API Security Requirements in 5G Core (5GC): Frameworks & Best Practices
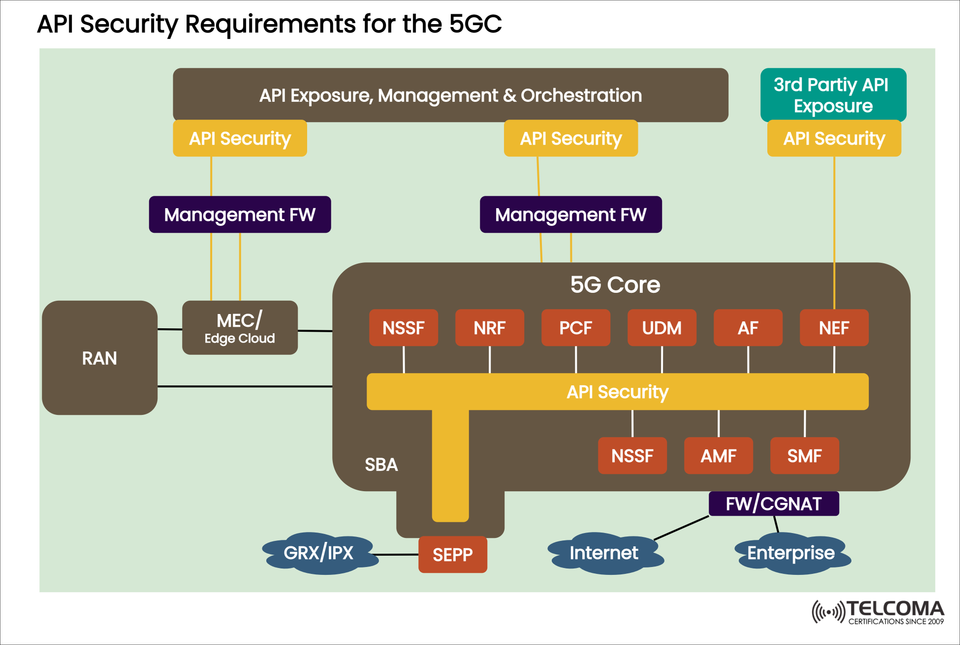

As 5G networks continue to evolve, the 5G Core (5GC) has become essential for enabling highly reliable, low-latency communication and extensive IoT connectivity. Different from previous generations, 5GC utilizes a Service-Based Architecture (SBA), allowing network functions (NFs) to interact via APIs.
This API-focused approach enhances flexibility and scalability, but it also brings along some security challenges. Protecting APIs from unauthorized access, data breaches, and exploitation is crucial. The image above presents the API security requirements for the 5G Core, which includes aspects like exposure, management, orchestration, and integration with external systems.
Why API Security is Critical in 5G Core
5G Core APIs are vital for:
Network Function Communication: NFs such as AMF, SMF, NRF, and PCF share information through APIs.
Multi-Access Edge Computing (MEC): APIs oversee edge cloud services to achieve ultra-low latency.
Third-Party Exposure: APIs allow external applications and services to interact with the network.
Network Orchestration: APIs facilitate automation, scalability, and effective resource management.
But along with these advantages come several risks:
Unauthorized access to sensitive subscriber information.
API misuse by harmful third-party apps.
Denial-of-Service (DoS) attacks targeting network functions.
Data leaks between network and enterprise boundaries.
So, API security isn’t just optional—it’s a fundamental necessity for maintaining trust, integrity, and reliability within 5G networks.
API Security Framework in 5GC
As the image shows, the API security framework covers multiple layers of the 5G ecosystem:
- API Exposure, Management & Orchestration
APIs are made available to both internal and external entities for orchestration purposes.
Security measures ensure that only authenticated and authorized users get access.
API gateways and management frameworks are in place to enforce these security protocols.
- 5G Core Network Functions (NFs)
The 5G Core includes service-based NFs like:
NSSF (Network Slice Selection Function) – Manages network slicing.
NRF (Network Repository Function) – Takes care of NF registration and discovery.
