Open RAN Security Challenges: Risks, Concerns, and Solutions

Tackling Security Challenges in Open RAN: Risks, Concerns, and Solutions
The emergence of Open Radio Access Networks (Open RAN) marks a significant shift in telecom infrastructure. By breaking down RAN functions and promoting open interfaces, Open RAN fosters innovation, reduces vendor lock-in, and supports multi-vendor ecosystems. But with this openness comes a rise in security risks.
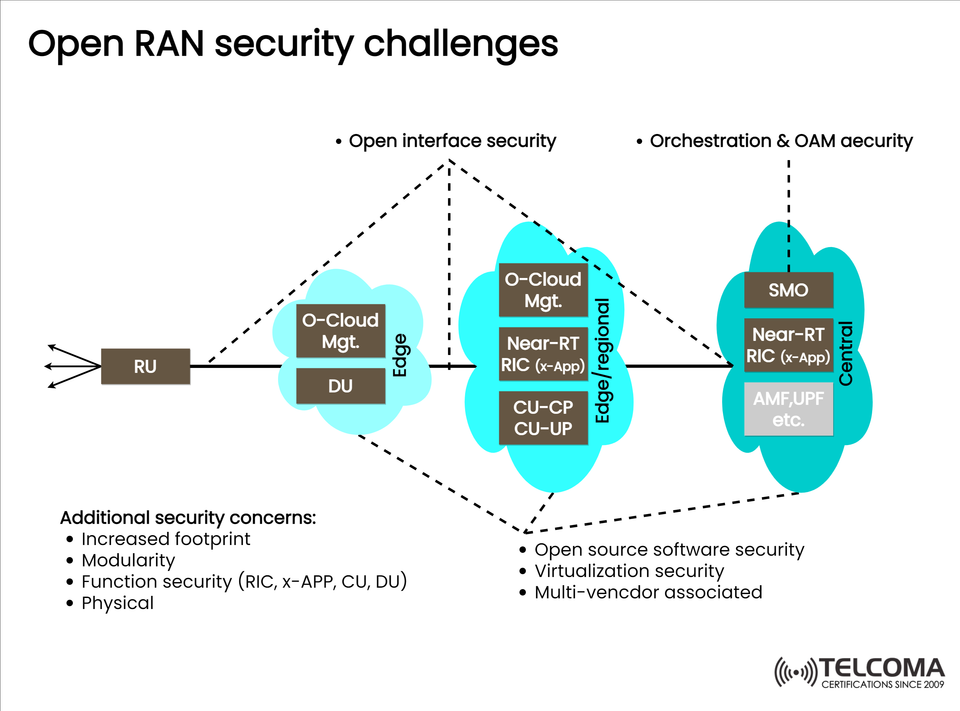
The diagram above illustrates several key security concerns across edge, regional, and central domains, including issues related to open interfaces, orchestration, O-Cloud management, and virtualization. For telecom operators, it's crucial to tackle these challenges to maintain network reliability, integrity, and trust.
In this article, we'll delve into the security challenges of Open RAN, their root causes, and possible ways to address them.
The Importance of Security in Open RAN
Unlike traditional RAN, which had functions tightly integrated under a single vendor, Open RAN distributes these functions across RU, DU, CU, and RIC hosted on the O-Cloud (Open Cloud Infrastructure).
Benefit: This openness allows for modular setups, collaboration among multiple vendors, and faster innovation.
Drawback: However, this broader setup and dependence on open interfaces can increase the attack surface, making security a primary concern.
In Open RAN, if one area is compromised, it can affect the entire network—from the Radio Unit (RU) at the edge to the Core and Service Management Orchestration (SMO) in the central layer.
Major Security Challenges in Open RAN
The diagram provided highlights a number of vulnerabilities throughout the architecture. Let’s break these down:
- Open Interface Security
Open RAN depends on standardized open interfaces (like fronthaul between RU and DU or midhaul between DU and CU).
Threat: Open interfaces, while they enable interoperability among vendors, are susceptible to man-in-the-middle (MITM) attacks, data interception, and protocol vulnerabilities.
Scenario: If attackers gain control over the RU ↔ DU link, they could disrupt signaling or inject harmful traffic.
Prevention: Implementation of strong encryption, authentication, and constant monitoring of interface traffic is necessary.
- Orchestration & OAM Security
The SMO (Service Management and Orchestration) layer orchestrates RAN, CN, and MEC operations.
Threat: Given that SMO manages policies, orchestration, and life-cycle management, a breach in this layer could lead to misconfigurations or unauthorized access throughout the network.
Issue: Integration with third-party APIs can introduce vulnerabilities.
Prevention: Employing zero-trust models, securing APIs, and implementing role-based access control are crucial.
- O-Cloud Management Vulnerabilities
O-Cloud is where the virtualized DU, CU, and RIC functions operate.
