NG-RAN and 5G Core Entities Explained: Identifiers, Bearers, and Architecture
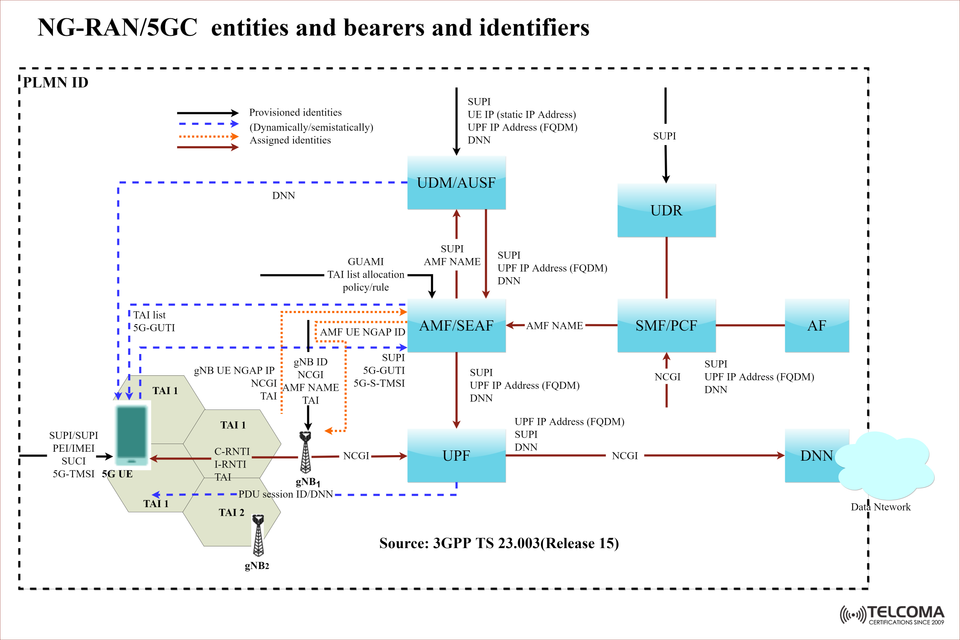

Identifying and understanding the components and identifiers associated with the NG-RAN and the 5G Core (5GC) is essential for engineering and technical professionals involved in next-gen networks as 5G networks will be the primary platform for the future of communication. The identifying diagram found in the (3GPP TS 23.003 Release 15) is a valuable tool in explaining what the various entities do, how they interconnect, what the identifiers do for them, and how the bearers are allocated to maintain sustained and reliable high-speed connectivity.
- Overview of NG-RAN and the 5G Core
The NG-RAN contains the radio access layer of 5G technology, linking User Equipment (UE) to the 5G Core (5GC) using the authorized 5G identifiers. The 5G Core uses a Service-Based Architecture (SBA) that facilitates flexible deployments in a virtualized manner. Together, the NG-RAN and 5GC entities manage identifiers, bearers, and security to achieve seamless end-user mobility and session continuity. - The Components in the Architecture
Radio Access Network (RAN) Components:
5G UE - a mobile device communicating with the gNB.
gNB - 5G Base station that can be broken down into gNB-CU and gNB-DU, specifying control plane and user plane functions.
5G Core Network Functions:
AMF/SEAF - Access and Mobility Management Function / Security Anchor Function. Addresses registration, connection management, and authentication.
SMF/PCF - Session Management Function / Policy Control Function. Provides session establishment and quality of service along with enforcing policies.
UPF - User Plane Function that routes user data to external networks.
- Identifiers in NG-RAN/5GC
5G networks utilize numerous identifiers to guarantee the unique identification of devices, sessions, and locations:
Identifier Definition
SUPI Subscription Permanent Identifier - unique user identity within 5G.
SUCI Subscription Concealed Identifier - an encrypted SUPI for privacy.
5G-GUTI 5G Globally Unique Temporary Identifier - a temporary identity for mobility management.
NCGI NR Cell Global Identifier - identifies a specific cell within the network.
