CAPIF and NEF in 5G: Understanding the Common API Framework and Network Exposure Function

The Importance of API Exposure in 5G
In 5G networks, APIs (Application Programming Interfaces) act as a crucial link between telecom infrastructure and digital innovation. They enable external applications and services to access network intelligence, like user data analytics, QoS control, edge computing, and much more.
That said, open access needs to be secure, standardized, and auditable. This is where CAPIF (Common API Framework) and NEF (Network Exposure Function) come into play.
Together, they lay the foundation for 5G network exposure, making sure that every API request—whether it’s from a trusted internal application or a third-party developer—adheres to the same security, discovery, and authorization protocols.
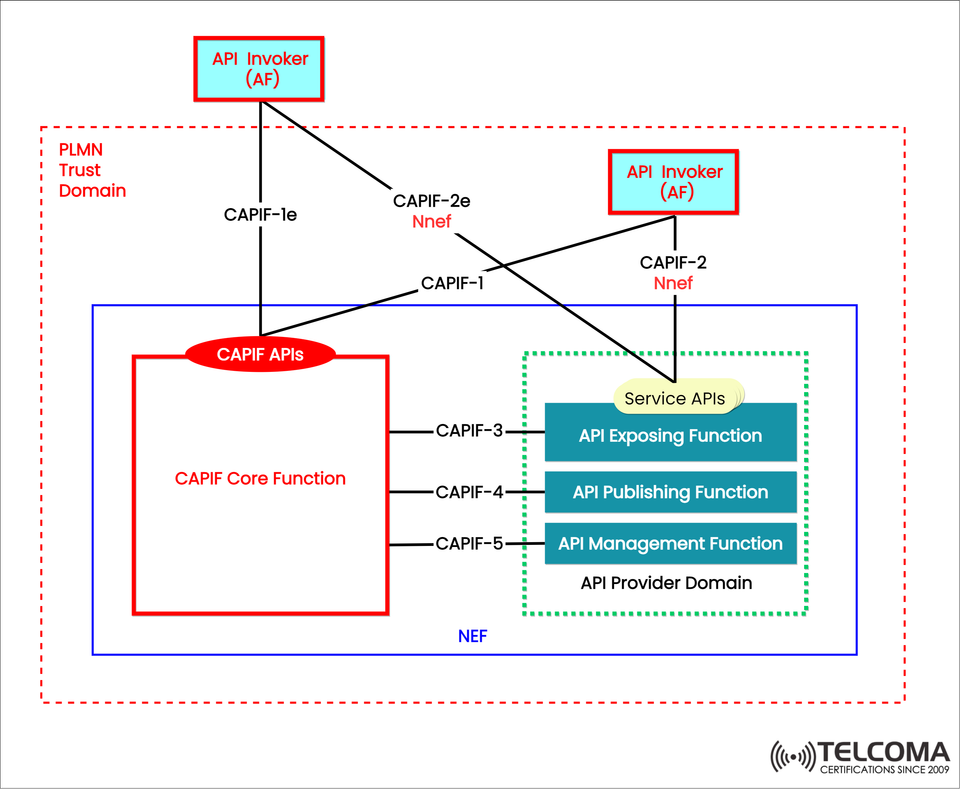
The image above (from Telcoma) visually depicts this integration: API Invokers (AFs) connect to CAPIF Core Functions and API Provider Domains using standardized interfaces (CAPIF-1 to CAPIF-5), all within the PLMN Trust Domain.
Understanding CAPIF: The Common API Framework
What is CAPIF?
CAPIF (Common API Framework) is a standardized framework from 3GPP that outlines how network APIs are safely published, managed, and accessed. It creates a common environment for both internal and external API invokers to interact with network services.
The aim is to standardize how APIs are:
Exposed by network functions (like NEF, PCF, NWDAF).
Discovered and consumed by external applications.
Governed and secured by operators.
In short, CAPIF provides a single entry point for all API interactions within a trusted telecom environment.
Introducing NEF: The Network Exposure Function
What is NEF?
The Network Exposure Function (NEF) is a core network function in 5G that exposes network capabilities to third-party application functions (AFs) via APIs.
It manages:
Secure northbound exposure of 5G core services.
Authentication, authorization, and policy enforcement for all API calls.
Translation of internal 3GPP interfaces (like Nnrf, Npcf) into more user-friendly APIs.
While NEF focuses on the actual exposure of 5G core functions, CAPIF sets the standardized framework that dictates how this exposure happens.
CAPIF and NEF: How They Connect
In the 5G architecture, CAPIF and NEF are closely linked. NEF can serve as the API Provider Domain within the CAPIF ecosystem.
CAPIF defines the framework and interfaces.
NEF carries out the exposure of network services in line with CAPIF standards.
As illustrated in the image:
Both the CAPIF Core Function and NEF operate within the PLMN Trust Domain.
API Invokers (AFs) communicate through CAPIF interfaces (like CAPIF-1, CAPIF-2, etc.).
The NEF domain includes CAPIF-compliant functions such as:
API Exposing Function
API Publishing Function
API Management Function
This integration ensures that every API transaction—from registration to invocation—follows a consistent and secure lifecycle.
