Understanding 5G NR AS Security Procedure: Step-by-Step Guide to Key Derivation and Integrity Protection

Understanding 5G NR AS Security Procedure
In 5G networks, security operates in layers—starting with NAS authentication at the core all the way to AS protection at the radio interface. Once NAS security is in place, we move on to an essential part: the Access Stratum (AS) Security Procedure. This is where the UE (User Equipment) and the gNB (5G NodeB) get set up to encrypt and protect the integrity of RRC and user-plane signaling.
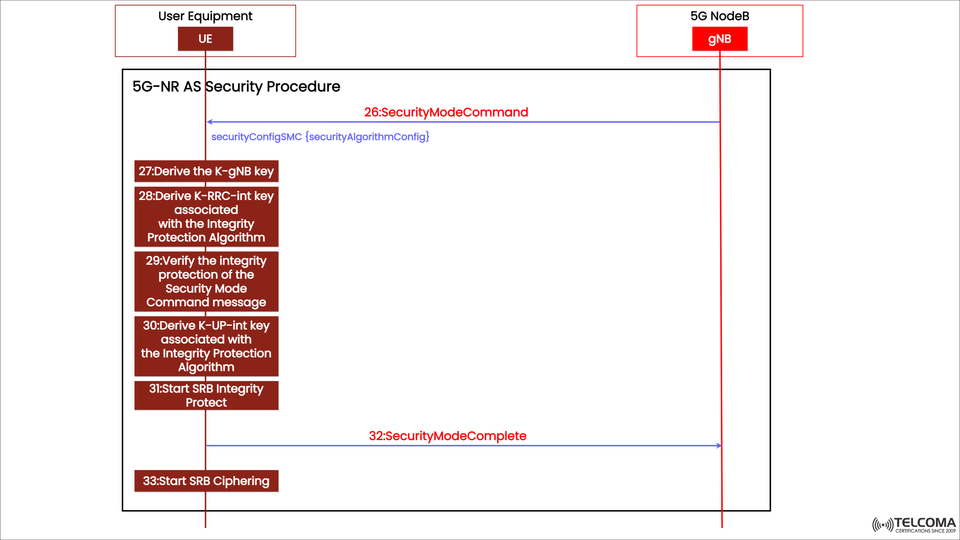
The diagram uploaded clearly illustrates how this all happens—beginning with the Security Mode Command and moving through key derivations, integrity checks, and finally to ciphering activation.
What’s 5G NR AS Security?
The Access Stratum (AS) is the layer that sits between the UE and the gNB, handling all radio communication. While NAS (Non-Access Stratum) secures signaling between UE and the 5G Core (AMF), AS security is all about protecting signaling and user data traveling over the air interface—which is the most exposed part of the network.
AS Security has three main roles:
Confidentiality (Encryption): Shields data from being intercepted.
Integrity Protection: Makes sure that signaling messages aren’t altered.
Key Management: Generates keys for different layers (RRC and User Plane).
So, even if someone tries to capture the radio traffic, they won't be able to read or modify it.
Overview of the 5G NR AS Security Flow
The diagram shows a series of AS security operations starting with the Security Mode Command and ending with SRB ciphering.
Step Message / Operation Direction Purpose
26Security Mode Command gNB → UE Instructs the UE to activate AS security using chosen algorithms.
27Derive K-gNB key UE local operation Derives gNB-level key from K_AMF.
28Derive K-RRC-int key UE local operation Generates integrity protection key for RRC.
29Verify integrity of SMCUE local operation Confirms the SMC message hasn’t been tampered with.
30Derive K-UP-int key UE local operation Generates integrity protection key for user-plane.
31Start SRB Integrity Protect UE local operation Initiates integrity protection on SRB messages.
32Security Mode Complete UE → gNB Confirms successful activation of security.
33Start SRB Ciphering UE local operation Begins encryption for RRC signaling.
Step 26: Security Mode Command
The process kicks off when the gNB sends a Security Mode Command (SMC) message to the UE.
This message includes the security configuration parameters, often called security Algorithm Config, which covers:
Ciphering algorithm (EEA) for confidentiality protection.
Integrity algorithm (EIA) for authenticity assurance.
Essentially, this command tells the UE which algorithms and keys to use for AS protection.
