Fundamental Network Model for AKMA in 5G Security
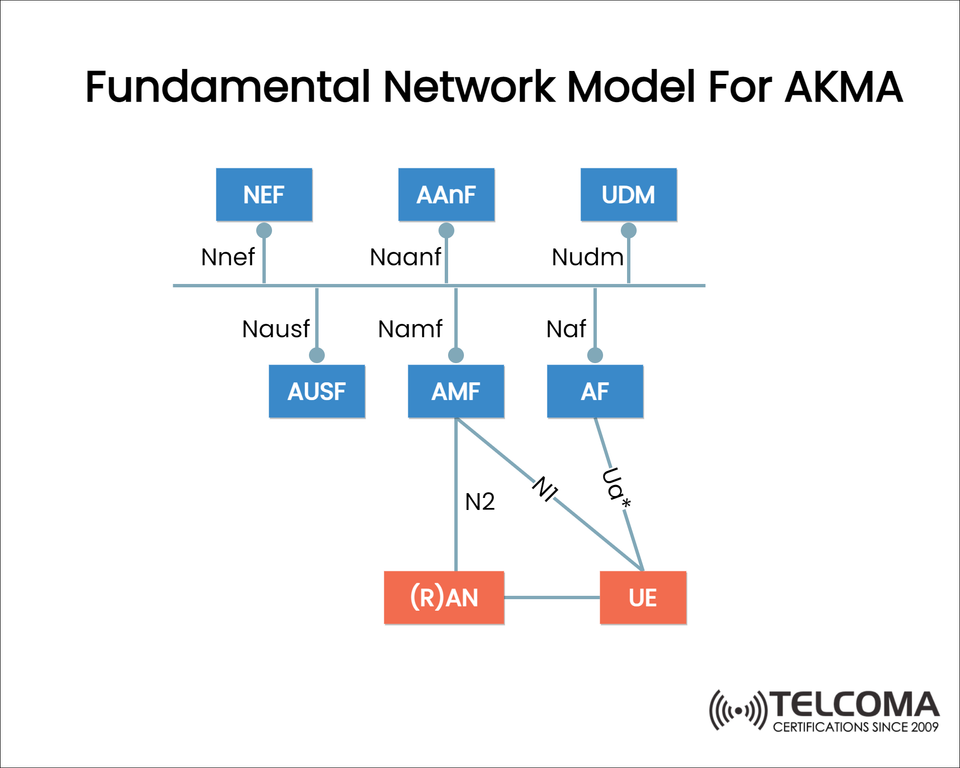

Fundamental Network Model for AKMA in 5G Security
The arrival of 5G networks has really changed the game in communication, offering ultra-low latency, high bandwidth, and the ability to connect tons of devices. But with these advancements, there’s a real need for strong security measures to keep user data safe and to allow trusted communication between network functions and applications.
One key solution is AKMA (Authentication and Key Management for Applications), which is outlined in 3GPP specifications. AKMA makes sure that applications and services can securely authenticate and exchange keys with user equipment (UE), all while keeping privacy intact and maintaining performance.
The diagram at the top shows the basic network model for AKMA, highlighting the different roles of network functions and their connections. In this post, we’re going to break down each part, explain how they communicate, and dive into how this model supports secure key distribution in 5G.
What is AKMA in 5G?
AKMA (Authentication and Key Management for Applications) is a framework introduced with 5G to ensure secure authentication and key derivation between network and application-level services. Unlike older systems that mainly focused on access authentication, AKMA broadens security to cover application functions (AFs), offering stronger protection for various 5G use cases like:
IoT systems with millions of devices
Smart city projects
Automation in Industry 4.0
Healthcare and remote operations
In simple terms, AKMA ensures that apps can rely on the same solid authentication foundation as the network itself.
Components in the AKMA Network Model
The diagram shows several key network functions that work together to make AKMA function. Let’s go through each one:
- UE (User Equipment)
Represents a mobile device, IoT device, or any endpoint.
Starts authentication requests and uses the derived keys for secure communication.
Interfaces: * UOa: Direct line to AF for application-level interactions. * N1/N2: Connects with AMF for mobility and signaling.
- (R)AN (Radio Access Network)
Supplies wireless connectivity between the UE and the 5G Core.
Links to the AMF through the N2 interface.
Helps transport the authentication signals to the core network.
- AMF (Access and Mobility Management Function)
Manages access and mobility in the 5G Core.