CAPIF Architecture: Key Entities and Their Roles
The architecture is made up of three core entities:
a) API Invoker (AF)
Represents an Application Function (AF) or third-party service that uses network APIs.
Registers and authenticates through CAPIF-1e.
Invokes network services via CAPIF-2 or CAPIF-2e.
Examples include: IoT platforms, enterprise dashboards, or content delivery services.
b) CAPIF Core Function
Acts as the central hub for authentication, authorization, and API discovery.
Provides CAPIF APIs for:
Invoker registration and onboarding.
Access to API catalogs and discovery.
Usage tracking and auditing.
This function enforces trust and policy, ensuring only authorized invokers can access exposed APIs.
c) API Provider Domain (NEF)
Contains the actual service APIs exposed by NEF.
Comprises:
API Exposing Function – manages API exposure to CAPIF Core.
API Publishing Function – registers APIs with CAPIF Core for discovery.
API Management Function – oversees analytics, throttling, and version control.
CAPIF Interfaces (Reference Points)
The CAPIF framework identifies five standardized reference points to ensure secure communication between entities:
Reference Point | Connection | Purpose
CAPIF-1 / CAPIF-1e | API Invoker ↔ CAPIF Core | Invoker onboarding, authentication, API discovery
CAPIF-2 / CAPIF-2e (Nnef) | API Invoker ↔ API Provider (NEF) | Direct service API invocation
CAPIF-3 | CAPIF Core ↔ API Exposing Function | Management of API exposure
CAPIF-4 | CAPIF Core ↔ API Publishing Function | API publishing and registration
CAPIF-5 | CAPIF Core ↔ API Management Function | Analytics, policy, and operational data exchange
These interfaces collectively promote trust, transparency, and control over API usage across different domains.
The PLMN Trust Domain
All CAPIF and NEF components operate within the PLMN (Public Land Mobile Network) Trust Domain.
This domain ensures that:
Every API Invoker and Provider is authenticated.
Communication is encrypted and auditable.
Operators maintain control and visibility over API access.
The trust domain acts as a security boundary, separating trusted internal components from external systems while allowing controlled exposure.
CAPIF-NEF Workflow: How It All Comes Together
Here’s a simple step-by-step example of how CAPIF and NEF work together:
Registration: The API Invoker (AF) registers with the CAPIF Core using CAPIF-1e. The Core authenticates the invoker and issues credentials.
API Discovery: The AF queries the CAPIF Core for available service APIs, and CAPIF returns the APIs published by NEF via CAPIF-4.
Authorization: CAPIF checks the AF’s authorization and issues access tokens.
Invocation: The AF uses CAPIF-2 (Nnef) to invoke NEF’s exposed APIs, for instance, requesting QoS data or edge session info.
Management & Auditing: CAPIF Core monitors all API usage through CAPIF-5, ensuring compliance, analytics, and billing.
Advantages of Integrating CAPIF with NEF
For Network Operators
Unified governance of all exposed APIs.
Streamlined policy enforcement and audit controls.
More straightforward cross-domain API management.
For Developers / API Invokers
Single, standardized access to network capabilities.
Faster onboarding thanks to automated discovery.
Assured security and interoperability.
For the Ecosystem
Encourages open innovation while keeping operator control intact.
Ensures compliance with 3GPP security frameworks.
Supports multi-operator API federation and roaming practices.
Security Measures in CAPIF and NEF
Security is a cornerstone of the CAPIF-NEF integration. This framework includes:
Mutual TLS authentication for all CAPIF interfaces.
OAuth 2.0 for access tokens and delegated authorization.
JWT (JSON Web Tokens) for lightweight, verifiable credentials.
Auditing and non-repudiation for every transaction.
Policy-based control to enforce role-based access management.
These elements work together to keep operator networks secure and compliant, even in an open API environment.
Real-World Applications of CAPIF and NEF
Here are some practical examples:
Smart Manufacturing: Enterprise AFs manage network slices using NEF APIs through CAPIF.
Edge Computing: Applications discover and securely invoke edge service APIs.
IoT Enablement: IoT platforms connect with network analytics APIs for better optimization.
Developer Ecosystems: Operators publish APIs to developer portals via CAPIF for external access.
These cases illustrate how CAPIF can transform 5G into an open, programmable platform.
The Future of CAPIF and NEF
As the industry moves towards 5G Advanced and 6G, CAPIF’s role will broaden to:
Support multi-operator federation for global API access.
Integrate AI/ML-driven API management for predictive policy enforcement.
Enable cross-industry API ecosystems (think automotive, healthcare, energy).
Upcoming releases will likely standardize CAPIF extensions for edge and cloud APIs, pushing towards a seamless network-as-a-service (NaaS) model.
Conclusion
The integration of CAPIF and NEF is vital for creating an open and programmable 5G network.
As the image shows, CAPIF delivers the governance, authentication, and exposure framework, while NEF acts as the execution layer that provides network services securely.
This collaboration allows telecom operators to safely open their networks to developers, enterprises, and verticals, driving innovation while retaining full control and compliance.
In essence, CAPIF and NEF together are reshaping 5G into not just a communication network, but a platform for innovation—unlocking the full potential of digital ecosystems.
