Driving AKMA Root Key after Primary Authentication in 5G Networks

In 5G networks, security is key for reliable connectivity and protecting user data. A major part of this security framework is the AKMA (Authentication and Key Management for Applications) root key derivation process. After the initial authentication, the AKMA root key is vital for ensuring secure communications and effective identity management between the User Equipment (UE), Authentication Server Function (AUSF), and the Unified Data Management (UDM).
This blog will take a deeper look at how the AKMA root key gets established after primary authentication, outlining the steps involved and why it's crucial for secure operations in 5G. We’ll simplify the process flow, making it clearer for telecom professionals and anyone interested in the technical details.
What is AKMA in 5G Security?
AKMA (Authentication and Key Management for Applications) provides a framework within 5G that offers:
A secure way to derive application-level keys as part of the 5G authentication process.
Protection against identity theft and man-in-the-middle attacks.
A distinction between network access authentication and service-level authentication.
The AKMA root key (K_AKMA) is derived from the K_AUSF (Authentication Server Function key), establishing trust right from the primary authentication.
Primary Authentication in 5G
Before we can derive the AKMA root key, the primary authentication happens between:
UE (User Equipment) – The mobile device or endpoint starting the authentication.
AMF (Access and Mobility Management Function) – Handles registration, mobility, and access authentication signaling.
AUSF (Authentication Server Function) – Validates the subscriber's authentication credentials.
UDM (Unified Data Management) – Stores subscription details and verifies the subscriber's identity.
This process sets up K_AUSF, which is the basis for deriving K_AKMA.
Step-by-Step Process of Deriving AKMA Root Key after Primary Authentication
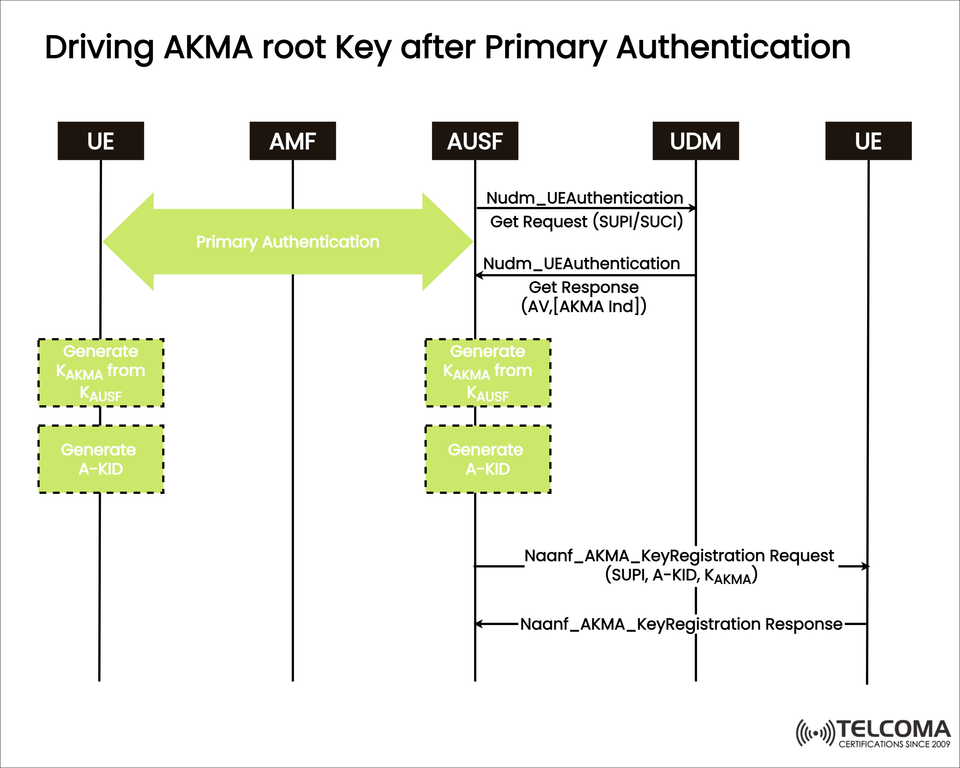
The image outlines this series of steps:
- Primary Authentication
The UE connects with the AMF to start the authentication process.
The AUSF gets authentication vectors from the UDM via Nudm_UE Authentication. Get Request (SUPI/SUCI).
The UDM replies with authentication vectors (AV) and an AKMA Indication flag.
