SDN Enabled Authentication Model: Enhancing Security and Speed in Next-Gen Networks

SDN-Enabled Authentication Model: Ensuring Secure and Efficient Access in Today’s Networks
As we rapidly advance with 5G, IoT, and edge computing, the way we authenticate has become a vital part of both network security and user experience. With billions of devices now linking to telecom networks, traditional authentication methods are facing hurdles like latency, scalability, and handover delays.
This is where Software-Defined Networking (SDN) comes into play. By separating the control layer from the data layer, SDN injects programmable intelligence into the network, allowing for dynamic, secure, and efficient authentication processes.
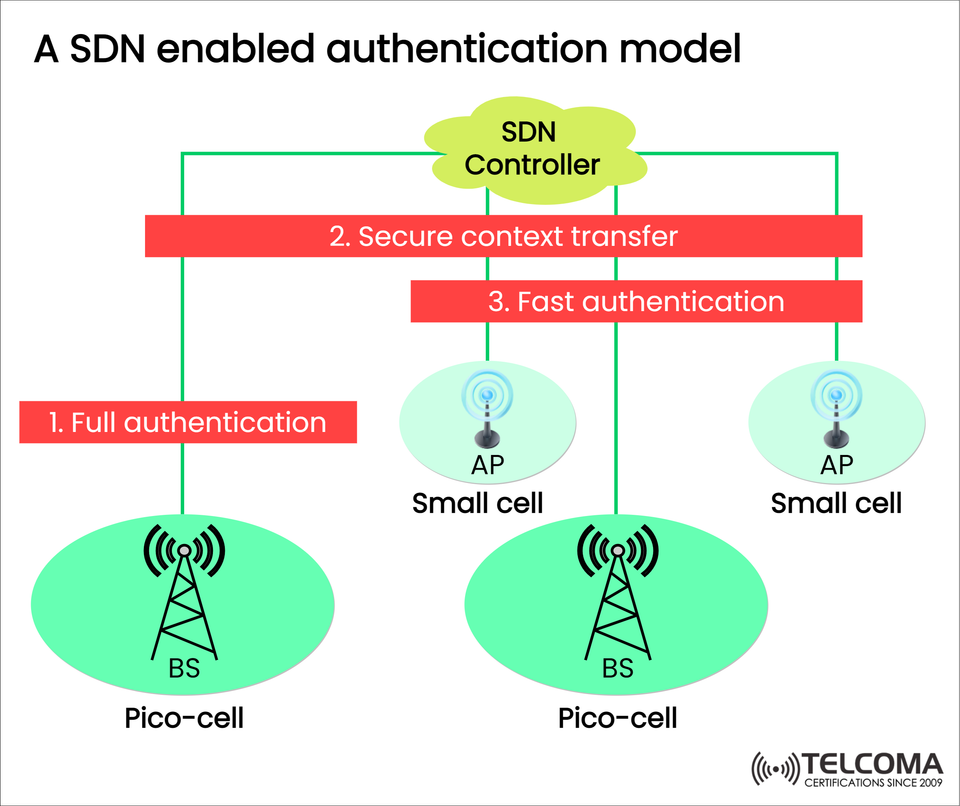
The image provided illustrates a SDN-enabled authentication model, showing how complete authentication, secure context transfer, and rapid authentication collaborate to enhance user mobility and security.
What is SDN in Network Authentication?
Software-Defined Networking (SDN) separates control logic from hardware, centralizing it in an SDN controller. In terms of authentication, this means:
Centralized Policy Management: A central controller takes care of all authentication rules.
Flexibility: You can change authentication methods without needing new hardware.
Scalability: It can support millions of devices by intelligently managing authentication.
Mobility Support: Ensures smooth transitions between different cells with minimal delays.
The SDN-Enabled Authentication Model: An In-Depth Look
The image highlights three key processes in the authentication flow:
Full Authentication (Initial Authentication)
Secure Context Transfer
Fast Authentication (Subsequent Access)
Let’s dive into each one.
- Full Authentication
When a user first connects to the network through a pico-cell base station (BS), it kicks off a full authentication process.
This involves checking the user’s credentials against the core authentication server.
It usually relies on standard security frameworks like EAP-AKA, EAP-TLS, or SIM-based authentication.
Once confirmed, a secure session is established between the user’s device and the network.
Although full authentication ensures robust security, it can be time-consuming if repeated at every handover. That’s where SDN helps streamline things.
