AKMA Key Hierarchy in 5G Security: A Detailed Guide for Telecom Professionals

AKMA Key Hierarchy in 5G Security: A Guide for Telecom Professionals
As 5G technology takes off, securing user data and ensuring reliable communication between devices and networks is now a top priority. A key element identified by 3GPP (3rd Generation Partnership Project) to accomplish this is the AKMA (Authentication and Key Management for Applications) framework.
The AKMA key hierarchy outlines how cryptographic keys are created and shared in the authentication process, safeguarding user identities and enabling secure communications across the Home Public Land Mobile Network (HPLMN), Authentication Server Function (AUSF), Application Anchor Function (AAnF), and Application Function (AF).
In this blog, we’ll delve into the AKMA key hierarchy step by step, explore its significance, and examine how each key plays a role in the layered security of 5G networks.
What is AKMA in 5G?
AKMA (Authentication and Key Management for Applications) is a security mechanism in 5G that goes beyond traditional network access to provide secure authentication. It allows for the secure generation and distribution of keys among different network functions and user equipment, ensuring that even application-level services are backed by strong cryptographic protection.
The system builds on the results of 5G primary authentication to create multiple layers of keys. Each key has a specific function, is scoped for a particular network action, and helps minimize vulnerabilities while keeping things efficient.
Understanding the AKMA Key Hierarchy
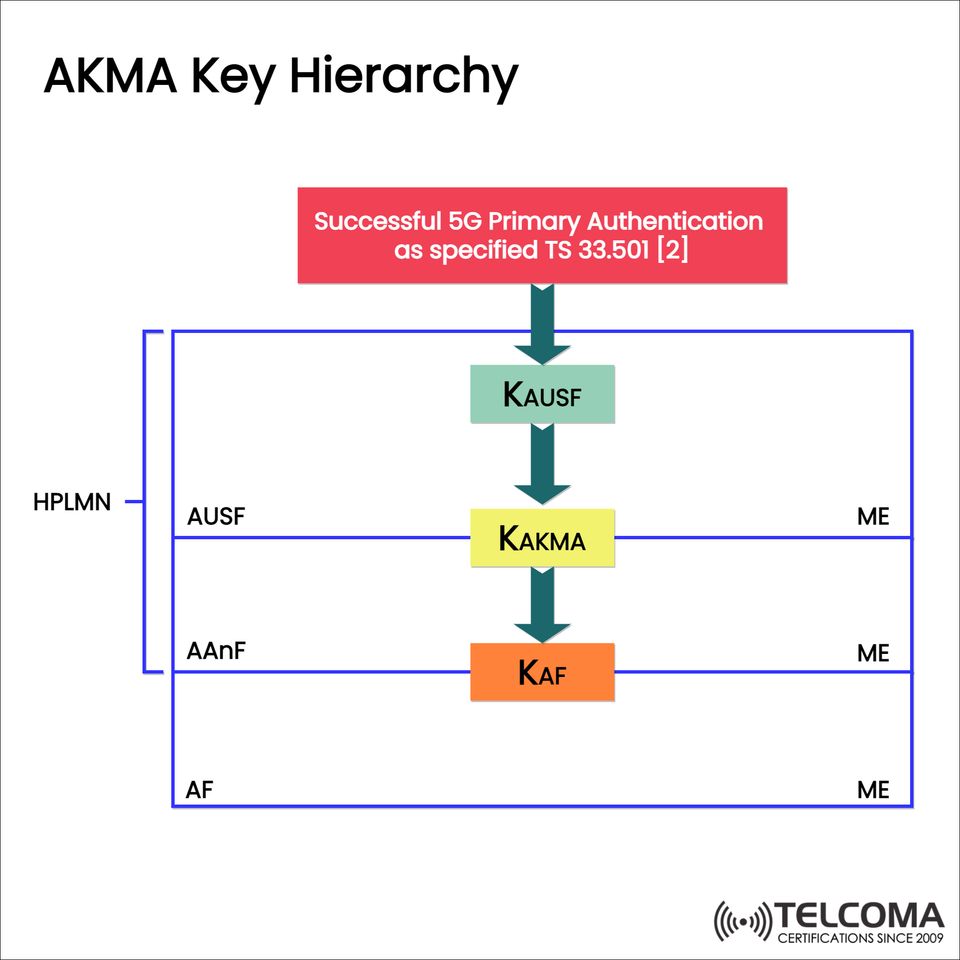
The diagram uploaded outlines the AKMA Key Hierarchy process according to the 3GPP TS 33.501 specification. Let’s break down the flow:
- Successful 5G Primary Authentication
Before starting the AKMA process, a 5G primary authentication occurs between the UE (User Equipment) and the network.
