Non-Roaming 5G Core Architecture with Untrusted Non-3GPP Access Explained
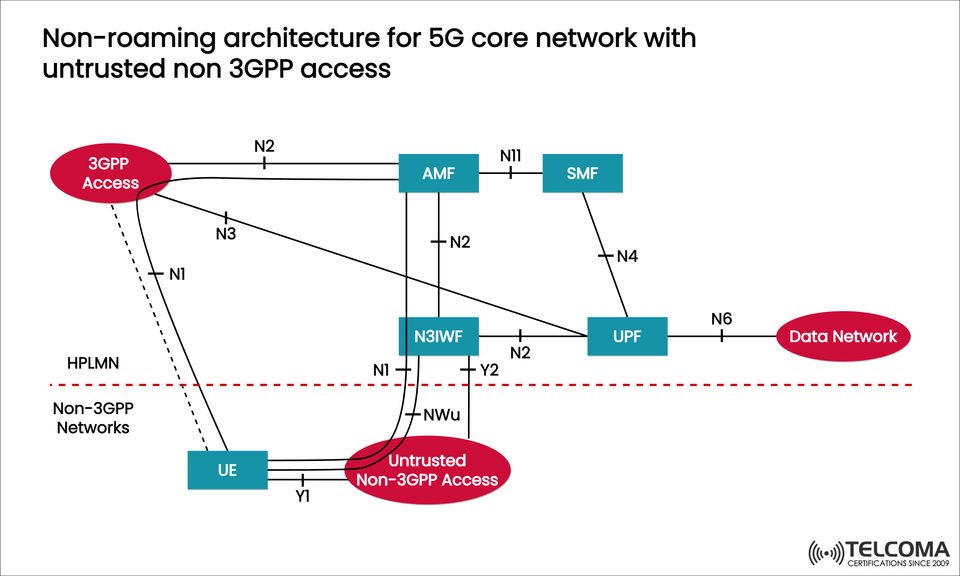

Non-Roaming Architecture for 5G Core with Untrusted Non-3GPP Access
5G isn’t just about mobile connections through traditional 3GPP networks like NR and LTE. A major aspect of the 5G Core (5GC) is its ability to work with non-3GPP access networks, including Wi-Fi, fixed broadband, or enterprise LANs. When these networks can't be fully trusted, we use a framework called untrusted non-3GPP access.
In the image above, you can see the non-roaming architecture of the 5G core network with untrusted non-3GPP access. At its heart is the Non-3GPP Inter Working Function (N3IWF), which ensures secure communication between user devices (UE) and the 5GC.
This architecture is crucial for providing seamless mobility, security, and continuity of service across various access technologies.
Why Non-3GPP Access is Important in 5G
While 5G New Radio (NR) gives us super reliable wireless connectivity, there are situations where we don’t need—or can’t rely exclusively on—cellular access. Many devices connect via Wi-Fi hotspots, enterprise networks, or fixed broadband, especially indoors or on campuses.
But not all of these networks are fully secure. For instance:
A public Wi-Fi hotspot might not offer strong encryption.
Enterprise Wi-Fi can have mixed security standards.
Broadband access may skip critical core network authentication layers.
In these instances, the 5GC uses untrusted non-3GPP access to enforce strict security and authentication without compromising connectivity.
Key Components of the Architecture
The diagram outlines how 3GPP access, untrusted non-3GPP access, and the 5GC connect. Let's break down the main parts:
- User Equipment (UE)
Connects through either 3GPP access (NR/LTE) or untrusted non-3GPP access (Wi-Fi/broadband).
Uses the Y1 and NWu interfaces to talk to the untrusted access network.
Sets up secure tunnels to the N3IWF before connecting to the 5G Core.
- Untrusted Non-3GPP Access
Refers to access networks that the operator doesn’t control.
Includes public Wi-Fi, unmanaged enterprise LANs, or broadband.
Needs extra security measures since the access infrastructure can’t be fully trusted.
