In-Depth Look at 5G Security Architecture: Components, Functions, and Layers

Focus on Security Architecture of 5G: A Guide for Telecom Professionals
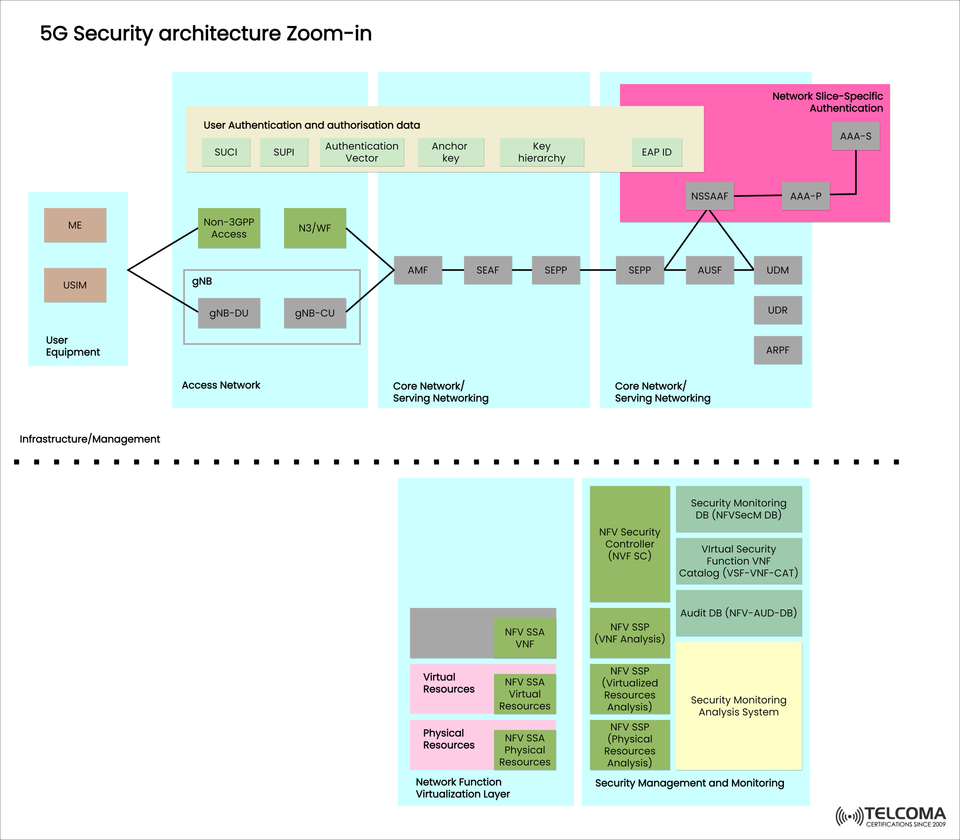
5G is expanding at an astounding pace across the globe, therefore it’s critical to have strong security mechanisms in place to protect user data, network resources and services allocated for a particular slice. This blog post looks at a zoomed-in perspective of the security architecture of 5G as illustrated in the diagram accompanying this article. We will break out some of the components from end-to-end, from User Equipment to Core Network, Network Function Virtualization (NFV), and Security Monitoring capabilities.
🔐 User Authentication and Authorization Mechanism
The security journey begins with the user authentication process which uses both existing and 5G identifiers:
SUCI (Subscription Concealed Identifier): Conceptually protects the SUPI upon first access.
SUPI (Subscription Permanent Identifier): Is the permanent identity of the subscriber.
Authentication vector and anchor key: Used for both cryptographic operations and session management.
The key hierarchy: Is the identifiers of encryption key and integrity keys at various layers.
EAP-ID: Used when the authentication procedures reference the Extensible Authentication Protocol (EAP).
🌐 Access Network: Security Entry Point
The Access Network is the first entry point in the experience chain and provides the initial secure access mechanism.
Key Components:
gNB (NextGen NodeB): The gNB comprises the gNB-DU (Distributed Unit) and the gNB-CU (Centralized Unit), solely for radio access networks.
Non-3GPP Access/N3WF: Non-3GPP Access offers support for the use of untrusted networks.
🔁 Core Network / Serving Networking
The Core Network plays a pivotal role in guaranteeing that the user identities and session management are executed within a secure operating environment.
Component Function
AMF Access and Mobility Management Function - UE registration and authentication occurs at this stage
SEAF Security Anchor Function - where the authentication exchanges are anchored.
SEPP: Security Edge Protection Proxy - protects PLMN signaling.
AUSF: Authentication Server Function - the validation is done at this stage.
UDM/UDR: Unified Data Management/Repository - subscriber profiles are stored.
ARPF: Authentication credential Repository and Processing Function - stores and manages the credentials.
🔒 Network Slice-Specific Authentication
5G networks allow network slicing, which enables different services to run on independent dedicated virtual networks.