TAI Tracking Area Identifier - logical group of cells for mobility management.
C-RNTI/I-RNTI Radio Network Temporary Identifiers for user equipment scheduling and control.
UPF IP / UE IP IP addresses for user plane and UE communication, respectively.
- Bearers and data flow
Bearers define the path for packets of user data to flow between a UE to an external network, as can be seen in the definitions of the following bearers which are dynamically assigned:
PDU Sessions - Provides end-to-end data connectivity
QoS Flows - Allocates resources to the bearers to facilitate application requirements
In the figure, you can observe the dynamically assigned identifiers (the blue dashed lines), the provisioned identifiers (the black lines), and the assigned identities (the red dotted lines), while maintaining the data flow path and the control path.
- Interactions between entities
The diagram shows:
The UE requests user authentication by sending the SUPI/SUCI to the AMF through the gNB.
The AMF coordinates authentication with the UDM/AUSF.
The SMF and UPF are managed by the PDU session, while the DNN is used to access the external data.
- The Value of All This for Telecom Professionals
Knowledge of these entities and identifiers allows for straightforward:
Real-time troubleshooting for production networks
Efficient mobility and load-balancing network planning
Security measures to lessen identifier visibility and use encryption
Better quality of service through better bearer mapping
Summary
NG-RAN and 5G Core architecture constitutes a highly integrated framework of entities, identifiers and bearers. When subscribers' identities and associated identifiers(s) are managed securely, the assigned data connections are routed appropriately, and all policies are enforced dynamically, the demand for ultra-speed low-latency applications can be satisfied in 5G networks.
For telecom engineers in particular, redefining the deployment and maintenance of next-generation mobile networks requires mastery of these concepts.
Extended Blog Content
7. Identifier lifecycle: 5G
In 5G, identifiers aren't really static; they are actively managed through phases of a lifecycle in order to preserve user privacy, provide uninterrupted mobility, and provide connection stability.
The lifecycle is made up of the following stages:
Provisioning - The SUPI is provisioned in the UDM during subscription creation.
Registration - The UE sends the encrypted SUPI as SUCI to the AMF to hide the permanent identifier.
Session Setup - Temporary identifiers include 5G-GUTI and C-RNTI.
Handover - The NCGI and TAI change as the UE moves, or hands-over, between gNBs.
Session Release - The temporary identifiers are released to avoid re-use.
Privacy note: the ability to conceal the SUPI using SUCI is a significant improvement with 5G.
- NG-RAN to 5GC Signaling Flow
When we look at the signalling between the NG-RAN and 5GC in a real operational environment, we can envisage signalling scenarios like this:
From UE to gNB
The UE sends the SUCI and makes the connection request.
The gNB assigns the UE with a C-RNTI for RRC communication.
From gNB to AMF
The gNB sends the UE’s request and the NCGI.
The AMF authenticates with AUSF/UDM.
From AMF to SMF
The AMF requests PDU session creation.
The SMF assigns an IP address and UPF path and respondent.
From SMF to UPF
The SMF establishes a user plane tunnel (e.g. GTP-U).
The UPF will connect to a DNN for external network access.
And Then Data Transfer:
The UE sends and receives user data through QoS flows, which are mapped to bearers to inform the NG-RAN and 5GC of intended service quality.
- Real-world telecom use cases
5G Standalone (SA) Networks – All the NG-RAN and 5GC components as AMF, SMF, and UPF are used.
5G Non-Standalone (NSA) Deployments - Partially integrated NG-RAN with LTE EPC.
Private 5G Networks – Custom identifier schemes for enterprise security.
Network Slicing – Distinct identifiers and bearers will be used for each service slice. - Important Benefits of 5G Identifier and Bearer Management
Improved Security - The use of SUCI (encryption) and temporary ID's.
Mobility Optimisation - Reducing session drops due to handovers being smoother.
Scalable Policy Control - By PCF being able to dynamically enforce QoS constraints on a per-session basis.
Optimising Data routing - By the UPF being able to provide traffic paths with low latency.
