Understanding SUCI in 5G: Subscription Concealed Identifiers Explained

Grasping SUCI in 5G: Unpacking Subscription Concealed Identifiers
The Importance of Privacy in the 5G Landscape
One major leap forward with 5G is better protection for user identities. In earlier systems like 2G, 3G, and LTE, subscriber identities (IMSI) were sometimes sent as plain text, which left them open to interception and misuse. With so many devices—think smartphones, IoT gadgets, and connected cars—coming online in the 5G world, it was crucial to step up privacy protections.
This is where SUCI (Subscription Concealed Identifier) comes in. SUCI is a hidden version of SUPI (Subscription Permanent Identifier), designed to keep permanent identifiers from being transmitted openly. It’s a key part of the 5G security framework, making sure that sensitive subscriber data stays secure during the registration phase on the network.
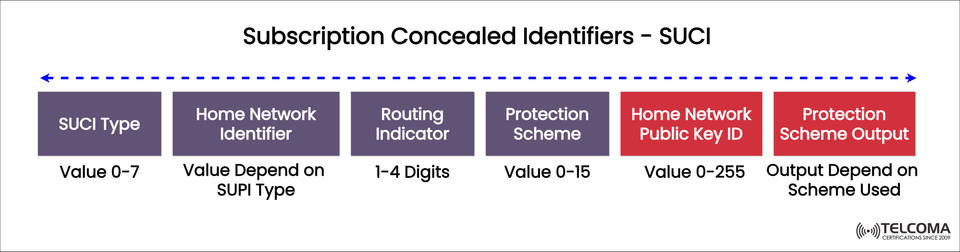
The diagram above gives a clearer picture of the SUCI structure, breaking it down into different fields that help ensure both its uniqueness and security.
What is SUCI in 5G?
SUPI (Subscription Permanent Identifier): Think of it as a unique and permanent ID for subscribers, similar to IMSI used in LTE.
SUCI (Subscription Concealed Identifier): This is an encrypted form of SUPI, which the UE (User Equipment) creates before sending it off to the network.
So, the concept is pretty straightforward: the permanent ID isn't revealed directly. Instead, when a device registers, it sends SUCI, keeping the SUPI shielded from potential attackers like IMSI catchers.
Breaking Down the SUCI Structure
The design of SUCI is laid out by 3GPP and consists of several fields, each with a specific function that helps ensure subscriber identification is both secure and efficient.
If we look at the image, the SUCI includes:
SUCI Type (Value 0–7) * This tells the network what kind of SUCI is being used and how to interpret the concealed identity.
Home Network Identifier * Drawn from the SUPI type, this identifies the subscriber's home network, usually indicating the MCC (Mobile Country Code) and MNC (Mobile Network Code).
Routing Indicator (1–4 digits) * Offers routing info for processing subscriber identity and helps target authentication requests quickly.
Protection Scheme (Value 0–15) * Points out the encryption method used to shield SUPI. Different schemes might be available based on operator setup.
Home Network Public Key ID (Value 0–255) * Specifies which public key from the home network gets used for encryption, allowing secure decryption at the UDM (Unified Data Management) node.
Protection Scheme Output * This is the encrypted result from applying the selected protection scheme, essentially hiding the SUPI.
How SUCI Functions in Real Life
To get a better sense of how SUCI operates, let’s review the identity exchange process:
The UE creates SUCI by encrypting SUPI with its home network's public key.
SUCI is sent in a Registration Request to the serving gNB and then forwarded to the AMF.
The AMF forwards SUCI to the UDM in the home network.
UDM decrypts SUCI using its private key to find the SUPI.
The authentication process continues using the SUPI internally, without ever sending it over the air.
This whole procedure makes sure that only the home network can access SUPI, greatly reducing risks from eavesdropping and man-in-the-middle attacks.
Why SUCI Matters
Privacy Assurance: Stops permanent IDs from being exposed.
Defense Against IMSI Catchers: Attackers can’t directly grab SUPI.
Scalability: Works smoothly with billions of devices.
Future-Proof Security: Utilizes asymmetric encryption (public/private key pairs).
Protection Schemes for SUCI
When it comes to crafting SUCI, different protection schemes can be used. These are laid out by 3GPP standards to ensure flexibility and compatibility.
Protection Scheme Description Use Case Null Scheme No encryption (rarely used)For testing or low-security scenarios ECIES-based scheme Encrypts SUPI with Home Network’s public key Common in most 5G setups Operator-defined scheme Custom encryption approach For proprietary networks
Most commercial 5G networks go for the ECIES (Elliptic Curve Integrated Encryption Scheme) since it strikes a good balance between security and efficiency.
SUCI vs. SUPI: Key Differences
Feature SUPISUCI Definition Permanent subscriber ID Concealed (encrypted) version of SUPI Exposure Never directly sent in 5GAlways sent instead of SUPI Security At risk if exposed Strongly secured with encryption Storage Securely stored in USIM Generated dynamically by UE Use Case Core network authentication Air interface communication
SUCI in Roaming Situations
SUCI is significant in the context of international roaming. When a subscriber roams onto another operator's network:
SUCI is generated and sent to the visited AMF.
This AMF then sends SUCI to the subscriber’s home UDM.
Only the home network can decrypt SUCI → this ensures roaming networks never gain direct access to the SUPI.
This helps keep subscriber identities safe worldwide, no matter which network they're connected to.
Technical Challenges with SUCI
Even though SUCI is tough, there are hurdles to overcome:
Public Key Management: Operators need to securely manage and refresh encryption keys.
Performance on IoT Devices: Lightweight devices must perform encryption without zapping the battery.
Interoperability in Roaming: Guaranteeing consistent SUCI handling across different networks is key.
Conclusion: SUCI as the Guardian of Subscriber Identity in 5G
The Subscription Concealed Identifier (SUCI) brings some of the most significant privacy upgrades in 5G. By encrypting the permanent SUPI, SUCI ensures that subscriber identities aren’t exposed on the radio interface.
Key points to remember:
SUCI is produced by encrypting SUPI with the public key of the home network.
It’s structured with fields like SUCI type, routing indicator, protection scheme, and scheme output.
SUCI guarantees privacy, secures roaming, and fights against IMSI-catcher threats.
Together with GUTI and SUPI, SUCI underpins 5G identity management.
For telecom experts, SUCI isn’t just a technical thing—it’s the foundation of subscriber trust in 5G networks. As networks develop, making sure SUCI is robustly implemented will be crucial for keeping billions of devices secure.
