Understanding the Resource Allocation Model in Wireless Networks

Understanding the Resource Allocation Model in Wireless Networks
In today’s wireless networks, effectively using spectrum is key to performance. With countless devices vying for a limited amount of bandwidth, operators have to optimize how they allocate resources to keep quality of service (QoS) high while also fending off interference and potential attacks.
The resource allocation model shown in the diagram is a framework that explains how bandwidth gets distributed, how feedback is gathered, and how interference—especially from jammers—is handled. This intelligent, layered model is essential for next-gen communication systems like 5G and beyond.
Core Components of the Resource Allocation Model
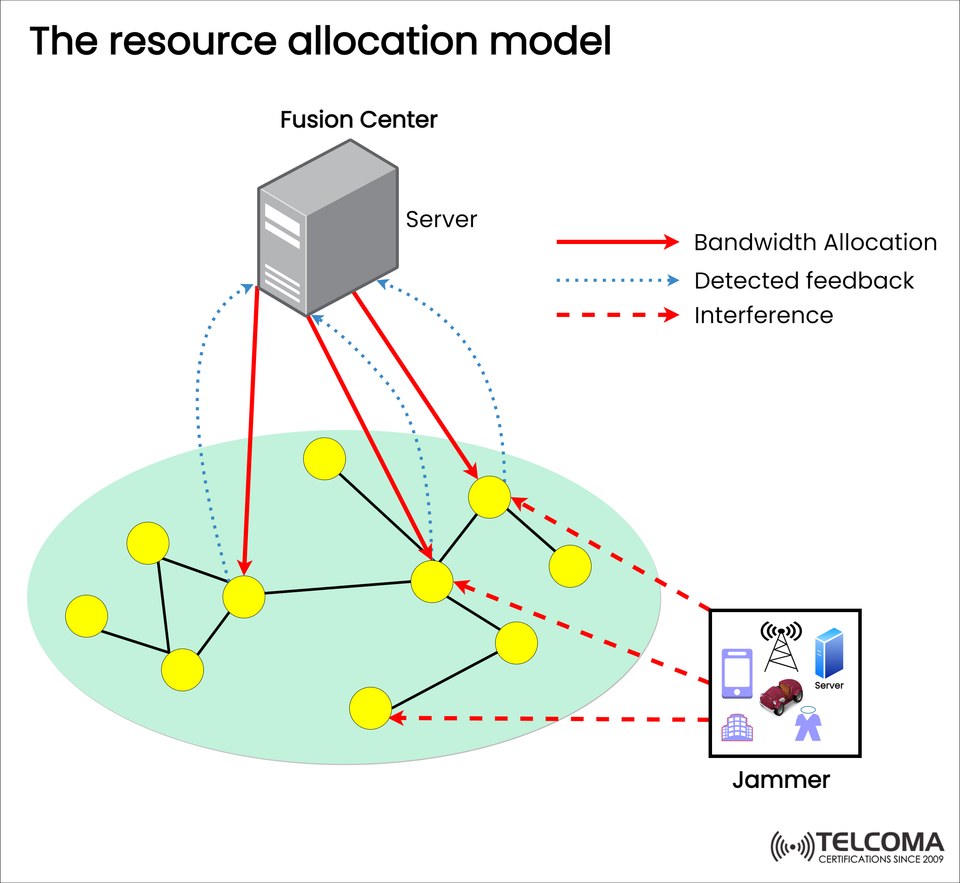
The diagram showcases some important entities:
Fusion Center (Server):
This is the main hub for resource allocation.
It collects feedback from various network nodes.
It allocates bandwidth based on current traffic and interference levels.
Network Nodes (Yellow Circles):
These represent connected devices or local clusters linked to the server.
They communicate with one another and share data.
They send back conditions to the fusion center to optimize allocation.
Jammer:
This can be a malicious or accidental source of interference.
It tries to disrupt communication by introducing noise or overwhelming the spectrum.
Communication Links:
Red Arrows: Show bandwidth being allocated from the server to the nodes.
Blue Dotted Arrows: Represent feedback loops that send performance data back to the server.
Red Dashed Arrows: Indicate interference caused by jammers.
How the Resource Allocation Model Operates
This model is based on a closed-loop system where decisions get updated continuously:
Step 1: Allocating Bandwidth
The fusion center hands out spectrum resources (bandwidth) to the nodes based on demand, priority, and QoS needs.
