5G-NR AS Security Procedure Explained: From Initial Context Setup to Security Mode Complete

Getting to Grips with the 5G-NR AS Security Procedure: A Step-by-Step Message Flow
Once the NAS (Non-Access Stratum) authentication and security setup between the UE (User Equipment) and AMF (Access and Mobility Management Function) is complete, the next vital step focuses on securing the Access Stratum (AS) — essentially the radio connection between the UE and the 5G NodeB (gNB).
The 5G-NR AS Security Procedure is all about making sure that any RRC (Radio Resource Control) and user-plane data sent over the air is both encrypted and has integrity protection. This setup safeguards user communications against any potential interception or manipulation over the radio link.
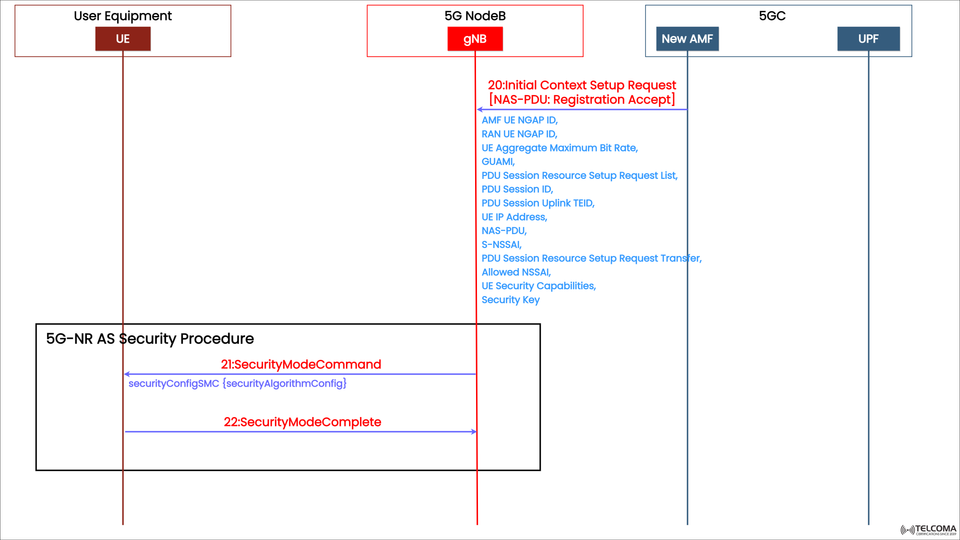
The image above illustrates where the AS Security Procedure fits into the larger 5G signaling process, starting off with the Initial Context Setup Request and moving through the Security Mode Command and Security Mode Complete messages.
Overview of the 5G-NR AS Security Procedure
The 5G-NR AS Security Procedure kicks into gear after successfully establishing NAS-level security (between the UE and AMF). At this point, the AMF hands over a Security Key along with other parameters to the gNB to start the RRC-level protection.
Here’s what this security stage ensures:
The encryption of user data and signaling messages.
Protection of RRC messages through integrity checks.
Keeping the radio connection between the UE and gNB confidential.
Securely exchanging session parameters like PDU session identifiers and security capabilities.
Who’s Involved in the Procedure?
Entity Role UE (User Equipment)The device that starts and confirms the security setup. gNB (5G NodeB)The 5G base station that ensures radio link security and resource configuration. AMF (Access and Mobility Management Function)Supplies the gNB with necessary security keys and UE context through the Initial Context Setup Request. UPF (User Plane Function)Manages user data forwarding but isn’t directly involved in AS security setup.
The Step-by-Step Flow of the 5G-NR AS Security Procedure
The image lays out three main steps:
Step 1: Initial Context Setup Request (Message 20)
Direction: AMF → gNB
Before AS security can kick in, the AMF sends an Initial Context Setup Request to the gNB. This message brings essential context and security parameters that the gNB will rely on to communicate securely with the UE.
The message includes:
AMF UE NGAP ID and RAN UE NGAP ID – unique IDs for the UE at the AMF and gNB.
UE Aggregate Maximum Bit Rate – maximum throughput allowed for the UE.
GUAMI – Globally Unique AMF Identifier.
PDU Session Resource Setup Request List – details specific to the session setup.
PDU Session ID and Uplink TEID – identifiers for user-plane data sessions.
UE IP Address – the IP assigned to the UE.
NAS-PDU (Registration Accept) – NAS message wrapped up for the UE.
S-NSSAI – Single Network Slice Selection Assistance Information.
Allowed NSSAI – the network slices the UE can use.
