5G NAS Authentication and Security Procedures Explained: Step-by-Step Analysis

Explaining 5G NAS Authentication and Security Procedures
A key part of the 5G Standalone (SA) architecture revolves around authentication and security. When a User Equipment (UE) kicks off its registration and identity verification, it must undergo NAS Authentication and Security procedures.
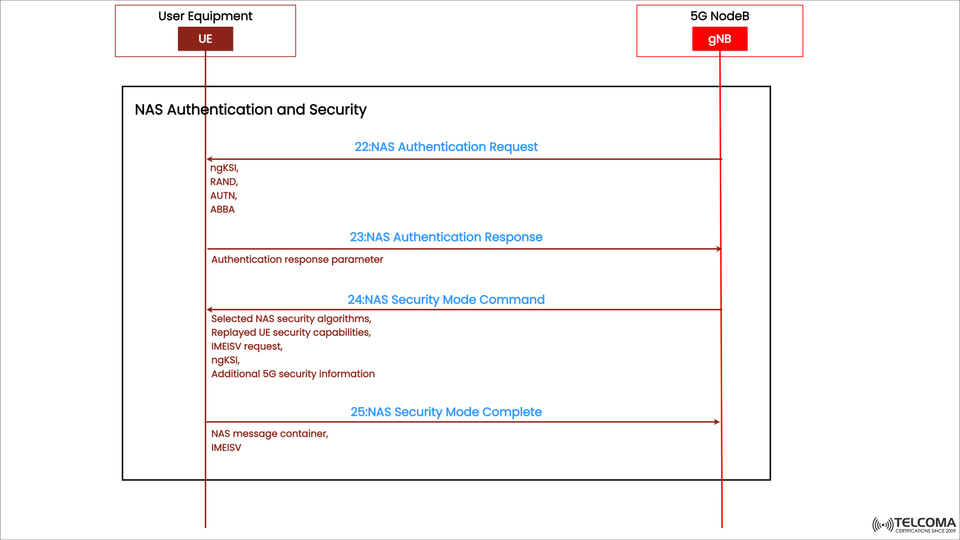
These processes confirm the identities of both the UE and the 5G Core Network (5GC), making sure that only genuine devices and trusted networks engage in sharing sensitive information. The diagram provided shows the interaction between the UE and the gNB (5G NodeB), highlighting important NAS messages like Authentication Request, Authentication Response, Security Mode Command, and Security Mode Complete.
NAS Authentication’s Role in 5G
The Non-Access Stratum (NAS) layer handles the signaling between the UE and the AMF (Access and Mobility Management Function) in the 5G Core.
The NAS authentication serves several purposes:
It verifies the subscriber’s identity using credentials from the USIM (Universal Subscriber Identity Module).
It confirms that the network is legitimate, blocking unauthorized or fake base stations.
It creates security keys for encrypting and protecting the integrity of the signaling and data.
This mutual authentication relies on either 5G-AKA (Authentication and Key Agreement) or EAP-AKA′ (Extensible Authentication Protocol), depending on what the operator has set up.
Overview of NAS Authentication and Security Steps
The diagram outlines four crucial messages exchanged between the UE and gNB (which eventually reaches the AMF in the core):
Step Message Direction Purpose
22NAS Authentication Request Network → UE Starts mutual authentication using a challenge-response method.
23NAS Authentication Response UE → Network UE proves its legitimacy by sending back the correct authentication token.
24NAS Security Mode Command Network → UE Network specifies encryption/integrity algorithms to secure NAS signaling.
25NAS Security Mode Complete UE → Network UE confirms that the NAS security context is active.
Step 22: NAS Authentication Request
Message: NAS Authentication Request
Direction: 5G Core (via gNB) → UE
The NAS Authentication Request kicks off the mutual authentication process between the UE and the network.
This message carries a few essential parameters:
ngKSI (NAS Key Set Identifier): Identifies the security key set in use.
