratum (AS), which deals with the radio and transport aspects.
The main objectives of NAS Authentication and Security are:
Authenticate the UE with the 5G Core Network.
Generate security keys for integrity protection and encryption.
Prevent impersonation attacks or repeated registration attempts.
Ensure mutual authentication between the network and the UE.
In short, it confirms that both the subscriber and the network are legitimate before any service or session begins.
Key Network Entities Involved
Entity Function in NAS Authentication UE (User Equipment)Kicks off registration and provides identification for authentication .gNB (5G Node B)Acts as an intermediary between the UE and the 5G Core. AMF (Access and Mobility Management Function)Manages NAS messages and initiates authentication. AUSF (Authentication Server Function)Runs the authentication algorithm and checks subscriber credentials. UDM/ARPF (User Data Management / Authentication Credential Repository and Processing Function)Keeps authentication vectors and subscriber data (indirectly used by AUSF).
Detailed Steps of the 5G NAS Authentication Process
Step 4: NAS Identity Request
Direction: AMF → UE (via gNB)
After the AMF receives the NAS Registration Request, it might not have enough info to uniquely identify the UE. So, it sends a NAS Identity Request to the UE to get its permanent or concealed identity.
Message Content:
Security Header Type – Indicates if the message is plain or integrity protected.
Identity Request Message Identity – Shows this is an identity request.
Identity Type – Specifies the identity type being requested (SUCI, GUTI, IMEI, or IMEISV).
Purpose:
To gather the subscriber identity needed for authentication and retrieving subscription info.
Step 5: NAS Identity Response
Direction: UE → AMF (via gNB)
In reply, the UE sends back its Mobile Identity. In the realm of 5G, this is usually the SUCI (Subscription Concealed Identifier) — a privacy-enhanced take on the subscriber’s permanent identity, which is known as the SUPI (Subscription Permanent Identifier).
Message Content:
Security Header Type – Either plain or integrity protected.
Identity Response Message Identity – Indicates the type of response message.
Mobile Identity – Either SUCI or GUTI.
Key Concept:
The SUCI encrypts the SUPI using the operator's public key, which means that if someone intercepts it, the permanent identity stays secure. This helps protect user privacy — a big step up from 4G systems.
Step 6: Authentication Request to AUSF
Direction: AMF → AUSF
Once the AMF gets the SUCI, it sends an authentication request to the AUSF using the Nau sf _UE Authenticate service interface.
Message Content:
SUCI – Subscription Concealed Identifier.
Serving Network ID – Identifies the network asking for authentication.
Requested Authentication Method – Either EAP-AKA’ or 5G-AKA.
Purpose:
The AUSF takes this request and sends it to the UDM/ARPF, which produces an authentication vector (AV) that includes:
RAND (Random Challenge)
AUTN (Authentication Token)
XRES* (Expected Response)
K_SEAF (Key for the security anchor function)
This vector helps validate the subscriber and derive session security keys.
Step 7: Authentication Response from AUSF
Direction: AUSF → AMF
After checking the subscriber's credentials, the AUSF sends back the authentication result to the AMF.
Message Content:
Authentication Result – Shows if it succeeded or failed.
SUPI – The permanent subscriber identifier (decrypted from SUCI).
If everything checks out, the AMF receives the authentication vectors and gets ready to send them to the UE for challenge-response verification.
Step 8: NAS Authentication Request
Direction: AMF → UE (via gNB)
The AMF then sends the NAS Authentication Request message to challenge the UE.
Message Content:
ngKSI (NAS Key Set Identifier) – Identifies the key set for security association.
RAND – The random number for the challenge.
AUTN – The authentication token created by the network.
ABBA – Extra security parameters (Anti-Bidding-Down mechanism).
Purpose:
To challenge the UE and confirm it has the right credentials and key material to produce a valid response.