UE Security Capabilities – supported ciphering and integrity algorithms list.
Security Key – a key derived from NAS for the gNB to create AS security keys.
👉 Purpose:
This message sets up the UE’s context in the gNB and provides the necessary security materials to kick off the RRC-level security setup.
Step 2: Security Mode Command (Message 21)
Direction: gNB → UE
Once the Initial Context Setup is in place, the gNB sends a Security Mode Command (SMC) to the UE to activate the AS security.
The Security Mode Command features:
security Config SMC {security Algorithm Config} – outlines which ciphering and integrity algorithms will be utilized for RRC and user-plane traffic.
Common algorithms include:
Ciphering: NEA0, NEA1, NEA2, NEA3 (AES and Snow3G-based)
Integrity: NIA1, NIA2, NIA3
Process:
The gNB picks the algorithms based on what the UE can support (shared during NAS registration).
It derives the KeNB or KgNB key from the NAS-level key (K_AMF).
The gNB tells the UE to employ these algorithms for encryption and integrity checks.
👉 Purpose:
To set security settings and activate ciphering and integrity protection for the radio link between the UE and gNB.
Step 3: Security Mode Complete (Message 22)
Direction: UE → gNB
Once the UE has successfully set up the requested algorithms and security keys, it sends back a Security Mode Complete message.
This message confirms:
The UE has implemented the requested ciphering and integrity configurations.
Secure RRC communication can now kick off.
After this step:
All RRC and user-plane messages are encrypted and integrity protected.
The UE and gNB now share an AS security context, ensuring confidentiality over the air interface.
Security Key Derivation in 5G-NR
5G brings a hierarchical key derivation system to make sure that each layer (NAS and AS) has its own independent and securely generated keys.
Key Hierarchy:
K → Permanent key in USIM.
K_AUSF → Derived during authentication at the core.
K_SEAF → Shared between AMF and UE.
K_AMF → Used by AMF to derive access stratum keys.
K_gNB → Generated by gNB to secure radio link communications.
This separation means that if one layer’s key gets compromised, the others still stay safe.
The Relationship Between NAS and AS Security
Aspect NAS Security AS Security Scope Between UE and AMF Between UE and gNB Protection NAS signaling (control plane)RRC signaling and user-plane data Key Source K_ SEAF derived during authentication K _g NB derived from K_ MF Algorithms NI Ax, NEAx (for NAS)NI Ax, NE Ax (for AS)Activation Message NAS Security Mode Command RRC Security Mode Command
👉 NAS security safeguards core signaling, while AS security shields the radio access layer. Both are crucial for comprehensive 5G security.
Advantages of the 5G-NR AS Security Procedure
🔒 Strong Air-Interface Protection: Keeps eavesdropping and spoofing at bay on the radio channel.
⚡ Streamlined Key Management: Employs hierarchical key derivation for independent NAS and AS layers.
📡 Flexible Algorithm Selection: Adjusts ciphering and integrity algorithms based on what the UE can handle.
🧩 Layered Security Model: Splits protection between core (NAS) and RAN (AS) layers for added security.
🛡️ Establishes Mutual Trust: Guarantees both gNB and UE utilize compatible security settings.
Common Troubleshooting Issues
Security Mode Reject: Happens if the UE can’t handle the chosen algorithms.
Integrity Check Failure: Could be due to mismatched keys or tampered messages.
RRC Reconfiguration Problems: If AS security isn’t activated correctly, the UE may lose the connection.
Sync Errors: When NAS and AS keys aren’t in sync from improper key derivation.
Tip for Engineers:
Always check the UE Security Capabilities and ensure the NAS-to-AS key derivation adheres to 3GPP-defined algorithms (TS 33.501).
Summary of Message Flow
StepMessageDirectionDescription20Initial Context Setup Request AMF → gNB Sends UE context, security key, and session details.21Security Mode Command g NB → UE Configures encryption and integrity algorithms.22Security Mode Complete UE → gNB Confirms that AS security is activated.
Conclusion
The 5G-NR AS Security Procedure is absolutely essential for the overall security framework of 5G. It guarantees that all communications through the radio interface are encrypted and maintained with integrity, building on the trust established during NAS authentication.
By creating separate NAS and AS security layers, 5G networks form a multi-layer defense model that boosts confidentiality, integrity, and resilience. For those working in telecom, mastering this procedure is key to securing network operations and delivering reliable services.
As the 5G landscape evolves, getting a solid grasp of how the AS Security Mode Command and Security Mode Complete messages function will be vital for optimizing performance and ensuring strong security at the radio layer.
