5G Security Architecture Explained: Authentication, Virtualization, and Monitoring

With 5G networks rolling out, security is more important than ever. Unlike earlier versions, 5G connects everything from smartphones to IoT devices, self-driving cars, industrial systems, and essential services. This huge expansion in connectivity needs a strong and layered security setup that covers authentication, encryption, virtualization, and monitoring.
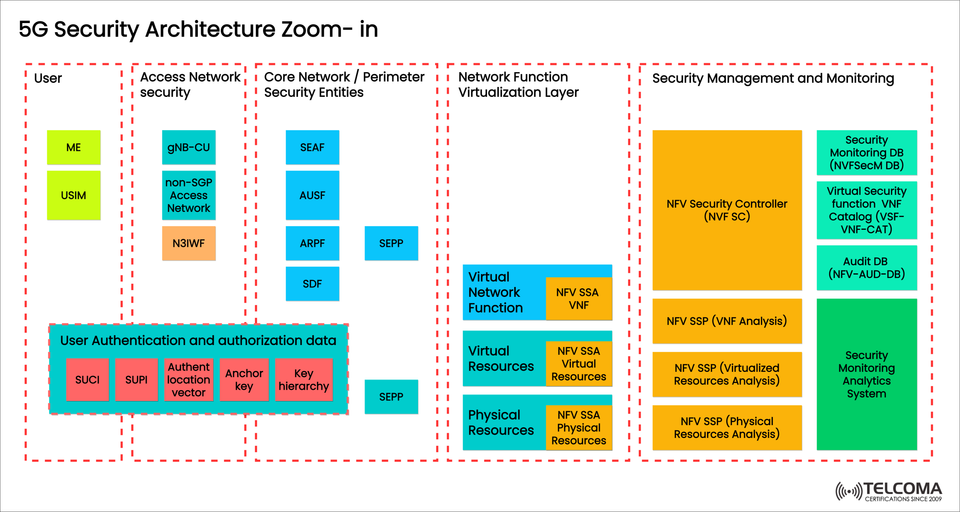
The image I uploaded shows a zoomed-in look at the 5G Security Architecture, breaking down the various functional areas: User, Access Network Security, Core Network Security Entities, Network Function Virtualization (NFV) Layer, and Security Management & Monitoring.
In this article, we’ll dive into these components and explain how they work together to keep 5G networks secure.
Why 5G Security Matters
Compared to 4G/LTE, 5G brings in some important changes:
Networks are more decentralized and virtualized, moving away from old hardware-based setups.
We're seeing critical applications like smart cities, healthcare, and self-driving transport, where even a small security breach can lead to serious issues.
There’s a massive growth in IoT devices, which adds to the potential attack surface.
So, the 5G security setup is built around end-to-end protection, zero-trust principles, and strong encryption.
Core Components of 5G Security Architecture
The 5G Security Architecture is made up of five main sections, each focusing on different aspects of trust, identity, and protection.
- User Layer Security
On the user side, there are two crucial components:
ME (Mobile Equipment): This refers to the actual device, like a smartphone, IoT device, or sensor.
USIM (Universal Subscriber Identity Module): This stores vital security credentials and helps with secure authentication.
These components work with the network to start authentication and make sure only legitimate users and devices can access it.
User Authentication and Authorization Data includes:
SUCI (Subscription Concealed Identifier): Keeps the user’s identity safe during transmission.
SUPI (Subscription Permanent Identifier): A unique ID for every subscriber.
Authentication Vectors: Cryptographic elements for verifying the subscriber.
Anchor Keys & Key Hierarchy: Ensure smooth session continuity and safe transitions between access points.
- Access Network Security
The access network is the first spot where user devices connect and includes:
gNB-CU (gNodeB Central Unit): Manages security functions at the radio layer.
Non-3GPP Access Network: Allows connection via Wi-Fi, satellite, or unlicensed spectrum while keeping security intact.
N3IWF (Non-3GPP Interworking Function): Ensures secure connectivity for devices connecting over untrusted networks.
These elements work together to ensure secure radio communication and keep unauthorized devices from attaching to the network.
- Core Network / Perimeter Security Entities
The 5G Core has several security functions:
SEAF (Security Anchor Function): Sets up trust anchors for secure sessions.