RAND (Random Challenge): A random number created by the network to check the UE’s authenticity.
AUTN (Authentication Token): A token generated by the network for the UE to confirm the network’s legitimacy.
ABBA (Anti-Bidding Down Algorithm): Ensures that both the UE and the network agree on the most secure encryption algorithms available.
When the UE gets this message, it carries out a few actions:
Verifies the AUTN using the stored key in its USIM.
If the AUTN checks out, the UE knows it's communicating with a legit network.
The UE calculates a response parameter (RES*) to send back to the network in the next step.
If authentication fails, the UE will halt the process to avoid unauthorized access.
Step 23: NAS Authentication Response
Message: NAS Authentication Response
Direction: UE → 5G Core (via gNB)
After the UE successfully verifies the AUTN, it creates an Authentication Response Parameter, known as RES* (Response Star).
Key Technical Details:
The RES*** is derived from the RAND value and the shared key **K stored in the USIM.
The network checks the RES* against its expected XRES* (Expected Response).
If they match, mutual authentication is deemed successful.
This step verifies that the UE is the legitimate subscriber it claims to be.
Step 24: NAS Security Mode Command
Message: NAS Security Mode Command
Direction: Network → UE
Once authentication goes through, the 5G Core (via the AMF) sends the Security Mode Command to set up encryption and integrity protection for all subsequent NAS messages.
This message includes:
Selected NAS security algorithms (for encryption and integrity).
Replayed UE security capabilities (to guard against downgrade attacks).
IMEISV request (International Mobile Equipment Identity and Software Version).
ngKSI (NAS Key Set Identifier).
Additional 5G security details, including options for stronger encryption.
Security Algorithms in Use
The Security Mode Command details the following algorithm pairs:
Integrity Protection Algorithms (IA): Such as 128-5G-IA1, 128-5G-IA2.
Ciphering Algorithms (EA): Such as 128-5G-EA1, 128-5G-EA2.
Both the UE and the network need to support the chosen algorithms for this process to carry on.
This ensures all future NAS messages sent back and forth are encrypted (for confidentiality) and integrity-protected (to ensure authenticity), preventing tampering and interception.
Step 25: NAS Security Mode Complete
Message: NAS Security Mode Complete
Direction: UE → Network
The last step in this phase is the NAS Security Mode Complete message, which the UE sends to confirm that the selected NAS security context is now in place.
Typically, this message will contain:
NAS message container: Could include an embedded NAS message for further registration or service requests.
IMEISV (International Mobile Equipment Identity and Software Version): Sent if requested in the Security Mode Command.
Once received by the network, it assumes that the UE and AMF now share the same encryption and integrity keys. From here on out, all NAS messages will utilize this established security context.
How the 5G NAS Security Framework Functions
To get a clearer picture of how things work, let’s consider the key hierarchy and security contexts involved.
5G Key Hierarchy:
K (Master Key): Stored securely in the USIM.
K_AMF: Created during authentication, unique to each session.
K_NASenc & K_NASint: Derived from K_AMF, used for NAS encryption and integrity.
K_gNB: Generated later for RRC and user-plane encryption.
This layered structure keeps each session separate, making it harder for attackers to reuse old session keys.
Mutual Authentication:
The UE checks the network’s authenticity using AUTN.
The network verifies the UE through a RES* vs XRES* comparison.
Both parties create matching K_AMF, ensuring synchronized encryption contexts.
Conclusion
The NAS Authentication and Security process forms the backbone of 5G security, ensuring trust and privacy between the UE and the network.
Through a series of challenge-response exchanges and algorithm negotiations, both sides achieve mutual authentication and derive encryption keys for future communication.
Implementing measures like ABBA protection, mutual verification, and per-session key derivation means 5G offers remarkable resilience against impersonation, eavesdropping, and replay attacks.
In short, these procedures don’t just make 5G faster and more reliable—they also make it much more secure than earlier technologies.
