Understanding 5G RAN Network Security Architecture

Understanding 5G RAN Network Security Architecture
5G isn't just about speed, lower latency, and handling loads of IoT devices; it also brings a clear need for strong security throughout the radio access network (RAN). Unlike the older generations, 5G uses a service-based architecture that's heavily based on virtualized, cloud-native, and disaggregated RAN components like O-RU, O-DU, and O-CU.
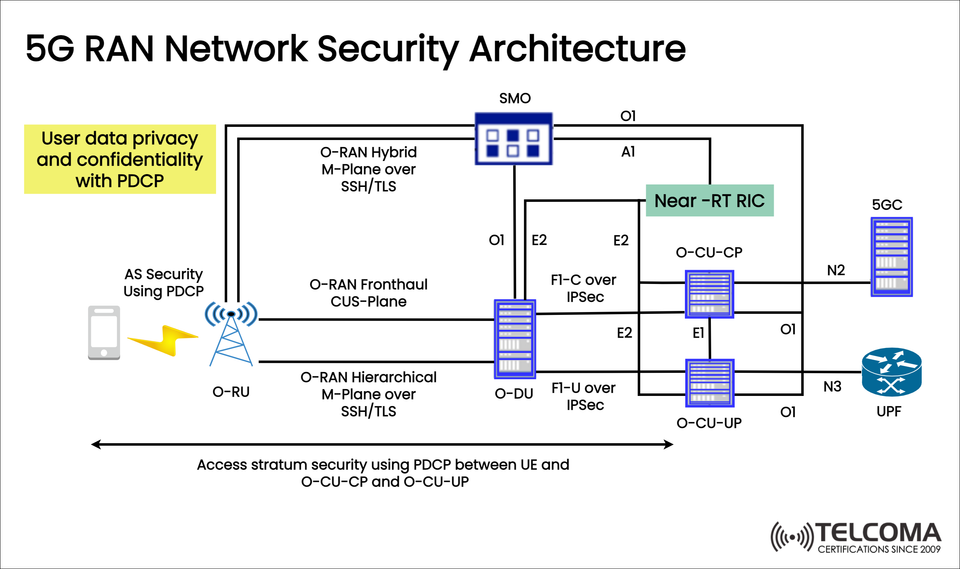
With these new developments come different security threats, so the 5G RAN Network Security Architecture becomes a vital part of telecom infrastructure. The diagram shared shows how security is applied at various levels, helping to make sure that there's user data privacy, confidentiality, and secure communication between RAN and the 5G Core (5GC).
Let's break this down step by step.
Why 5G RAN Security is Important
In 4G LTE, RAN security was mostly about encryption and integrity protection between user equipment (UE) and the eNodeB. But with the disaggregation in 5G, we have more interfaces and entities involved, which means we need a thorough, multi-layered security model.
Here are some key motivations for enhancing 5G RAN security:
Safeguarding user data privacy across various applications (like AR/VR, IoT, and self-driving cars).
Protecting O-RAN interfaces that are open to external control and management.
Allowing cloud-native setups without putting data confidentiality at risk.
Stopping cyber threats like spoofing, man-in-the-middle attacks, and denial-of-service.
Core Components of 5G RAN Security
The diagram shows how multiple security layers and protocols protect the entire RAN ecosystem.
- User Data Privacy and Confidentiality with PDCP
The Packet Data Convergence Protocol (PDCP) is crucial for encrypting and ensuring the integrity of user data.
Access Stratum (AS) security uses PDCP between the UE and O-CU (both control and user plane).
This setup helps prevent eavesdropping, tampering, and replay attacks.
Key Point: PDCP is the first defense line for both user plane and control plane data in 5G RAN.
- Security in O-RAN Interfaces
With O-RAN's disaggregation, multiple interfaces each have their own security methods:
O1 Interface (from SMO to O-RAN nodes): - Secured with SSH/TLS encryption for management tasks like configuration and performance monitoring.
O-RAN Hierarchical M-Plane (O-RU to O-DU): - Uses SSH/TLS for secure management signaling.
O-RAN Hybrid M-Plane (O-DU to SMO): - Also encrypted using SSH/TLS for hybrid management.
O-RAN Fronthaul (O-RU to O-DU): - The CUS-plane (Control, User, Synchronization) needs protections against tampering.
Key Point: O-RAN relies on SSH/TLS for M-Plane security and IPsec for the control and user planes, providing end-to-end security.
- F1 Interface (O-DU to O-CU)
F1-C (Control Plane) over IPsec safeguards control signaling.
F1-U (User Plane) over IPsec secures data traffic.
Key Point: IPsec is crucial for protecting sensitive signaling and user data in distributed RAN frameworks.
- Near-Real Time RIC (RAN Intelligent Controller)
The Near-RT RIC enhances RAN performance using AI/ML-driven policies.
It connects with O-CU through E2, which must be fortified with IPsec/TLS.
If violated, attackers could manipulate network optimization processes, resulting in poorer quality of service or even outages.
Key Point: Securing the RIC is vital since it manages intelligent RAN operations.
- Integration with 5GC and UPF
O-CU-CP connects to 5GC via N2.
O-CU-UP links to UPF through N3.
Both connections rely on secure tunnels and mutual authentication between the RAN and 5GC.
Key Point: End-to-end integrity is kept intact by securing the handoff points between the RAN and the core network.
Security Protocols in 5G RAN
Here’s a quick overview of the protocols and mechanisms at play in the 5G RAN Security Architecture:
Component Interface Security Mechanism
UE ↔ O-CU PDCP AS Security (Encryption, Integrity Protection)
O-RU ↔ O-DU Fronthaul CUS IPsec, TLS/SSH
O-DU ↔ O-CU F1-C / F1-U IPsec
SMO ↔ O-RAN Nodes O1 SSH/TLS
Near-RT RIC ↔ CU E2 TLS/IPsec
CU ↔ 5GC / UPF N2 / N3 IPsec / Secure Tunneling
Challenges in Securing 5G RAN
While the architecture provides multiple layers of defense, telecom operators still face some real hurdles:
Complexity: A variety of interfaces creates more configuration and monitoring work.
Virtualization Risks: Cloud-native RANs can be vulnerable to container weaknesses and API issues.
Latency vs Security Trade-offs: Stronger encryption (like IPsec) can add some overhead, making it important to balance speed and security.
Supply Chain Risks: O-RAN’s multi-vendor landscape brings challenges for establishing trust and ensuring interoperability.
Best Practices for 5G RAN Security
Telecom operators should embrace a defense-in-depth strategy to bolster 5G RAN security:
End-to-End Encryption: Use a layering of PDCP, IPsec, and TLS for all interfaces.
Zero-Trust Architecture: Authenticate each entity before allowing access.
Continuous Monitoring: Implement AI-based intrusion detection and anomaly tracking in the RAN.
Vendor Security Audits: Ensure strict compliance from O-RAN suppliers.
Network Slicing Security: Create strong isolation for different slices to avoid cross-slice attacks.
Conclusion
The 5G RAN Network Security Architecture makes sure that the next wave of mobile networks can offer not just speed and capacity, but also reliability and trust.
PDCP protects user data privacy and confidentiality.
SSH/TLS and IPsec safeguard crucial RAN interfaces like O1, F1, and E2.
O-RAN security measures tackle risks in disaggregated, cloud-native environments.
Integration with the 5G Core (5GC) maintains end-to-end secure connectivity.
For telecom professionals and network architects, mastering RAN security has become essential for delivering resilient, future-ready 5G networks.
