5G Security Architecture Zoom-In: Key Components and Functions Explained

5G isn't just about faster internet; it's really the foundation for future communication, driving advancements in IoT, self-driving cars, remote healthcare, and smart cities. But with this leap in connectivity, there are definitely more security issues to think about. This generation of technology has a more complex and layered security structure compared to its predecessors, covering everything from the user to the access network, core network, virtualization layer, and security management.
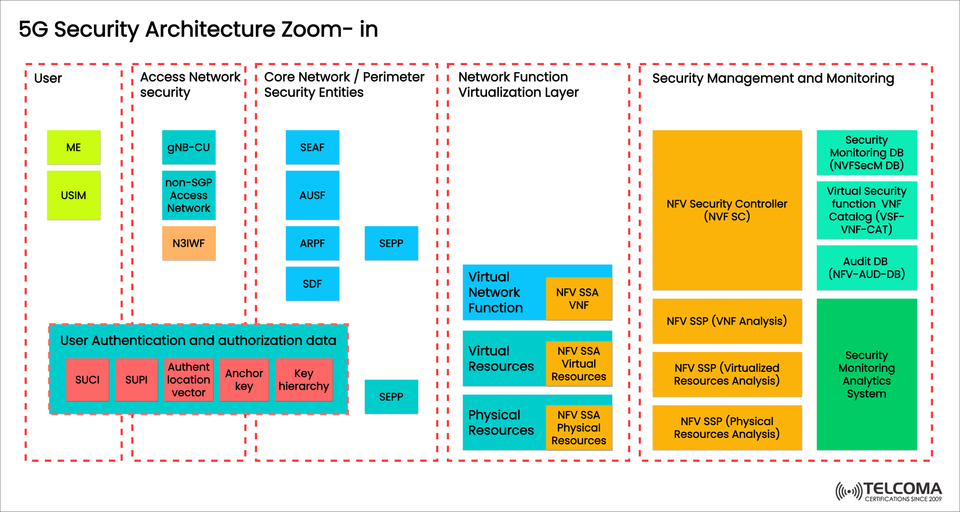
The image above presents a close-up of the 5G Security Architecture, showcasing the essential components and processes that ensure communication is secure, trustworthy, and reliable. Let's dive into it step by step.
Core Pillars of 5G Security Architecture
You can break down the 5G Security Architecture into five key layers:
User Security
Access Network Security
Core Network Security Entities
Network Function Virtualization (NFV) Layer
Security Management and Monitoring
At the heart of all these layers is user authentication and authorization, which is crucial for keeping data safe and intact throughout the system.
- User Security
When it comes to the user, security kicks off with the Mobile Equipment (ME) and Universal Subscriber Identity Module (USIM).
ME (Mobile Equipment): Refers to the device connecting to the network.
USIM: Holds the user’s identity and encryption keys, making secure authentication possible.
This layer makes sure that only approved users with the right credentials can access the 5G network.
- Access Network Security
This part of the network is the initial contact point for users connecting to the core. It includes:
gNB-CU (Next Generation NodeB – Central Unit): Takes care of access security and handling mobility.
Non-3GPP Access Network: Deals with untrusted Wi-Fi or other networks that need secure integration.
N3IWF (Non-3GPP Interworking Function): Serves as a secure bridge between non-3GPP access networks and the 5G core.
This phase is all about ensuring that both trusted and untrusted connections are safe from threats like spoofing or eavesdropping.
- Core Network / Perimeter Security Entities
With the core network, you get some specialized security functions:
SEAF (Security Anchor Function): Secures the core and manages mutual authentication between users and the network.
AUSF (Authentication Server Function): Handles authentication requests and replies.
ARPF (Authentication credential Repository and Processing Function): Keeps long-term subscriber credentials safe.
SDF (Subscriber Data Function): Supplies user subscription and authentication data.
SEPP (Security Edge Protection Proxy): Safeguards signaling between different operators across network boundaries.
These components work together to provide strong end-to-end authentication, data confidentiality, and communication integrity.
