Understanding AUSF Interactions in 5G Standalone Access Registration
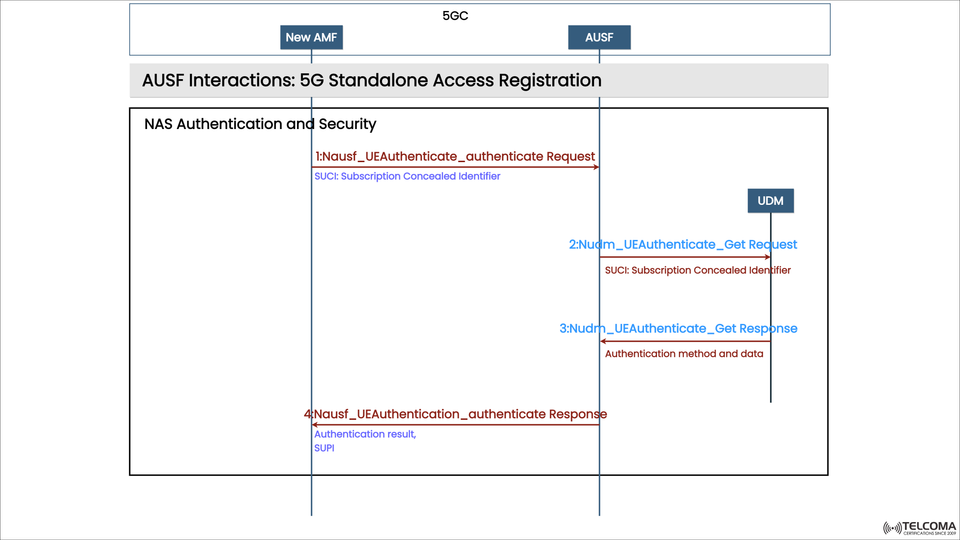

AUSF Interactions in 5G Standalone Access Registration Explained
The Authentication Server Function, or AUSF, is key to securing 5G networks. It authenticates subscribers and ensures that communication between user devices and the 5G Core (5GC) is trusted.
The image above shows how the AUSF interacts during 5G Standalone (SA) access registration. It highlights the collaboration between important 5G Core Network (5GC) entities — AMF, AUSF, and UDM — to carry out NAS authentication and set up secure connections between User Equipment (UE) and the network.
In this blog post, we'll break down the message sequence, key identifiers, and the functional importance of each step in the authentication process.
Understanding the 5G Core (5GC) Authentication Framework
Before we get into AUSF interactions, let’s quickly cover how authentication fits into the 5G Core architecture.
In a 5G Standalone (SA) setup, the Access and Mobility Management Function (AMF) manages mobility and registration. Meanwhile, AUSF and UDM (Unified Data Management) work together to ensure authentication is secure and standardized.
The main authentication mechanisms used in 5G are:
5G-AKA (Authentication and Key Agreement)
EAP-AKA’ (Extensible Authentication Protocol-AKA’)
These methods help maintain confidentiality, integrity, and the authenticity of user identities and traffic.
Key Entities in AUSF Authentication Flow
Entity Function AMF (Access and Mobility Management Function)Kicks off the authentication process, communicates with AUSF, and manages registration procedures. AUSF (Authentication Server Function)The main entity responsible for authenticating the UE through methods like 5G-AKA or EAP-AKA’.UDM (Unified Data Management)Holds subscriber info, keys, and authentication data, providing AUSF with authentication vectors. UE (User Equipment)The device (like a smartphone or IoT gadget) that makes the registration request to connect to the 5G network.
Overview of AUSF Interactions: 5G SA Registration
The NAS (Non-Access Stratum) authentication process in 5G consists of a four-step message exchange between AMF, AUSF, and UDM.
Here’s a quick rundown of what each step entails (as shown in the image):
Step Message Direction Key DataDescription1Nausf_UEAuthenticate_authenticate Request AMF → AUSFSUCI The AMF sends an authentication request with the Subscription Concealed Identifier (SUCI) to AUSF.2Nudm_UEAuthenticate_Get Request AUSF → UDMSUCIAUSF asks UDM for authentication data using SUCI.3Nudm_UEAuthenticate_Get Response UDM → AUSF Authentication Method and Data UDM sends back the authentication vectors (keys, method, parameters) to AUSF.4Nausf_UEAuthentication_authenticate Response AUSF → AMFSUPI, Authentication Result AUSF sends the authentication result and decrypted Subscription Permanent Identifier (SUPI) back to AMF.
Step-by-Step Explanation of the AUSF Authentication Flow
Now, let’s dive deeper into each step to understand the technical flow and the security logic behind it.
