5G SA Security Overview: 3GPP SBA, API Security, and Multi-Domain Operations
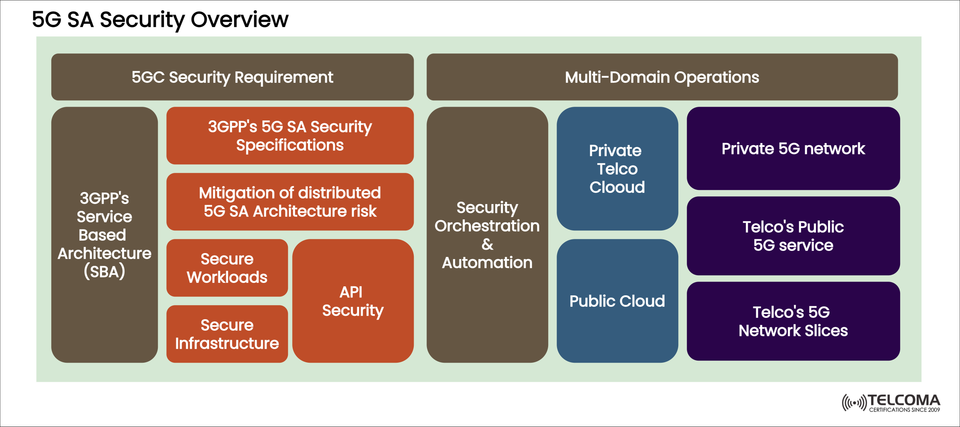

The move to 5G Standalone (SA) is a big step forward for mobile networks. Unlike Non-Standalone (NSA) setups that depend on LTE for control signaling, 5G SA brings in a native 5G Core (5GC) designed around 3GPP’s Service-Based Architecture (SBA).
This new architecture offers advantages like low latency, network slicing, and private 5G networks, but it also comes with new security challenges. To safeguard the 5GC, we need to tackle issues like API exposure, distributed workloads, and multi-domain environments, where public, private, and telco clouds overlap.
The diagram uploaded—5G SA Security Overview—highlights how telecom operators and businesses can secure 5G SA deployments across these areas. Let’s take a closer look.
5GC Security Requirements
The 5G Core (5GC) brings new functions and service-based interfaces that need to meet the 3GPP-defined security specifications.
Here are some key requirements:
3GPP’s 5G SA Security Specs: * Outlines authentication, encryption, and integrity protection for the 5G Core. * Includes security mechanisms for SBA, like service authorization, access tokens, and TLS.
Managing Distributed 5G SA Risks: * With 5GC functions spread across cloud-native setups, attack surfaces expand due to virtualization, containerization, and cloud APIs. * Operators should implement zero-trust architectures and real-time threat detection.
Secure Workloads: * Network functions (VNFs and CNFs) need to be strengthened against malware injection or privilege escalation. * Managing the secure lifecycle—from deployment to updates—is crucial.
Secure Infrastructure: * The 5G infrastructure runs on cloud-native platforms (like Kubernetes, OpenStack, etc.). * It's vital to ensure hardware root of trust, secure boot, and encrypted communications.
API Security: * SBA heavily relies on APIs for interactions between 5GC functions (AMF, SMF, PCF, UPF, etc.). * APIs need protection against threats like DDoS attacks, replay attacks, token theft, and configuration mistakes. * Key defenses involve API gateways, rate limiting, and strong authentication.
3GPP’s Service-Based Architecture (SBA)
At the core of 5G SA is the Service-Based Architecture (SBA):
Functions like AMF (Access and Mobility Management Function), SMF (Session Management Function), and UPF (User Plane Function) expose services through HTTP/2 APIs.
Unlike LTE’s point-to-point design, SBA is flexible, scalable, and cloud-native.
While this openness provides power, it also adds vulnerability.
Security Implications of SBA:
APIs should enforce mutual TLS and OAuth-based service authorization.
Ongoing monitoring for API traffic anomalies is essential for intrusion detection.
Operators must comply with 3GPP TS 33.501, which sets the rules for 5G security.