PCF (Policy Control Function) – Oversees QoS and policy rules.
UDM (Unified Data Management) – Stores subscriber details.
AF (Application Function) – Offers application-level services.
NEF (Network Exposure Function) – Safely exposes APIs to third parties.
AMF (Access and Mobility Management Function) – Manages user access and mobility.
SMF (Session Management Function) – Handles session control.
Each of these NFs communicates through APIs, necessitating end-to-end encryption, authentication, and authorization controls.
- Multi-Access Edge Computing (MEC)
MEC brings the 5G Core to the edge for low-latency applications.
APIs at the MEC level need to be secured to avoid unauthorized access to edge resources.
- Third-Party API Exposure
APIs are accessible to external developers, businesses, and service providers.
The Network Exposure Function (NEF) ensures secure and controlled access.
API security in this context helps prevent misuse and enforces Service Level Agreements (SLAs).
- Interconnect Security
APIs must be secured across external connections:
GRX/IPX – For roaming and inter-operator communication.
SEPP (Security Edge Protection Proxy) – Safeguards inter-PLMN signaling.
FW/CGNAT – Provides firewall protection and address translation for internet and enterprise access.
Key API Security Requirements for the 5G Core
Here are the key requirements:
Requirement Description Purpose Authentication Strong identity verification for all API clients . Prevents unauthorized access . Authorization Role-based and context-aware permissions . Ensures only legitimate requests are processed . Encryption End-to-end TLS for data-in-transit . Protects API traffic from eaves dropping . Integrity Protection Digital signatures and hash verification . Ensures data hasn’t been tampered with . Rate Limiting Limits excessive API requests . Prevents DoS attacks and resource misuse . Audit & Logging Monitoring API calls and activities . Supports compliance and highlights threats . Threat Detection AI/ML-based anomaly detection for APIs . Spots malicious behavior early . API Gateway Protection Central enforcement point for policies .Simplifies security and orchestration.
API Security Challenges in 5GC
Even with solid frameworks, 5G APIs encounter challenges:
The dynamic nature of 5G traffic complicates anomaly detection.
Third-party integration broadens the attack surface.
Standardizing roaming and inter-operator APIs securely poses a challenge.
Applications sensitive to latency (think AR/VR, IoT, and autonomous vehicles) need fast but secure API responses.
Best Practices for API Security in 5GC
To tackle these challenges, operators and vendors need to adopt best practices:
Zero-Trust Architecture (ZTA): Always authenticate and authorize; never assume trust.
API Tokenization & OAuth 2.0: Use token-based authentication to secure third-party API access.
Transport Layer Security (TLS 1.3): Ensure secure and encrypted API communication.
Mutual Authentication: Both API providers and consumers should verify each other.
API Gateway Deployment: Leverage gateways for traffic monitoring, threat detection, and policy enforcement.
Continuous Monitoring: Use real-time analytics to identify anomalies in API traffic.
Regular Security Audits: Conduct penetration tests and vulnerability assessments.
Standard Compliance: Follow 3GPP security specifications and GSMA API security guidelines.
Role of NEF in Securing API Exposure
One of the most important components shown in the image is the Network Exposure Function (NEF).
Acts as a secure API broker between internal 5G functions and external third-party APIs.
Validates, filters, and enforces security policies on every API request.
Monitors third-party usage to identify abuse and ensure compliance.
So, NEF is a key player in securing API exposure in the 5G ecosystem.
Conclusion
As 5G networks establish themselves as the backbone of global connectivity, API security in the 5G Core is absolutely vital. APIs drive agility, service innovation, and integration across multiple domains, but they also introduce new vulnerabilities.
The image emphasizes how API security requirements extend across 5GC functions, edge computing, orchestration, and third-party exposure. For a secure ecosystem, operators need to implement authentication, authorization, encryption, monitoring, and compliance frameworks.
By adhering to best practices and following industry standards, telecom operators can make sure that the 5G Core remains secure, resilient, and trustworthy, thereby enabling next-generation applications like IoT, AR/VR, and autonomous systems.