Step 9: NAS Authentication Response
Direction: UE → AMF (via gNB)
Once the UE gets the challenge, it calculates a response using its USIM (Universal Subscriber Identity Module) and sends the NAS Authentication Response message back to the AMF.
Message Content:
Authentication Response Parameter – The UE’s calculated response (RES).
The AMF will compare this RES with the XRES* it got from the AUSF. If they match, the authentication is successful, and both sides can derive shared keys for NAS and AS security setup.
Summary of Message Flow
Step Message Direction Key Function4NAS Identity Request AMF → UE Request subscriber identity5NAS Identity Response UE → AMF Provide SUCI (concealed SUPI)6Nausf_UEAuthenticate_authenticate Request AMF → AUSFT rigger authentication vector generation7Nausf_UEAuthenticate_authenticate Response AUSF → AMF Return authentication vectors and SUPI8NAS Authentication Request AMF → UE Challenge the UE9NAS Authentication Response UE → AMF Provide authentication result
Enhancements in 5G Authentication Security
5G brings along various innovations to boost security compared to LTE/4G:
SUCI & SUPI Privacy: Safeguards subscriber identity through encryption.
Mutual Authentication: Both UE and network authenticate one another.
Key Hierarchy: Generates separate keys for NAS and AS (K_AMF, K_gNB).
Improved Integrity & Confidentiality: Ensures protection for signaling and data.
EAP-AKA’ Support: Enables authentication for non-3GPP access (like Wi-Fi).
These measures make 5G more robust against interception, spoofing, and identity theft.
Authentication Algorithms: 5G-AKA vs. EAP-AKA’
Feature5G-AKAEAP-AKA’Used For3GPP access (NR/NG-RAN)Non-3GPP access (Wi-Fi, untrusted networks)Authentication Server AUSFAUSF + EAP Server Key Derivation K_ SEAF, K_AMFEAP-derived keys SUPI Protection SUCI encryption SUCI encryption Primary Focus SIM-based 3GPP devices Wi-Fi or offloaded devices
Both methods share similar principles but differ in how they’re deployed and handle keys.
Common Challenges and Troubleshooting Strategies
Identity Mismatch (SUCI/SUPI): Confirm that the UE’s SUCI encryption and AMF decryption keys match.
Authentication Failure: Make sure the RAND or AUTN values were correctly received and processed by the UE.
AUSF Timeout: Check UDM connectivity and authentication vector retrieval from the ARPF.
NAS Message Integrity Problems: Ensure security header fields are correctly set up at the AMF.
For engineers, looking through NAS traces and AUSF logs can provide crucial insights into issues during authentication testing.
A Real-World Example
Imagine a UE powering up in a 5G SA network for the first time:
The AMF asks for identity and receives the SUCI from the UE.
The AUSF authenticates the subscriber through the UDM and sends back authentication vectors.
The UE successfully responds to the challenge, establishing secure NAS keys.
After that, all signaling — like registration and session setup — is encrypted and has integrity protection.
This entire process ensures that only authorized users can access network resources while preserving confidentiality and trust in the 5G framework.
The Advantages of NAS Authentication and Security
Privacy Protection: No exposure of permanent identifiers.
End-to-End Integrity: Safeguards all control-plane messages.
Mutual Verification: Helps stop fake network attacks.
Scalable Design: Capable of managing millions of secure UE registrations.
Multi-Access Functionality: Works well for both 3GPP and non-3GPP access.
Conclusion
The 5G NAS Authentication and Security procedure is vital for maintaining the integrity of 5G networks. With thoughtfully crafted message exchanges among the UE, AMF, and AUSF, it guarantees that every subscriber and network element is securely verified before any communication starts.
Thanks to SUCI-based privacy, mutual authentication, and strong key derivation methods, 5G significantly boosts trust and privacy measures compared to LTE.
For telecom experts, mastering this flow is key to understanding how 5G secures user identities, prevents fraud, and lays the groundwork for all future secure signaling and data transfers in the network.