Threats:
Misconfigurations in cloud orchestration layers.
Exploitable hypervisor vulnerabilities.
Attackers moving laterally across virtual machines (VMs).
Impact: If O-Cloud is compromised, it could expose multiple network functions all at once.
Prevention: Adopt hardened cloud security practices, constant vulnerability assessments, and hardware-based security measures (like TPM or HSM).
- Open Source Software Security
Open RAN relies significantly on open-source software for its flexibility and cost-effectiveness.
Threats:
Open-source code can be vulnerable to issues that aren’t yet discovered.
Attackers may exploit weaker components maintained by the community.
Prevention: Regular updates, implementing SBOM (Software Bill of Materials), and thorough validation of open-source dependencies are necessary.
- Virtualization Security
Virtualization forms the backbone of O-Cloud, allowing for the flexible deployment of CU, DU, and RIC.
Threats:
Vulnerabilities in hypervisors and containers.
Misconfigurations that allow lateral movement for attackers.
Prevention: Secure container orchestration (like Kubernetes hardening), runtime protection, and continuous monitoring of workloads are vital.
- Multi-Vendor Ecosystem Challenges
Open RAN’s strength—multi-vendor flexibility—also presents security challenges.
Threat: Different vendors can have various levels of security practices, complicating end-to-end accountability.
Issue: Pinpointing the source of a breach in a multi-vendor context can be tough.
Prevention: Establish standardized security compliance frameworks for vendors, certifications, and strict SLAs (Service-Level Agreements).
- Increased Footprint and Modularity
By breaking RAN into RU, DU, CU, and RIC components, Open RAN heightens the attack surface.
Threat: More interfaces, hardware units, and distributed setups mean more entry points for potential attackers.
Prevention: Conduct end-to-end security audits, consistently manage configurations, and use comprehensive monitoring systems.
- Function Security (RIC, xApps, CU, DU)
The RIC (RAN Intelligent Controller) plays a central role in Open RAN, hosting xApps (near-RT) and rApps (non-RT) for optimization.
Threat: Malicious or poorly designed xApps could interfere with RAN functionality.
Prevention: Application sandboxing, thorough code reviews, and runtime integrity checks are essential.
- Physical Security Risks
With more distributed units deployed at the edge (like RU, DU), concerns about physical tampering arise.
Threat: Attackers could gain access to hardware located in less secure areas.
Prevention: Utilize tamper-proof devices, secure boot mechanisms, and restrict physical access.
Summary of Security Concerns
Security Area Risks Mitigation Measures Open Interfaces MITM, data interception, spoofing Encryption, authentication, monitoring Orchestration & OAM Unauthorized access, misconfiguration Zero-trust models, secure APIs, RBACO-Cloud Management VM exploits, misconfigurations Hardened cloud security, TPM, audits Open Source Software Vulnerabilities in community code Regular patching, SBOM, validation Virtualization Hypervisor/container vulnerabilities Kubernetes hardening, runtime monitoring Multi-Vendor Setup Varied vendor practices, accountability Standard compliance, SLAs Increased Footprint Larger attack surface End-to-end monitoring, config management RIC/x App Security Malicious apps, RAN manipulation Sandboxing, code review Physical Security Hardware tampering Tamper-proof devices, secure boot
Strategies for Securing Open RAN
To tackle the challenges mentioned above, telecom operators and vendors should implement a multi-layered, proactive security strategy:
Zero-Trust Framework: Never assume trust between any network component.
Automation-Driven Security: Leverage AI and machine learning for anomaly detection to preemptively defend against threats.
Vendor Certification: Ensure vendors meet security standards based on guidelines from 3GPP and O-RAN Alliance.
Closed-Loop Security: Integrate security measures into orchestration workflows for real-time remediation.
Ongoing Auditing: Regular compliance checks and penetration testing are vital.
Future of Open RAN Security
As the adoption of Open RAN speeds up, security frameworks will continue to develop. The O-RAN Alliance and 3GPP are actively working on:
Better specifications for open interfaces.
Security guidelines for RIC applications.
Models of shared responsibility between operators and vendors.
New technologies like confidential computing, AI-enhanced security analytics, and blockchain-based trust models will bolster Open RAN security even further.
Wrap-Up
Open RAN signifies a major evolution in telecom networks, promoting innovation and flexibility through openness and modularity. However, this openness also gives rise to distinct security challenges—from open interface vulnerabilities to issues of multi-vendor accountability and virtualization risks.
To fully tap into the potential of Open RAN while minimizing risks, operators need to adopt comprehensive, multi-layered security strategies that integrate cloud-native protections, zero-trust principles, and ongoing monitoring.
The future of telecom will be open, intelligent, and software-driven—but only if security is treated as a fundamental component right from the start.