Interfaces: * Namf connects with AAnF * N2 links with (R)AN * N1 communicates with UE
Supports AKMA by handling signaling flows and enabling communication between UE and the other core functions.
- AUSF (Authentication Server Function)
Takes charge of user authentication.
Interfaces: * Nausf with AMF
Provides the K_AUSF key, which serves as the basis for deriving AKMA keys.
Ensures that only authenticated users can request keys.
- UDM (Unified Data Management)
Holds subscription and authentication data.
Interfaces: * Nudm with AMF
Gives AUSF the subscriber credentials it needs during authentication.
- AAnF (AKMA Anchor Function)
Central to the AKMA key distribution process.
Interfaces: * Naanf with AMF
Acts as the anchor for application-level authentication and key provisioning.
- AF (Application Function)
Represents application services (like video streaming, IoT platforms, or industrial apps).
Interfaces: * Naf with AAnF * UOa with UE
Utilizes the K_AF (application function key) to create secure communication with UE.
- NEF (Network Exposure Function)
Offers APIs and exposes network capabilities to outside applications.
Interfaces: * Nnef with AAnF
Plays a supporting role in AKMA by making sure that external application requests follow security policies.
Key Interfaces in the Model
InterfaceBetweenPurposeN1AMF ↔ UE Signaling and session managementN2AMF ↔ (R)AN Control signaling and mobility UOa AF ↔ UE Application-level communication Nausf AMF ↔ AUSF User authentication Nudm AMF ↔ UDM Subscriber data access Namf AMF ↔ AAnF Coordination for AKM ANafA AnF ↔ AF Application key provisioning NnefNEF ↔ AAnFAPI exposure for applications
How the AKMA Model Works
The AKMA model defines the flow step-by-step:
Primary Authentication: * The UE authenticates with the network via AUSF and UDM using subscription data. * A root key (K_AUSF) is created.
AKMA Anchor Key (K_AKMA): * From the K_AUSF, AUSF and AAnF derive an intermediate key (K_AKMA). * This key is specific to application authentication.
Application Function Key (K_AF): * AAnF generates K_AF for a particular AF. * The same key is shared with both AF and UE.
Secure Communication: * The AF and UE utilize K_AF to authenticate and set up secure sessions for application services.
Why is the AKMA Model Important in 5G?
The AKMA network model brings a lot to the table:
Enhanced Application Security: Apps no longer depend on weaker authentication methods.
Layered Key Hierarchy: Even if an application key gets compromised, root keys stay secure.
Service-Specific Keys: Each AF has its own key, so cross-service attacks are prevented.
Scalability: Can handle millions of devices and applications all at once.
Privacy Protection: User identities are kept safe using methods like SUCI.
Use Cases of AKMA
IoT Deployments: Keeping communication secure for sensors and actuators in smart factories.
Healthcare: Allowing secure remote monitoring and telesurgery.
Smart Cities: Securely managing keys for surveillance, traffic systems, and utilities.
Enterprise 5G: Private networks can securely authenticate enterprise apps using AKMA.
OTT Services: Streaming, gaming, or financial apps can integrate AKMA-based keys for added trust.
Step-by-Step Flow of AKMA Authentication
To get a better grasp of the fundamental network model, let’s break down the AKMA process:
Primary Authentication by UE
The UE connects with the network through the AUSF, using the credentials saved in the UDM.
A root key, known as K_AUSF, gets generated.
Deriving K_AKMA
The AUSF partners with the AAnF to create an intermediate AKMA Anchor Key (K_AKMA).
This key is unique to AKMA and serves as the base for deriving further keys.
Generating Application Function Key (K_AF)
The AAnF comes up with a service-specific key, called K_AF.
This key is securely distributed to both the UE and the Application Function (AF).
Secure AF-UE Communication
With K_AF in place, the AF and UE authenticate each other and set up an encrypted session.
This ensures that the application layer is just as secure as the network layer.
Conclusion
The fundamental network model for AKMA is a vital piece of 5G security architecture, ensuring that both the network and applications benefit from strong authentication and key management. By involving components like AUSF, AMF, UDM, AAnF, AF, NEF, and UE, the model guarantees that application keys (K_AF) are securely derived and distributed, keeping threats at bay while paving the way for scalable services.
For telecom professionals and enterprises, grasping the AKMA model is crucial for rolling out secure, application-focused services in the 5G world. As networks evolve to support IoT, healthcare, smart cities, and Industry 4.0, AKMA makes sure that security keeps pace with innovation.