- Network Function Virtualization (NFV) Layer
5G relies heavily on virtual systems to adapt and scale. The NFV layer consists of three main resource types:
Virtual Network Function (VNF): Security services set up as virtual functions.
Virtual Resources: Computing, storage, and network resources in a virtual setup.
Physical Resources: The actual hardware that makes virtualization possible.
Each resource layer gets examined through NFV SSA (Security Service Assurance) to spot weaknesses and enforce security policies.
- Security Management and Monitoring
This layer focuses on ongoing monitoring and enforcement of security measures throughout the network:
NFV Security Controller (NFV SC): Directs and upholds security across VNFs.
NFV SSP (Security Service Provider): * VNF Analysis * Virtualized Resources Analysis * Physical Resources Analysis
Databases: * Security Monitoring DB (NVFSecM DB) for up-to-date data. * Audit DB (NFV-AUD-DB) for logging and ensuring compliance. * Virtual Security Function Catalog (VSF-VNF-CAT) for managing virtual security solutions.
Security Monitoring Analytics System: Offers real-time insights and forecasts on potential threats.
This setup ensures that cyber threats can be detected and dealt with proactively.
User Authentication and Authorization Data
At the core of security are the authentication and authorization data, which protect user privacy and access rights. This covers:
SUCI (Subscription Concealed Identifier): Safeguards user identity.
SUPI (Subscription Permanent Identifier): A permanent identifier that’s well protected.
Authentication Vector: Supplies cryptographic material for verifying users.
Anchor Key: Ensures session continuity and helps prevent replay attacks.
Key Hierarchy: Organized key management that supports encryption and keeps integrity across sessions.
By securing these identifiers and credentials, 5G guarantees that user data remains protected from interception and impersonation attacks.
Why 5G Security Architecture Matters
This new architecture comes with several benefits over older networks:
End-to-End Encryption: Provides data protection across various domains.
Mutual Authentication: Confirms identities for both users and the network.
Network Slicing Security: Lets each slice have its own tailored security policies.
Virtualization Security: Protects VNFs and cloud-native setups.
Resilience and Monitoring: Enables real-time threat detection and response.
Summary Table: 5G Security Architecture Layers
Layer Key Components Main Functions
User ME, USIM Identity and key storage
Access Network gNB-CU, Non-3GPP Access, N3IWF Secure connectivity
Core Network SEAF, AUSF, ARPF, SDF, SEPP Authentication, subscriber data, inter-operator security
NFV Layer VNFs, Virtual & Physical Resources Secure virtualization and service assurance
Security Mgmt. NFV SC, SSP, DBs, Analytics Monitoring, enforcement, auditing
4G vs 5G Security: What’s Different?
To really grasp how 5G security has improved, it’s useful to look at it alongside 4G (LTE) architecture.
Aspect
4G Security
5G Security
User Identity Protection
IMSI (International Mobile Subscriber Identity) is sometimes visible.
SUCI (Subscription Concealed Identifier) keeps permanent identity (SUPI) hidden.
Authentication
Mutual authentication has its limits.
Stronger mutual authentication with SEAF and AUSF.
Access Networks
Mainly relies on 3GPP access (LTE, WiMAX).
Allows both trusted and untrusted non-3GPP access through N3IWF.
Virtualization
Very little NFV/SDN integration.
Complete NFV/SDN integration with security measures at VNF, virtual, and physical levels.
Network Slicing
Not available.
Secure, isolated network slices with tailored policies.
Monitoring
Basic logging and auditing.
Real-time monitoring, analytics, and AI-powered threat detection.
From this comparison, it’s clear that 5G is built with security in mind, tackling many of the weaknesses found in 4G.
Conclusion
5G is about more than just speed; it’s focused on creating a trusted digital environment. The 5G Security Architecture Zoom-In illustrates how various layers—from user authentication to network monitoring—work in harmony to deliver comprehensive security, resilience, and privacy.
For telecom professionals, grasping this architecture is vital for designing, deploying, and managing secure 5G networks that can face evolving cyber challenges while facilitating next-gen services.