- Secure Context Transfer
After the initial authentication, the SDN controller takes on an important role.
The user’s authentication context (which includes keys, session info, and trust state) is securely passed to other cells within the network.
This eliminates the need for re-authentication with each handover.
The SDN controller enforces security policies centrally, ensuring uniformity.
This secure transfer enables low-latency mobility, crucial for 5G applications like autonomous vehicles, AR/VR, and industrial IoT.
- Fast Authentication
Once the secure context is shared, fast authentication allows users to connect quickly to new access points (APs) or small cells.
Instead of performing a complete cryptographic handshake, the network checks the session using previously shared keys.
The SDN controller ensures the trustworthiness of the session continuity.
This cuts down authentication delays from several seconds to just milliseconds.
Fast authentication is vital in areas with dense small cell deployments, like smart cities, factories, and transportation hubs.
Why SDN Enhances Authentication
The SDN-enabled model brings significant advantages over traditional authentication systems:
Centralization: One SDN controller manages all authentication policies, cutting down on inconsistencies.
Flexibility: Policies can be easily updated through software, making it easier to adapt to new devices and standards.
Mobility: Facilitates seamless handovers between pico-cells and small cells.
Efficiency: Reduces unnecessary authentication steps, enhancing QoS (Quality of Service).
Security: Offers strong encryption during context transfer and helps prevent replay attacks.
Applications in Telecom Networks
This model shines in next-generation mobile and enterprise networks:
5G Networks: Supports ultra-reliable low-latency communication (URLLC) by cutting delays during mobility.
IoT Ecosystems: Effectively authenticates billions of devices without causing bottlenecks.
Enterprise Networks: Ensures secure roaming over large campuses or smart factories.
Public Wi-Fi Offloading: Makes secure transitions between cellular and Wi-Fi access points simpler.
Healthcare: Facilitates seamless authentication for wireless body area networks (WBANs) in telemedicine.
Comparison: Traditional vs. SDN-Enabled Authentication
Feature Traditional Authentication SDN-Enabled Authentication Initial Setup Full handshake for every access Only once (full authentication)Mobility Support High delay during handovers Seamless with fast authentication Scalability Limited by distributed hardware Centralized & scalable with SDN Policy Updates Complex, hardware-dependent Simple, software-defined Security Secure but repetitive Secure with context transfer
Challenges in SDN-Enabled Authentication
While it’s a powerful model, there are also some challenges:
Controller Bottleneck: Centralized control might hit scalability limits if not properly optimized.
Security Risks: If the SDN controller is compromised, it puts the entire system at risk.
Interoperability: Needs to work with legacy systems and standards.
Complexity: Initial deployment can be trickier than traditional setups.
The Future of SDN-Enabled Authentication
The future of authentication will continue to be influenced by SDN, AI, and the advancements in 5G/6G. Here are some possible directions:
AI-Powered Authentication: Leveraging machine learning to spot anomalies and threats.
Blockchain Integration: Decentralized trust models for secure context transfer.
6G Networks: Ultra-fast authentication thanks to terahertz communication and massive IoT support.
Zero Trust Models: Ongoing validation instead of one-off authentication.
Real-World Case Study: Using SDN for Authentication in Telecom Networks
Many telecom operators around the world are looking into or already applying SDN-enabled authentication models to tackle the challenges posed by 5G and beyond. Let’s check out a couple of real-life examples.
- AT&T’s Shift to SDN
AT&T has been leading the way in using SDN to virtualize its core network functions.
Challenge: As they rapidly rolled out small cells for 5G, AT&T had to come up with faster and more secure authentication methods for mobile users jumping between pico-cells and Wi-Fi.
Solution: They implemented an SDN controller to centralize policy management, allowing for context-aware authentication.
Impact: This move cut down latency during handovers, enhanced the customer experience for streaming and gaming, and made it easier to integrate IoT devices.
Conclusion
The SDN-enabled authentication model is changing the game for how we manage authentication in modern telecom networks. By integrating full authentication, secure context transfer, and fast authentication, it guarantees both security and efficiency for users on the go.
For those in the telecom field and tech enthusiasts, getting a grip on this model is vital as networks grow denser, more mobile, and increasingly security-focused. With the maturation of 5G and 6G on the horizon, SDN will continue to play a key role in developing secure, scalable, and flexible authentication systems.