Before the UE can get to work on them, it needs to verify and derive the necessary keys.
Step 27: Deriving the K-gNB Key
Once the SMC is in the UE’s hands, it starts the key derivation process by calculating the K-gNB key.
K-gNB is derived from K-AMF, which was set up during NAS authentication.
This key acts as the root from which other keys in the AS security domain are generated.
The formula provided by 3GPP (TS 33.501) is:
K-gNB = K-AMF ⊕ FC || P0 || L0
Where FC and parameters (P0, L0) ensure each connection is unique.
K-gNB serves as the master key for both RRC and user-plane security derivations.
Step 28: Deriving K-RRC-int Key
After getting K-gNB, the UE generates K-RRC-int, which is specifically used for RRC (Radio Resource Control) integrity protection.
This key guarantees that RRC signaling messages between UE and gNB can’t be altered or forged.
The derivation formula takes into account the identifiers for security algorithms:
K-RRC-int = K-gNB ⊕ f(algorithm ID, direction, bearer ID)
This ensures that each RRC session has a unique integrity key drawn from the main K-gNB.
Step 29: Verifying Integrity Protection of Security Mode Command
Before security can be activated, the UE needs to check that the Security Mode Command itself hasn’t been tampered with.
Using K-RRC-int, the UE verifies the integrity protection of the received SMC message.
If the verification passes, the UE can trust that the message is from a legitimate gNB.
If it fails, the UE tosses the command out, blocking potential man-in-the-middle (MITM) attacks.
This validation step is crucial because integrity protection ensures message authenticity, keeping unauthorized commands out.
Step 30: Deriving K-UP-int Key
After confirming the SMC, the UE derives yet another key—K-UP-int, which is used for user-plane integrity protection.
While not all operators enforce user-plane integrity due to processing overhead, it’s vital for mission-critical applications, industrial IoT, or secure enterprise networks.
K-UP-int ensures that user data packets shared between UE and gNB are verified for authenticity.
The derivation process is still linked back to K-gNB, ensuring key integrity throughout.
Step 31: Starting SRB Integrity Protection
Once K-RRC-int and K-UP-int are ready, the UE kicks off SRB (Signaling Radio Bearer) Integrity Protection.
SRB carries RRC signaling messages like configuration commands, mobility management messages, and handover instructions.
Integrity protection here means that:
No one can alter or inject fake signaling messages.
The gNB and UE can instantly detect and disregard tampered messages.
This marks the activation of AS integrity protection on the signaling level.
Step 32: Security Mode Complete
After setting up integrity protection, the UE sends the Security Mode Complete message back to the gNB.
This confirms:
All keys have been successfully derived.
Integrity protection on SRB has been activated.
The system is ready to start ciphering (encryption).
At this point, all future RRC and NAS messages sent over SRB are integrity protected.
Step 33: Starting SRB Ciphering
The last step in the AS Security procedure is turning on SRB ciphering, which provides confidentiality for signaling messages.
Once SRB ciphering begins:
All RRC and NAS messages are encrypted.
Sensitive parameters (like configuration data or handover commands) are protected from eavesdropping.
The UE and gNB use K-RRC-enc, derived from K-gNB, as the encryption key for this purpose.
This wraps up the AS Security Mode activation.
Real-World Example: Secure UE–gNB Communication
Once AS security is in place:
All RRC messages (like configurations, measurement reports, mobility updates) are integrity-protected and encrypted.
User-plane data, including voice, video, or internet traffic, flows securely between UE and gNB using distinct ciphering keys.
Even if an attacker intercepts the radio link, they can’t decipher the contents or inject unauthorized commands.
This establishes a trusted communication environment, which is crucial for IoT, autonomous systems, and enterprise 5G networks.
Conclusion
The 5G NR AS Security Procedure wraps up the final layer of protection before data transmission kicks off. By deriving keys from K-AMF and activating integrity protection and ciphering at the RRC and user-plane levels, the network ensures both confidentiality and authenticity over the air interface.
From the Security Mode Command to SRB Ciphering, every step guarantees that only authorized entities can exchange messages and that those messages remain unchanged and unreadable by outsiders.
In essence, AS Security turns the radio interface into a cryptographically secured channel, reinforcing 5G’s commitment to secure, high-performance connectivity.