- Non-3GPP InterWorking Function (N3IWF)
The main gateway for untrusted access in 5G.
Creates secure IPsec tunnels between UE and 5GC.
Handles authentication via the N1 interface (control plane) and sends NAS signaling to the AMF.
Manages user plane traffic via the UPF (through N3).
- Access and Mobility Management Function (AMF)
Connects to UE (through N1 and N2 signaling) for managing mobility.
Makes sure that if a device switches from Wi-Fi to 5G NR, the session stays connected.
- Session Management Function (SMF)
Oversees user sessions and policies.
Works alongside AMF and UPF to set up sessions when UE connects through untrusted access.
- User Plane Function (UPF)
Manages user data traffic (using N3 and N6 interfaces).
Connects the UE traffic to external Data Networks (DN), like the internet, enterprise applications, or cloud services.
- Data Network (DN)
The final stop for user traffic.
Can be the public internet, enterprise servers, or specialized 5G services.
Interfaces in the Architecture
InterfaceFunctionConnectionN1NAS signaling between UE and AMF (via N3IWF)UE ↔ N3IWF ↔ AMFN2Control signaling AMF ↔ N3IWF / UPFN3User plane tunnelN3IWF ↔ UPFN4Session control SMF ↔ UPFN6Data routing UPF ↔ Data NetworkN11Session management AMF ↔ SMF NWu Secure IPsec tunnel setup UE ↔ N3IWFY1, Y2UE communication with non-3GPP access UE ↔ Untrusted Access
These interfaces make sure that both the control plane and user plane traffic are authenticated, encrypted, and routed correctly.
How Security is Maintained
Given that the access network is untrusted, security is crucial:
IPsec tunnels are set up between UE and N3IWF for data confidentiality.
EAP-AKA’ authentication checks the subscriber’s details.
The N3IWF serves as the security anchor, blocking unauthorized access to the 5G Core.
This layered approach keeps the 5G core safe, even if a Wi-Fi network is compromised.
Benefits of Untrusted Non-3GPP Access in 5G
Integrating untrusted access brings a bunch of advantages:
✅ Wider coverage: UE can connect over Wi-Fi or broadband where 5G NR isn't available.
✅ Smooth mobility: Handover between Wi-Fi and cellular networks without losing sessions.
✅ Boosted security: Untrusted networks can still be secured through N3IWF and IPsec.
✅ Traffic offloading: Operators can ease cellular spectrum congestion by using Wi-Fi.
✅ Enterprise readiness: Businesses can seamlessly bring their broadband/Wi-Fi networks into the 5GC.
Example Use Cases
Public Wi-Fi Offload – Mobile providers can send smartphone data through Wi-Fi hotspots while keeping it secure.
Enterprise IoT – IoT devices on enterprise Wi-Fi can securely connect to the 5G core.
Fixed Wireless Access Integration – Broadband lines can link with the 5GC for unified management and policy enforcement.
Indoor Coverage – Seamless connection inside buildings where 5G radio signals might be weak.
Trusted vs Untrusted Non-3GPP Access
Aspect Trusted Non-3GPP Access Untrusted Non-3GPP Access Example Managed enterprise Wi-Fi Public Wi-Fi, unmanaged LANs Gateway Trusted Non-3GPP Gateway (TNGF)N3IWFSecurityControlled by operator Secured via IPsec tunnels Use Case Enterprise private networks Public hotspots, residential broadband
This distinction is key because operators can use either mode depending on where the access is happening.
Conclusion
The non-roaming architecture for 5G core with untrusted non-3GPP access is a foundational aspect of 5G’s vision for universal connectivity. By utilizing the N3IWF and secure tunneling protocols, 5GC can expand its services to Wi-Fi and broadband networks that aren’t inherently trusted.
This ensures service continuity, stronger security, and flexible access options for users, while allowing operators to enjoy spectrum efficiency and lower network load.
As 5G keeps advancing, blending cellular and non-cellular access networks will be essential for creating a truly integrated and smart network ecosystem.