- Derivation of K_AKMA
Once primary authentication is done, the UE calculates the K_AKMA key from K_AUSF.
At the same time, the AUSF derives the same K_AKMA.
This ensures that both the UE and AUSF have the same AKMA root key, fostering mutual trust.
- Generation of A-KID
Both the UE and AUSF also create an A-KID (AKMA Key Identifier).
This unique identifier allows them to reference the derived key without revealing the actual K_AKMA.
- Key Registration with UDM
The AUSF sends a Naan f_A KM A_ Key Registration Request that includes:
SUPI (Subscription Permanent Identifier)
A-KID
K_AKMA
The UDM responds with Naanf_AKMA_KeyRegistration Response, confirming that the key was registered successfully.
- Secure Key Availability
After registration, the AKMA key is ready for use to secure application-level services.
This setup helps avoid repeatedly exposing the primary authentication process, providing a reliable trust anchor.
Workflow Summary (Tabular Form)
Step Entities InvolvedActionOutcome1UE ↔ AMF ↔ AUSF ↔ UDM Primary Authentication Establishes K_AUSF2UE, AUSF Derive K_AKMA from K_AUSF Shared root key established3UE, AUSF Generate A-KID Key identifier created4AUSF ↔ UDM Key Registration K_AKMA securely registered5UE, Network Secure Use Key available for applications
Why is Deriving the AKMA Root Key Important?
Stronger Security: Even if application-level keys are compromised, the root key stays safe.
Separation of Concerns: Keeps access authentication separate from application authentication, which boosts modularity.
Scalability: Multiple applications can use a single AKMA root key, without needing to redo the authentication process.
Efficiency: Reduces the signaling load by not requiring repeated primary authentication.
Trust Management: Offers a secure base for application providers without exposing user credentials.
Technical Insights for Telecom Professionals
Nudm_UE Authentication Interface
Vital for communication between AUSF and UDM.
Manages retrieval and validation of subscriber identity and authentication vectors.
Key Derivation Function (KDF)
Used to create K_AKMA from K_AUSF.
Ensures one-way cryptographic derivation to prevent reverse engineering.
A-KID Usage
Prevents direct sharing of K_AKMA.
Offers a secure reference for applications and UDM during key management.
Naanf_AKMA Messages
Standardized interfaces for key registration and management.
Guarantees interoperability between AUSF and UDM.
Use Cases of AKMA Root Key in 5G
Application Security: Facilitates secure communication between mobile apps and network services.
IoT Device Authentication: Safeguards IoT devices that require robust yet lightweight authentication.
Enterprise Networks: Provides secure access for enterprises to 5G-enabled applications without compromising user credentials.
Roaming Scenarios: Ensures trusted key exchange across different networks.
Challenges and Considerations
While AKMA strengthens 5G security, telecom professionals need to keep in mind:
Key Lifetime Management: Keys should have set expiration times to prevent unapproved use.
Synchronization Issues: It's crucial for UE and AUSF to stay in sync during key derivation.
Scalability in Large Networks: Managing billions of IoT devices requires efficient key registration systems.
Standard Compliance: Adhering to 3GPP specifications is essential for interoperability.
A Closer Look: What Sets AKMA Apart from Traditional Authentication
In older mobile networks like 3G and 4G, authentication was closely tied to the network access layer. This meant apps had to use different methods (such as OAuth, TLS, or SIM-based APIs) to create secure connections. This setup often led to a lack of trust consistency, increased delays, and several different security domains to handle.
Things have changed with 5G AKMA:
Unified Trust Anchor: It comes from the same root authentication key (K ext{_}AUSF), which means it's strongly linked to the user's identity.
Application Independence: Once the AKMA key is created, various applications (like OTT apps, enterprise tools, and IoT platforms) can use it securely without needing to go through the authentication process again.
Efficient Key Reuse: Just one initial authentication provides reusable key material for several services.
So, in essence, AKMA closes the gap between network and application security, making 5G more flexible for businesses and IoT applications.
Conclusion
The process of deriving the AKMA root key after primary authentication is a fundamental component of 5G security architecture. By utilizing K_AUSF and securely generating both K_AKMA and A-KID, networks can ensure a trusted and scalable method for application-level authentication. This not only boosts security but also streamlines identity management for services in 5G networks across applications, IoT, and enterprise solutions.
For anyone in telecommunications or tech, getting a grip on AKMA is key to building secure and scalable 5G systems.