Security Orchestration and Automation
Securing a distributed 5G Core requires more than just static rules—it calls for automation and orchestration.
Security Orchestration: * Provides centralized control for deploying and enforcing policies across various domains. * It automates workload isolation, intrusion detection, and compliance checks.
Automation: * Utilizes AI/ML to identify real-time anomalies in traffic patterns. * Allows for self-healing responses, like scaling resources under DDoS or isolating compromised nodes.
Integration with DevSecOps: * Security should be part of the CI/CD pipeline for CNFs and VNFs. * This ensures that vulnerabilities are consistently patched.
Multi-Domain Operations
5G SA deployments span various environments:
- Private Telco Cloud
This is dedicated infrastructure for operators’ core networks.
It provides better control and compliance.
Nonetheless, it remains open to insider threats and misconfigurations.
- Public Cloud
Operators are increasingly using AWS, Azure, or Google Cloud for 5GC functions.
Pros: scalability, flexibility, and quicker rollouts.
Cons: reliance on cloud providers and potential risks from shared infrastructure vulnerabilities.
- Private 5G Network
Businesses are setting up dedicated 5G SA networks for places like factories, hospitals, and airports.
Security here must tackle industrial IoT threats, such as device spoofing and unauthorized lateral movement within the network.
- Telco’s Public 5G Service
This includes consumer-facing 5G SA services offered by mobile network operators (MNOs).
They need to securely support billions of subscribers with solid authentication and lawful interception measures.
- Telco’s 5G Network Slices
Network slicing allows the division of 5G infrastructure into virtual networks.
Each slice can have its own security protocols.
Risks involve slice isolation breaches and attacks that cross slice boundaries.
Security Challenges in Multi-Domain Operations:
Consistently maintaining security across hybrid clouds.
Ensuring slice isolation while sharing infrastructure.
Adapting to regulatory differences in various regions.
Key Security Challenges in 5G SA
Here are the main security issues operators need to address:
Expanded Attack Surface: APIs, cloud-native workloads, and distributed nodes heighten vulnerability.
Supply Chain Risks: Engaging third-party cloud and software vendors opens new doors for risk.
DDoS Attacks: The high bandwidth of 5G makes it a prime target for large-scale denial-of-service attacks.
IoT Device Security: With billions of connected devices, there’s a risk of exploitation for botnets or espionage.
Slice Security: Network slices must stay isolated to stop breaches from spreading.
Comparison: 4G vs 5G SA Security
Feature4G LTE EPC Security5G SA Security (5GC + SBA)Core Architecture Point-to-point Service-Based Architecture APIs Limited Extensive (HTTP/2 APIs)Virtualization Partial (VNFs)Cloud-native (CNFs, VNFs)Multi-Domain Ops Mostly private telco cloud Public, private, hybrid Security Complexity Medium High (multi-domain + SBA)Network Slicing Not supported Supported, requires isolation
Best Practices for Securing 5G SA
To secure 5G SA deployments, telecom operators should consider:
Zero Trust Security Model: No implicit trust—always verify.
API Security Gateways: Safeguard SBA APIs with robust authentication and rate limiting.
End-to-End Encryption: Protect both signaling and user plane traffic.
Slice-Aware Security: Isolate slices with specific security measures.
Cloud-Native Security: Secure containers, orchestration layers (like Kubernetes), and CI/CD pipelines.
AI/ML-based Monitoring: Identify anomalies in real-time traffic.
Regular Compliance Audits: Align with 3GPP TS 33.501 and local regulatory standards.
Conclusion
The 5G Standalone Core (5GC) offers groundbreaking capabilities through its Service-Based Architecture (SBA), cloud-native design, and multi-domain operations. But these advancements also bring new challenges in API security, workload protection, and slice isolation.
Operators need to adopt 3GPP’s security specifications, embrace automation and orchestration, and ensure consistent protections across public, private, and hybrid cloud domains.
Securing 5G SA isn't just a one-off task—it's an ongoing, adaptive process that blends compliance with evolving standards, AI-driven monitoring, and a zero-trust strategy. By rising to these challenges, telecom providers can deliver secure and reliable 5G services for both their business partners and end-users.
