5G Standalone UE Context Transfer and NAS Identity Procedure Explained

5G Standalone Registration: UE Context Transfer and NAS Identity Procedure
The 5G Standalone (SA) registration process involves an important step where the User Equipment (UE), 5G Node B (g NB), and the 5G Core (5GC) work together in the UE Context Transfer and NAS Identity Exchange phase. This helps the new AMF (Access and Mobility Management Function) securely identify and authenticate the UE, either with information already on file or new security credentials.
This part of the process is crucial for maintaining service continuity, secure identification, and smooth registration in 5G networks. Let’s break it down step by step.
Overview: Why UE Context Transfer Matters
The UE Context Transfer procedure lets a new AMF gather important information about a UE from the previous AMF. This is especially useful when the UE is moving between AMFs or reconnecting after some inactivity.
If this transfer didn't happen, the UE would have to re-register from the beginning, which would slow things down and add extra signaling. Instead, 5G networks try to make use of existing context whenever possible, speeding up authentication and keeping services seamless.
Key Benefits:
Lowers signaling load on the core network
Ensures UE continuity when switching AMFs
Recycles authentication context when still valid
Promotes smooth mobility and quick registration
Message Flow Summary
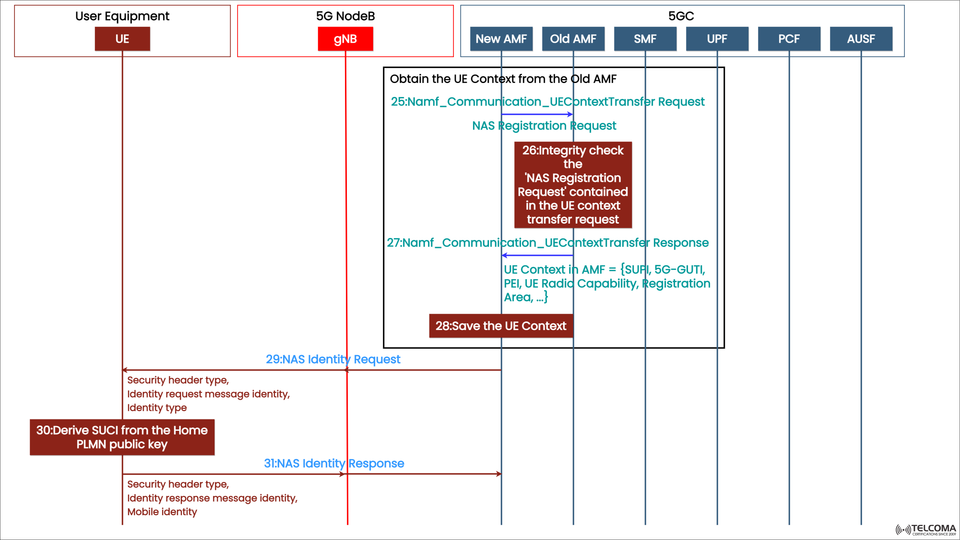
The diagram highlights steps 25 to 31 in the 5G SA registration flow, involving both the old and new AMFs, gNB, and UE. Here’s a brief overview:
Step Message/Action Direction Purpose
25 Nam f_ Communication _ UE Context Transfer Request New AMF → Old AMF Requests UE context, including NAS Registration info
26 Integrity check of NAS Registration Request Old AMF Verifies NAS message integrity
27 Nam f_ Communication _ UE Context Transfer Response Old AMF → New AMF Sends back UE context (SUFI, 5G-GUTI, PEI, UE Capabilities, etc.)
28 Save the UE Context New AMF Stores the context received
29 NAS Identity Request New AMF → UE Requests UE identity for verification
30 Derive SUCI from Home PLMN Public Key UE internal UE encrypts its identity (SUPI) to create SUCI
31 NAS Identity Response UE → New AMF UE sends SUCI (Subscription Concealed Identifier)
- Step-by-Step Breakdown of the Procedure
Let’s delve into the technical details of each step.
Step 25: Nam f"_ Communication _ UE Context Transfer Request
After the Initial UE Message (which contains the NAS Registration Request) reaches the new AMF, it checks if there’s a previous AMF association. If there is, the new AMF will try to pull the UE context from the old AMF to sidestep unnecessary registration.
Purpose: To utilize existing security and registration context.
Sent by: New AMF → Old AMF
Includes:
NAS Registration Request (from UE)
UE identifiers, like 5G-GUTI
Potential tracking area and slice information
This step kicks off the UE context recovery process, which is vital for seamless handovers or mobility-related registration updates.
Step 26: Integrity Check of NAS Registration Request
Here, the old AMF carries out an integrity check on the included NAS Registration Request during the context transfer.