Step 1: Authentication Request from AMF to AUSF
Message: Nausf_UE Authenticate_authenticate Request
Key Field: SUCI (Subscription Concealed Identifier)
When a UE tries to register with the 5G network, the AMF kicks off the authentication process by sending a request to AUSF. This message includes the SUCI, a privacy-protected version of the SUPI (Subscription Permanent Identifier).
The UE generates the SUCI by encrypting the SUPI with the Home Network’s public key.
This way, the permanent subscriber identity isn’t exposed over the air, which enhances privacy and prevents tracking.
At this stage, AUSF doesn’t know the SUPI yet; it only receives the encrypted SUCI.
Step 2: AUSF Requests Authentication Vectors from UDM
Message: Nudm_UE Authenticate_Get Request
Key Field: SUCI
Once AUSF gets the SUCI, it sends a request to UDM to get the authentication vectors. UDM decrypts the SUCI to find the SUPI and locates the subscriber in its database.
Then, UDM generates an authentication vector, which consists of:
RAND (Random Challenge)
AUTN (Authentication Token)
XRES* (Expected Response)
KSEAF (Key Seed for SEAF)
These parameters rely on the 5G-AKA or EAP-AKA’ algorithms and are securely sent back to AUSF in the next step.
Step 3: AUSF Receives Authentication Data from UDM
Message: Nudm_UEAuthenticate_Get Response
Key Field: Authentication Method and Data
UDM then responds with the authentication method and data vectors, allowing AUSF to verify the UE.
At this moment:
AUSF determines which authentication method (5G-AKA or EAP-AKA’) works for the subscriber.
It computes HXRES* — a hashed version of the expected response (XRES*) — and saves it for future comparison.
This step makes sure that only valid subscribers, who can adequately respond to the challenge, get access.
Step 4: AUSF Sends Authentication Response to AMF
Message: Nausf_UEAuthentication_authenticate Response
Key Fields: Authentication Result, SUPI
Finally, AUSF sends an authentication response back to AMF, which contains:
Authentication Result (to show success or failure)
SUPI (the decrypted permanent identifier)
If authentication goes well:
The AMF derives a KAMF (Key for AMF) from the KSEAF key it got earlier.
This KAMF is used to create secure NAS and AS (Access Stratum) connections between the UE and the network.
With this, the NAS authentication and security setup in 5G Standalone mode is complete.
Security Highlights of AUSF Authentication Flow
The AUSF-based authentication model in 5G introduces some improvements over older generations like LTE:
Subscriber Identity Protection
The SUCI usage ensures that the permanent identity (SUPI) stays hidden.
Separation of Control and Authentication Functions
AUSF focuses on just authentication, while AMF takes care of mobility and access, leading to a modular design.
Flexible Authentication Methods
It supports both 5G-AKA and EAP-AKA’, making it compatible with various devices and networks.
Enhanced Key Hierarchy
5G adopts a layered key derivation model (KSEAF → KAMF → KNAS/AS) to boost session isolation and reduce key exposure risks.
Integration with Service-Based Architecture (SBA)
AUSF and UDM use standardized APIs (Nausf_, Nudm_) defined by 3GPP to ensure scalability and inter-vendor compatibility.
Practical Insights for Telecom Professionals
For network engineers and 5G architects, grasping AUSF interactions is vital when:
Designing 5G core networks with secure onboarding processes.
Implementing authentication algorithms in vendor-neutral setups.
Ensuring alignment with 3GPP Release 15 and 16 security standards.
Troubleshooting registration issues due to authentication mismatches between AMF, AUSF, and UDM.
These insights help keep authentication delays low while still providing strong identity protection.
Key Takeaways
Concept Description AUSF Role Handles subscriber authentication in 5G Standalone mode SUCI/SUPISUCI hides SUPI for privacy sake5G-AKA / EAP-AKA’ Authentication protocols for secure access AMF-AUSF-UDM Flow4-step sequence that ensures identity verification and key derivation Security Outcome Sets up encrypted channels and trust between UE and network
Conclusion: AUSF — The Security Backbone of 5G Core
The Authentication Server Function (AUSF) is a crucial part of the 5G Core security framework. By collaborating with AMF and UDM, it ensures that only authorized users can access the network while safeguarding subscriber identities with SUCI/SUPI encryption methods.
The step-by-step authentication process — from Nausf_UEAuthenticate Request to Response — illustrates how 5G is moving towards cloud-native, API-driven, and privacy-focused architectures.
As billions of devices connect to 5G, AUSF’s strong authentication and identity protection will lay the groundwork for trust, resilience, and smooth communication.
