Key Threats in Microwave Networks: Understanding Security Challenges and Countermeasures

Microwave networks are essential for today’s telecommunications, offering high-capacity, point-to-point wireless connections that enable everything from mobile backhaul and enterprise connectivity to defense and public safety communications.
Nonetheless, as the need for bandwidth and low-latency communication increases, so does the attack surface for these networks. With more connectivity and third-party integrations, microwave links face significant cybersecurity threats that could interrupt communications, compromise data, and jeopardize vital services.
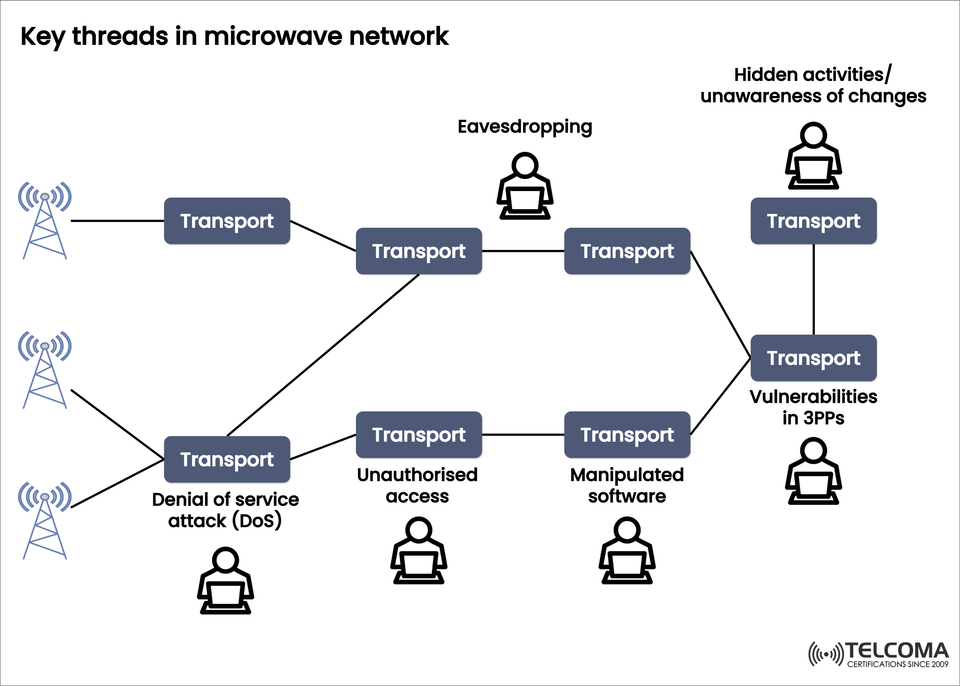
The image shared by Telcoma highlights the key threats facing microwave networks, which include denial-of-service (DoS) attacks, unauthorized access, eavesdropping, software manipulation, and vulnerabilities in third-party platforms (3PPs).
What is a Microwave Network?
Before diving into the vulnerabilities, it’s important to know what a microwave network actually is.
These networks utilize high-frequency radio waves (typically between 1 GHz to 60 GHz) to transmit data between fixed locations. They serve as the transport layer in telecommunications, capable of handling large volumes of voice, video, and data traffic over long distances.
Microwave links are crucial for:
Cellular backhaul (linking base stations to the core network)
Remote and rural communication
Emergency and defense communication systems
Enterprise private networks
Even though they are efficient and cost-effective, their wireless design leaves them susceptible to various cyber and physical threats.
Key Threats in Microwave Networks
The image outlines several attack types and weaknesses that could affect the transport layer of microwave networks. Here are the main threats, explained in detail.
Denial of Service (DoS) Attacks
Description:
A Denial of Service (DoS) attack inundates the microwave network with excessive traffic or harmful data, overloading its capacity and causing service disruptions.
Impact:
Network outages or performance degradation
Essential communication services becoming unavailable
Financial losses and diminished reliability
Example:
A coordinated DoS attack on telecom backhaul could incapacitate multiple base stations, disrupting entire mobile networks.
Countermeasures:
Install firewalls and intrusion prevention systems (IPS)
Adopt traffic filtering and rate-limiting policies
Utilize redundant network paths to keep the service running
Unauthorized Access
Description:
Unauthorized access happens when malicious actors take advantage of weak authentication or unsecured interfaces to infiltrate the microwave system.