Integrity Check Ensures:
The NAS message hasn’t been tampered with during its journey.
The request genuinely came from the authenticated UE.
It blocks replay attacks or attempts at spoofing.
This step boosts the security framework of the 5G NAS layer, in accordance with 3GPP TS 33.501 security standards for 5G.
Step 27: Nam f"_ Communication _ UE Context Transfer Response
Once the old AMF verifies the NAS message, it sends a UE Context Transfer Response back to the new AMF.
UE Context in AMF may include:
SUPI (Subscription Permanent Identifier)
5G-GUTI (Temporary Identifier)
PEI (Permanent Equipment Identifier)
UE Radio Capability Information
Registration Area and Security Contexts
These details enable the new AMF to move forward with registration without needing a full re-authentication, unless specific policies or timeouts dictate otherwise.
Step 28: Save the UE Context
The new AMF saves the UE context it just received into its records.
This ensures:
Quick access to user information for further signaling.
The establishment of a UE context in the new AMF that corresponds with the state the old AMF was managing.
An efficient transition between network functions with minimal signaling overhead.
At this moment, the UE context has been successfully transferred and stored in the new AMF.
Step 29: NAS Identity Request
After saving the context, the new AMF sends a NAS Identity Request to the UE to confirm or reacquire its identity.
Message Details:
Type: NAS message from AMF to UE
Contains:
Security header type
Identity request message identity
Requested identity type (like SUCI, GUTI, IMEI)
The goal here is to make sure the AMF links the correct user subscription (SUPI) to the right security context, especially if the UE context was only partially recovered or incomplete.
Step 30: Derive SUCI from the Home PLMN Public Key
When the UE gets the NAS Identity Request, it creates its SUCI (Subscription Concealed Identifier).
Process Overview:
The UE uses the Home PLMN’s (Public Land Mobile Network) public key.
The SUPI (usually the IMSI) is encrypted with this key.
The outcome is the SUCI, a privacy-enhanced version of the subscriber’s identity.
Why SUCI is Important:
It prevents sensitive subscriber identifiers (IMSI) from being transmitted openly.
It allows secure identification without exposing actual subscriber details.
It meets GDPR privacy standards.
This cryptographic aspect is one of the strongest privacy upgrades in the 5G security framework.
Step 31: NAS Identity Response
In the end, the UE sends the NAS Identity Response back to the new AMF.
Contents:
Security header type
Identity response message type
Mobile identity (SUCI)
The AMF uses this information to:
Retrieve the SUPI by decrypting the SUCI (using the Home PLMN’s private key).
Verify the UE’s identity.
Move ahead with authentication through the AUSF (Authentication Server Function).
Now, the UE is securely identified within the new AMF context, all set for the authentication and policy enforcement steps.
Technical Highlights and Security Mechanisms
Feature Description
UE Context Transfer Allows old AMF context to be reused for fast re-registration.
NAS Integrity Check Stops tampering and spoofing of NAS messages.
SUCI Encryption Safeguards user identity using asymmetric cryptography.
Privacy Compliance Conceals permanent identifiers during signaling.
AMF Context Synchronization Keeps services continuous during AMF relocations.
These features work together to ensure that the 5G registration process is effective, secure, and privacy-respecting.
Integration with Other 5GC Functions
During and after this stage:
AUSF (Authentication Server Function) authenticates the UE using SUCI/SUPI.
SMF (Session Management Function) prepares for session setup requests.
PCF (Policy Control Function) later applies policies based on subscription information.
The AMF serves as the anchor for the control plane, facilitating secure communication among all components in the 5GC.
Troubleshooting Common Issues
Telecom engineers often face issues during this phase. Some common challenges include:
Failed Context Retrieval: Old AMF is unreachable or context has expired.
NAS Integrity Check Failure: NAS message is corrupted or mismatched.
SUCI Derivation Errors: The configuration of the PLMN public key is incorrect.
Identity Request Loops: Repeated identity requests due to incomplete context.
Network logs (like AMF traces and NAS signaling captures) can be crucial in diagnosing these problems.
5G Security Perspective
This part of the 5G registration process underlines the zero-trust security architecture of 5G.
NAS messages are protected for integrity.
UE identities are concealed and encrypted.
Context transfers utilize secure Service-Based Interfaces (SBI).
This design ensures that even during mobility, user privacy and network integrity stay intact.
Conclusion
The UE Context Transfer and NAS Identity Procedure in 5G Standalone plays a crucial role linking the start of registration to the authentication phase. By allowing for context reuse, integrity checks, and secure SUCI-based identification, this step ensures the registration process is both efficient and confidential.
For telecom professionals, mastering these interactions between the UE, gNB, and 5GC (AMF, AUSF, SMF) is vital for enhancing 5G performance and ensuring network security integrity.