Once that’s successfully completed, a root key known as K ext{_}AUSF is derived.
This step ensures that only verified users and devices can move on to the next phases of the hierarchy.
- K ext{_}AUSF (Authentication Server Function Key)
Derived at: AUSF after primary authentication.
Role: Acts as the root key for generating additional keys.
Scope: Stored in the AUSF and securely shared with the user’s Mobile Equipment (ME).
K ext{_}AUSF forms the foundation of the AKMA hierarchy, from which all other application-level keys are generated.
- K ext{_}AKMA (AKMA Key)
Derived from: K ext{_}AUSF
Role: An intermediate key created specifically for the AKMA framework.
Scope: Utilized within the AUSF and securely passed to the ME.
K ext{_}AKMA ensures a distinction between general authentication keys and the application-specific security keys. This multi-layered approach lowers the risk if any lower-level keys are compromised.
- K ext{_}AF (Application Function Key)
Derived from: K ext{_}AKMA
Role: The final service-level key used by the Application Function (AF).
Scope: Shared among the Application Anchor Function (AAnF), AF, and the ME.
K ext{_}AF is the operational key that enables secure sessions between users and specific applications. By scoping it at the application level, AKMA makes sure that if one application’s key is compromised, it won't affect other services or the root authentication process.
Visual Representation: AKMA Flow
The uploaded image shows the downward key derivation process clearly:
Successful 5G Primary Authentication → K ext{_}AUSF
K ext{}AUSF → K ext{}AKMA
K ext{}AKMA → K ext{}AF
Key Derived From Used By Purpose K ext{}AUSF5G Primary AuthAUSF, ME Root key for authentication K ext{}AKMAK ext{}AUSFAUSF, MEAKMA intermediate key K ext{}AFK ext{_}AKMAAAnF, AF, ME Application-level security key
Why is the AKMA Key Hierarchy Important?
The AKMA hierarchy tackles several challenges in 5G security:
Separation of Concerns: Each key has a specific role and scope, which helps prevent a single point of failure.
Scalability: By generating keys for individual applications, the network supports a variety of secure services.
Application Security: Applications benefit from unique keys (K ext{_}AF) instead of relying on the same root authentication credentials.
Enhanced Privacy: Since K ext{_}AUSF remains within the AUSF, the risks of exposure are kept low.
Standards Compliance: AKMA is specified in 3GPP TS 33.501, ensuring it works seamlessly across the globe.
Real-World Use Cases of AKMA in 5G
Secure IoT Communication: IoT devices often tap into 5G networks for crucial tasks, where AKMA ensures each device/application has its own secure key.
Network Slicing Security: 5G's network slicing allows multiple services to operate on the same infrastructure. AKMA keeps keys isolated for each slice, protecting against cross-slice attacks.
Enterprise Applications: Businesses using private 5G networks can rely on AKMA for secure user and service authentication.
Over-the-Top (OTT) Services: Service providers like streaming platforms or financial services can authenticate sessions securely using K ext{_}AF without revealing the network’s root keys.
Advantages of AKMA over Legacy Key Management
When compared to LTE and earlier networks, AKMA in 5G offers:
More precise key distribution
Better resilience against breaches
Support for advanced services beyond basic connectivity
Future-proof design for IoT and industry 4.0 use cases
Conclusion
The AKMA key hierarchy is a crucial element of the 5G security architecture, ensuring that authentication and key management extend past mere network access. By organizing keys from K ext{}AUSF → K ext{}AKMA → K ext{_}AF, this framework delivers layered protection, service-level isolation, and application security.
For telecom professionals and network architects, grasping the ins and outs of AKMA is essential for crafting and sustaining secure, scalable, and forward-looking 5G deployments.
As 5G continues to develop, AKMA will remain key in safeguarding sensitive data and enabling the secure digital experiences that users and enterprises expect.