Critical applications, like emergency communications, get top priority.
More casual applications, like browsing the web, get whatever resources are left over.
Step 2: Gathering Feedback
Nodes keep a watchful eye on the quality of the bandwidth they’re given. They send feedback to the fusion center that includes:
Signal-to-noise ratio (SNR)
Packet delivery success rates
Latency measurements
Levels of interference
This feedback loop allows for dynamic adjustments instead of just static allocations.
Step 3: Mitigating Interference
When a jammer tries to throw a wrench in the communication, nodes pick up on unusual patterns (like sudden noise spikes or lost packets).
The fusion center can then:
Shift bandwidth away from the affected frequency.
Boost redundancy or error correction methods.
Use beamforming or adaptive modulation to lessen interference.
Security Challenges in Resource Allocation
Even though resource allocation improves performance, it can also create vulnerabilities. The jammer in the diagram highlights one of the major threats.
Common Threats:
Jamming Attacks: Intentional interference that aims to disrupt communication channels.
Eavesdropping: Unauthorized listening when feedback or allocations are sent without encryption.
Spoofed Feedback: Fake nodes that send incorrect information, tricking the fusion center into misallocating resources.
Countermeasures:
Encrypt Control Channels to guard against spoofing or eavesdropping.
Employ Spread Spectrum Techniques to enhance resistance to jamming.
Utilize Machine Learning Algorithms to spot abnormal interference patterns early.
Advantages of the Resource Allocation Model
By combining smart allocation with ongoing feedback, this model ensures:
Efficiency: Makes the best use of limited spectrum resources.
Scalability: Can handle vast IoT deployments with thousands of devices competing for bandwidth.
Resilience: Adapts to counter both accidental and intentional interference.
QoS Assurance: Prioritizes applications sensitive to latency like autonomous driving, remote surgeries, or AR/VR.
Resource Allocation in 5G and Beyond
When it comes to 5G wireless networks, the resource allocation model takes on an even more crucial role:
Network Slicing: It creates different logical networks on the same physical framework. Each slice gets its own specific allocation of bandwidth and latency.
Ultra-Reliable Low-Latency Communication (URLLC): Demands flexible allocation with strict QoS guarantees.
Massive Machine-Type Communication (mMTC): Needs to efficiently share spectrum among billions of IoT devices.
Enhanced Mobile Broadband (eMBB): Ensures applications demanding high throughput, such as 4K streaming, run smoothly during peak usage.
Use Case Examples
Smart Cities:
Sensors and surveillance cameras transmit data to a central server.
Bandwidth gets allocated dynamically to the most critical sensors (like emergency alarms).
Any jammers trying to disrupt vital systems are quickly dealt with.
Autonomous Vehicles:
Cars share real-time traffic info with roadside units and servers.
Feedback helps fine-tune spectrum allocation based on traffic levels.
Any interference from malicious devices is countered to ensure safety.
Industrial IoT:
Machines in a factory send in operational data.
Feedback loops allow for adaptive reallocation to avoid downtime.
Jammer detection promotes secure, uninterrupted automation.
Comparative Overview
Aspect
Traditional Networks
Resource Allocation Model
Bandwidth Assignment
Static
Dynamic and adaptive
Interference Handling
Limited
Proactive mitigation with feedback
Security
Basic encryption
Multi-layer defense (anti-jamming, secure feedback)
Scalability
Limited
High, designed for IoT and 5G
The Future of Resource Allocation
As networks evolve into 6G, resource allocation will incorporate advanced technologies:
Artificial Intelligence (AI): AI-driven predictive allocation based on traffic trends.
Blockchain: Ensures transparency and trust in the feedback and allocation processes.
Quantum-Safe Encryption: Protects allocation channels from future quantum computing threats.
Edge Computing: Moves fusion centers closer to the user to cut down latency and enhance resilience.
In Closing
The resource allocation model is fundamental to modern wireless network design, making sure bandwidth is used efficiently, optimization is driven by feedback, and resilience against interference and jamming is maintained.
For telecom professionals and network engineers, getting a handle on this model is crucial for keeping up with the demands of 5G, IoT, and future 6G ecosystems. By striking a balance among performance, security, and scalability, resource allocation ensures networks stay reliable even as threats evolve.
