Security Threats in 5G: Device, RAN, MEC, and Core Network Risks Explained

The Importance of 5G Security
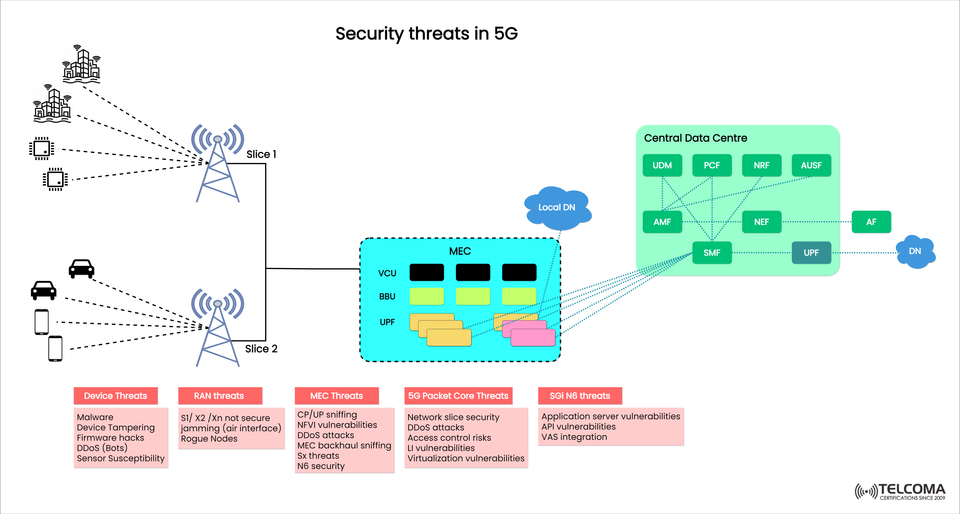
5G is shaking up the digital landscape with its ultra-low latency, massive IoT connectivity, and network slicing that enables tailored services. But with these advancements come new risks, giving cybercriminals even more opportunities. Unlike earlier networks, 5G uses cloud-native infrastructure, virtualization, and edge computing, which can lead to new vulnerabilities across devices, radio access networks (RAN), mobile edge computing (MEC), and the 5G core network.
In this article, we’ll dive into the major security threats in 5G networks, referencing the layered risks shown in the diagram, and share insights aimed at telecom professionals and tech enthusiasts.
Device-Level Threats in 5G
Devices are the frontline of the 5G ecosystem. With billions of IoT sensors, smartphones, and connected vehicles depending on 5G, any weak security at the device level could jeopardize the whole network.
Main device threats include:
Malware: Harmful software that can take over device functions.
Device Tampering: Unauthorized modifications to hardware that allow exploits.
Firmware Hacks: Attacks targeting the firmware, often slipping under the radar of standard security tools.
DDoS (Bots): Compromised IoT devices forming botnets that can flood networks.
Sensor Vulnerabilities: Taking advantage of weak or unencrypted data from IoT sensors.
Example: A hacked IoT camera could end up being part of a botnet used for DDoS attacks, disrupting essential 5G services.
RAN (Radio Access Network) Threats
The RAN connects devices to the 5G core through base stations and spectrum. Because it’s wireless and exposed, attackers might exploit weaknesses in signaling and communication channels.
Key RAN threats consist of:
S1/X2/Xn Insecurity: Interfaces that might not have solid encryption.
Jamming (Air Interface Attacks): Disrupting wireless signals to deny service.
Rogue Nodes: Fake base stations (IMSI catchers) that trick devices into connecting, paving the way for eavesdropping.
Example: Rogue base stations might intercept sensitive business communications, creating privacy and espionage risks.
MEC (Mobile Edge Computing) Threats
MEC brings cloud computing closer to the network edge, allowing for ultra-low latency in applications like self-driving cars and AR/VR. While it’s powerful, MEC also introduces more vulnerabilities.
Significant MEC threats include:
CP/UP Sniffing: Interception of control plane/user plane traffic.
NFVI Vulnerabilities: Weak spots in the Network Functions Virtualization Infrastructure (NFVI).
DDoS Attacks: Distributed denial of service aimed at edge servers.