Important Pieces to Consider:
NSSAAF: Network Slice Specific Authentication and Authorization Function.
AAA-S & AAA-P: Authentication, Authorization, and Accounting servers needs slice-specific policies and access control.
🧱 Network Function Virtualization (NFV) and Infrastructure
As previously highlighted, the infrastructure layer leverages virtualization to isolate resources and support secure baseline scalable operations.
NFV Layers:
Physical Infrastructure: This includes physical hardware components.
Virtual Infrastructure: This includes virtual machines, containers, etc.
NFV SSA VNF: Secure virtualized network functions.
Analysis Modules:
NFV SSP (Physical, Virtual, and VNF Analysis)
🛡️ Security Management and Security Monitoring Systems
Certainly, security does not stop at access or core but continues with monitoring and responding to incidents.
Important Components:
NFV Security Controller (NFV-SC): governs all NFV security.
Audit DB (NFV-AUD-DB): stores the Audit logs and audit trails.
The 5G security architecture is non-sequential, layered, module, with multiple types of authentication, connectivity security and resilience at either BSS or OSS level. Every step from USIM to NFV analysis applies a significant contribution to providing applications and users the connected networks and resilience it seeks. The core for every telco professional is to have knowledge about and be comfortable with the architecture, when considering 5G, am I deploying the architecture as a whole (as offered in a particular deployment) or am I deploying the architecture and responding to compliance obligations or security incidents prepared by specialized knowledge in the architecture?
- [x] Functional Details of the Security Components in 5G
- [x] Identity Protection: SUCI and SUPI
The protection of end-user identities in 5G (SUCI and SUPI) is a foundational upgrade to previous generations like LTE:
o SUPI is a temporary, specific and permanent identity (like IMSI in LTE), that CANNOT be sent in clear-text.
o SUCI is a temporary and none-clear-text version of SUPI, using the home operator public key. The flow of the protocol will ensure that if SUCI is intercepted, the original identity will NEVER be presented.
This process, just to add on, is ensuring privacy-by-design, as it uses asymmetric encryption, which also satisfies GDPR, if aligned with other regulatory structures. - [x] Authentication Process Using SEAF and AUSF
The 5G authentication flow can use 5G-AKA or EAP-AKA' protocols as below: - AMF, the anchor point, creates the initial authentication request and determines which authentication method will be used.
- Section 5g-SEAF, can access and connect to AUSF and offer the derived serving network key, to initiate and authenticate.
- AUSF uses what it receives back from the UE and searches the data from UDM (Unified Data Management) where the Subsciber,
🔄 SEPP – The Interconnect Protector
SECURITY EDGE PROTECTION PROXY (SEPP) is a really important addition in 5G:
It is used for secure inter-PLMN communication, particularly when roaming.
It provides end-to-end protection for signalling traffic (NAS/HTTP2).
It provides header enrichment and integrity for messages that cross trust boundaries.
Protection matters when each operator trusts an inter-operator or inter-network arrangement, particularly in a roaming scenario where the operators utilize each other's underlying infrastructure.
🧠 Security in Virtualized and Sliced Environment
Cloud-native approaches, which include, but aren't limited to, NFV and slices, have added layers of attack surface complexity that weren't in the legacy infrastructures.
🔍 Security layers of virtualization
Layer Security Function
Physical Resources Protected and isolated as part of the hardware root-of-trust and/or TPM modules.
Virtual resources Monitored for integrity, isolation violations
VNF Security Monitored for known or unknown vulnerabilities, compliance and patch level status.
Each security layer is continuously validated in an ongoing manner by NFV SSA (Security Service Assurance) as part of NFV SSP (Simulated Security Profiles) through the analysis engines.
🔭 Real-time Threat Monitoring and Audit Systems
5G is a proactive monitoring environment - leverages automation, analytics, and artificial intelligence (AI) to identify and adjudicate threats.
Key Security Monitoring Elements:
NFV SC (Security controller) include security control policy and multi-layered response to detected threats.
Security Monitoring database (NFVSeemDB) includes Virtual and Physical resource logs.
Audit Database (NFV-AUD-DB) includes Compliance, Traceability, and Event Correlation. VSF-VNF-CAT.
📌 Summary Table:
Major Functional Entities in 5G Security
Layer Key Entities Role
User Equipment ME, USIM User identity storage & initiation
Access Network gNB, N3IWF Connectivity & protocol protection
Core Network AMF, SEAF, AUSF, UDM, SEPP Access and Interconnect security and key management
Slice Security NSSAAF, AAA-S/P Security policy and access control specific to the entirety of slice context
NFV Infrastructure SSA VNF, SSP, SC Security of virtualization and orchestration
Monitoring Systems DBs, Catalogs Logging, compliance, threat detection