AUSF (Authentication Server Function): Authenticates users and devices.
ARPF (Authentication Credential Repository and Processing Function): Manages long-term subscriber authentication data.
SDF (Subscription Data Function): Looks after subscriber profiles and authorization data.
SEPP (Security Edge Protection Proxy): Secures communication between operators and guards against attacks when roaming.
These functions make up the backbone of security within the 5G Core.
- Network Function Virtualization (NFV) Security Layer
Given that 5G relies heavily on cloud-native and virtualized systems, security has to cover these virtual elements, too.
The NFV Security Layer defends:
Virtual Network Functions (VNFs): Such as firewalls, IMS, packet cores, and more.
Virtual Resources: Includes CPU, memory, and storage allocated to VNFs.
Physical Resources: Hardware servers that host the virtualized infrastructure.
Security checks are carried out via NFV SSA (Security Service Assurance) across different layers:
VNF Security Assurance.
Virtualized Resource Assurance.
Physical Resource Assurance.
This ensures that any malware or vulnerabilities at the virtualization layer can't compromise the entire network.
- Security Management and Monitoring
Keeping an eye on and managing the security of 5G is crucial for its resilience. The architecture utilizes:
NFV Security Controller (NFV SC): Centralizes the management of security functions.
NFV SSP (Security Service Provider): Analyzes VNFs, virtual resources, and physical resources.
Security Monitoring Databases: Store logs, security analytics, and alerts, such as NVFSeCM DB (Security Monitoring Database), VSF-VNF-CAT (Virtual Security Function Catalog), and NFV-AUD-DB (Audit Database).
Security Monitoring Analytics System: Leverages AI/ML to spot anomalies, thwart DDoS attacks, and foresee threats.
This layer turns 5G into a self-protecting and adaptive system that detects and neutralizes threats in real-time.
Comparative Breakdown of Security Entities
Layer Key Entities Role in Security
User Layer ME, USIM Store credentials, kick off secure access.
Authentication Data SUCI, SUPI, Keys Protect identity, aid secure handover.
Access Network Security gNB-CU, N3IWF Secure radio access and untrusted networks.
Core Network Security SEAF, AUSF, ARPF, SDF, SEPP Authentication, authorization, roaming security.
NFV Security Layer VNF, Virtual & Physical Resources Protects cloud-native functions and infrastructure.
Security Monitoring & Mgmt NFV SC, SSP, Analytics Ongoing monitoring, anomaly spotting, compliance.
Key Features of 5G Security Architecture
End-to-End Encryption: Keeps things confidential all the way from device to core.
Identity Protection: Concealed identifiers help prevent user tracking.
Zero Trust Model: Requires authentication from every component, even trusted ones.
Multi-Layered Security: Covers physical, virtual, and application layers.
AI-Driven Threat Detection: Real-time anomaly detection boosts resilience.
How 5G Security Differs from 4G
While 4G focused on SIM-based authentication and encryption, 5G takes a step further by:
Supporting multiple access technologies (3GPP and non-3GPP).
Allowing network slicing with dedicated security policies.
Utilizing NFV and SDN, which means new protections for virtualization.
Guarding against supply chain and roaming attacks using SEPP.
Introducing stronger encryption algorithms and concealed identifiers (SUCI).
Challenges in 5G Security
Even with its strong design, 5G faces some new hurdles:
Expanded Attack Surface: Millions of IoT devices open up vulnerabilities.
Complex Virtualization: Protecting VNFs needs advanced orchestration.
Supply Chain Risks: Equipment and software dependencies might be at risk.
Inter-Operator Security: Keeping roaming secure is still a big concern.
These challenges call for ongoing security innovation and global standardization.
Conclusion
The 5G Security Architecture is a sophisticated and layered framework aimed at shielding users, devices, and networks from the ever-evolving cyber threats. Everything from user authentication and secure access to core network security entities, NFV protections, and real-time monitoring is crafted with resilience in mind.
For telecom professionals, understanding this architecture is key to ensuring compliance, protecting revenue, and maintaining trust. For tech enthusiasts, it highlights that 5G is not just about speed and low latency but also about protecting our digital future.
As 5G continues to drive innovation in smart cities, autonomous vehicles, and mission-critical applications, its security framework will serve as the bedrock of a trusted global digital ecosystem.