MEC Backhaul Sniffing: Capturing data between MEC nodes and the core.
Sx Threats: Issues with insecure session management and signaling channels.
N6 Security Risks: Vulnerabilities in connections from MEC to the internet.
Example: A compromised MEC node could alter AR data in real-time, posing safety risks in fields like industrial automation.
5G Packet Core Threats
The 5G core is built on a cloud-native Service-Based Architecture (SBA), which boosts scalability but also comes with new hazards. It links network functions like AMF, SMF, UDM, PCF, and UPF.
Core network threats are:
Network Slice Security: Each slice needs to be isolated; weak isolation can lead to data breaches.
DDoS Attacks: Flooding signaling traffic to crash network functions.
Access Control Risks: Unauthorized access to core functionalities.
Lawful Interception (LI) Vulnerabilities: Exploits in monitoring systems meant to be legal.
Virtualization Vulnerabilities: Weaknesses within hypervisors and virtual machines.
Example: If attackers get into the SMF (Session Management Function), they could disrupt connectivity for entire groups of users.
SGi/N6 Interface Threats
The N6 interface links the 5G core to outside data networks (like the internet, content delivery systems, and enterprise setups). This area is high-risk as it exposes the network to outside threats.
SGi/N6 threats include:
Application Server Vulnerabilities: Weaknesses in the app servers themselves.
API Vulnerabilities: Poorly secured APIs can allow data tampering.
VAS (Value-Added Services) Integration Risks: Bringing in third-party services could create backdoors.
Example: A poorly secured API in an IoT healthcare app might leak sensitive patient information.
Summary of 5G Security Threats
Here’s a quick overview of the threats across the 5G ecosystem:
Layer | Threats
Device | Malware, tampering, firmware hacks, botnets, sensor exploits
RAN | Insecure interfaces (S1/X2/Xn), jamming, rogue nodes
MEC | CP/UP sniffing, NFVI risks, DDoS, backhaul sniffing, Sx/N6 vulnerabilities
5G Packet Core | Slice security, DDoS, access risks, LI vulnerabilities, virtualization flaws
SGi/N6 Interface | App server weaknesses, API flaws, VAS integration risks
Mitigating 5G Security Threats
To create a resilient 5G ecosystem, we need to implement proactive security strategies like:
Device Hardening: Secure boot, firmware validation, and malware detection.
RAN Security: Strong encryption, authentication measures, and rogue node detection.
MEC Protection: Isolated edge environments, secure APIs, and intrusion detection systems.
Core Security: Solid access controls, AI-based anomaly detection, and slice isolation.
Interface Safeguards: API security testing, third-party audits, and zero-trust policies.
Looking Ahead: Security in 5G and What’s Next
As 5G networks continue to develop and set the stage for 6G, it’s crucial that our security approaches keep up.
Here are some important things to think about for the future:
- Zero Trust Architecture
Every device, node, and app should be authenticated continuously.
This strategy helps stop attackers from moving around inside networks.
- Using AI and Machine Learning for Threat Detection
AI-driven security analytics can spot anomalies in real-time.
This tech can predict and prevent unknown attack patterns before they cause harm.
- Encryption That Can Stand Up to Quantum Computing
With quantum computing on its way, the encryption we use now might get compromised.
5G will need to incorporate post-quantum cryptography to stay resilient in the long run.
- Ensuring Security in Network Slicing
While network slicing provides flexibility, it also opens up more ways for attacks.
We need to implement isolation mechanisms and security policies tailored to each slice.
- Working Together Across the Ecosystem
We can’t leave security up to the operators alone.
It’s essential for vendors, regulators, and enterprises to collaborate on establishing unified standards and best practices.
Conclusion
5G networks are gearing up to transform industries, but without strong cybersecurity frameworks, their full potential could be at risk from malicious actors. By getting a grasp on the multi-layered security threats across devices, RAN, MEC, core, and external interfaces, telecom pros can implement effective defense-in-depth strategies.
The future of 5G security hinges on continuous monitoring, AI-driven threat detection, and teamwork across the telecom ecosystem to safeguard both consumers and businesses.