Impact:
Tampering with configurations
Theft or manipulation of data
Injection of malware into the network
Example:
Attackers might exploit default credentials on a microwave transceiver to change routing parameters, redirecting sensitive data traffic.
Countermeasures:
Implement strong password policies and two-factor authentication
Keep firmware and access control lists up-to-date
Perform penetration testing to find security gaps
Eavesdropping
Description:
Eavesdropping refers to intercepting microwave signals or management data during transmission. Since microwave links operate on line-of-sight radio waves, attackers can potentially capture signals using specialized antennas.
Impact:
Exposure of confidential information (voice, video, or corporate data)
Breach of data privacy and regulatory compliance
Risk of blackmail or espionage
Example:
A hacker using a high-gain antenna to intercept data from a corporate microwave backhaul link could access unencrypted traffic.
Countermeasures:
Use end-to-end encryption (like AES, IPSec, or TLS)
Apply frequency hopping and spread spectrum techniques
Regularly check for signal anomalies or interference
Manipulated Software
Description:
Malicious alterations to software or firmware pose a serious risk in microwave systems. Attackers can modify genuine software updates or inject trojans for persistent access.
Impact:
Compromised system integrity and control
Unauthorized data manipulation or deletion
Long-term surveillance or backdoor access
Example:
If a compromised software update is pushed to a microwave node, it could give attackers remote control.
Countermeasures:
Confirm digital signatures and vendor authenticity for software updates
Use secure boot and version control processes
Deploy endpoint detection and response (EDR) solutions
Vulnerabilities in Third-Party Platforms (3PPs)
Description:
Many modern microwave systems connect with third-party management platforms, analytics tools, or network orchestrators. Any flaws in these components expose the entire network to risks.
Impact:
Data leaks via insecure APIs
Reliance on unpatched software
Increased risk of supply-chain attacks
Example:
An attacker exploiting a flaw in a third-party network management system could access sensitive operational data.
Countermeasures:
Perform third-party risk assessments
Ensure vendors align with ISO 27001 and NIST standards
Promptly apply security patches and updates
Hidden Activities / Unawareness of Changes
Description:
Sometimes, unauthorized network activities or configuration shifts go unnoticed, especially in extensive, multi-node microwave setups.
Impact:
Unseen data breaches or malicious reconfigurations
Network instability and performance issues
Delays in responding to active threats
Countermeasures:
Use real-time monitoring and anomaly detection tools
Keep detailed change logs and audits
Implement AI-driven network visibility solutions for early threat detection
Why Security in Microwave Networks Matters
Microwave networks carry mission-critical data for telecom operators, the defense sector, and enterprises.
Even a short security lapse can lead to:
Service disruptions across regions
Breach of customer data confidentiality
Reputational damage and regulatory penalties
As 5G, IoT, and smart infrastructure rely heavily on microwave and millimeter-wave transport, ensuring robust cybersecurity has become a fundamental operation.
Best Practices for Securing Microwave Networks
Implement Layered Security: Utilize a defense-in-depth approach—protect data at the physical, transport, and management levels.
Regular Security Audits: Carry out vulnerability assessments and penetration testing.
Zero-Trust Architecture: Continuously verify every device and connection.
Network Segmentation: Isolate critical assets from public or less-secure segments.
AI and ML-based Monitoring: Leverage predictive analytics to catch anomalies early.
Employee Training: Ensure network engineers are familiar with cyber hygiene and compliance requirements.
Vendor Collaboration: Collaborate with equipment providers to maintain firmware security and patch management.
Future Outlook: Securing the Next-Gen Microwave Transport
As telecom moves toward 6G and ultra-low-latency communication, microwave transport will be crucial in backhauling small cells, IoT devices, and edge computing nodes.
Future security efforts will likely focus on:
AI-driven threat prediction
Quantum-safe encryption
Blockchain-based authentication
Federated security management across multiple operators
In short, tomorrow’s microwave networks need to be intelligent, adaptive, and self-defending.
Conclusion
The Telcoma illustration of the key threats in microwave networks serves as a reminder that even the most advanced transport technologies only hold up as well as their weakest link.
From denial-of-service attacks and unauthorized access to hidden vulnerabilities in third-party software, the risks are real and escalating.
Yet, with strong encryption, continuous monitoring, layered defense, and AI-based security frameworks, telecom operators can create resilient, secure, and future-ready microwave communication systems.
