Understanding the SEAL Functional Model in 3GPP: Architecture, Components, and Interfaces

SEAL Functional Model Explained: The Backbone of 3GPP Vertical Application Layer (VAL) Systems
As 5G networks keep advancing, industries like automotive, healthcare, manufacturing, and smart cities need tailored communication frameworks that go beyond regular network connectivity. To address these varied application requirements, the 3GPP Service Enabler Architecture Layer (SEAL) offers a cohesive and modular platform that supports interoperable and secure communication within the Vertical Application Layer (VAL).
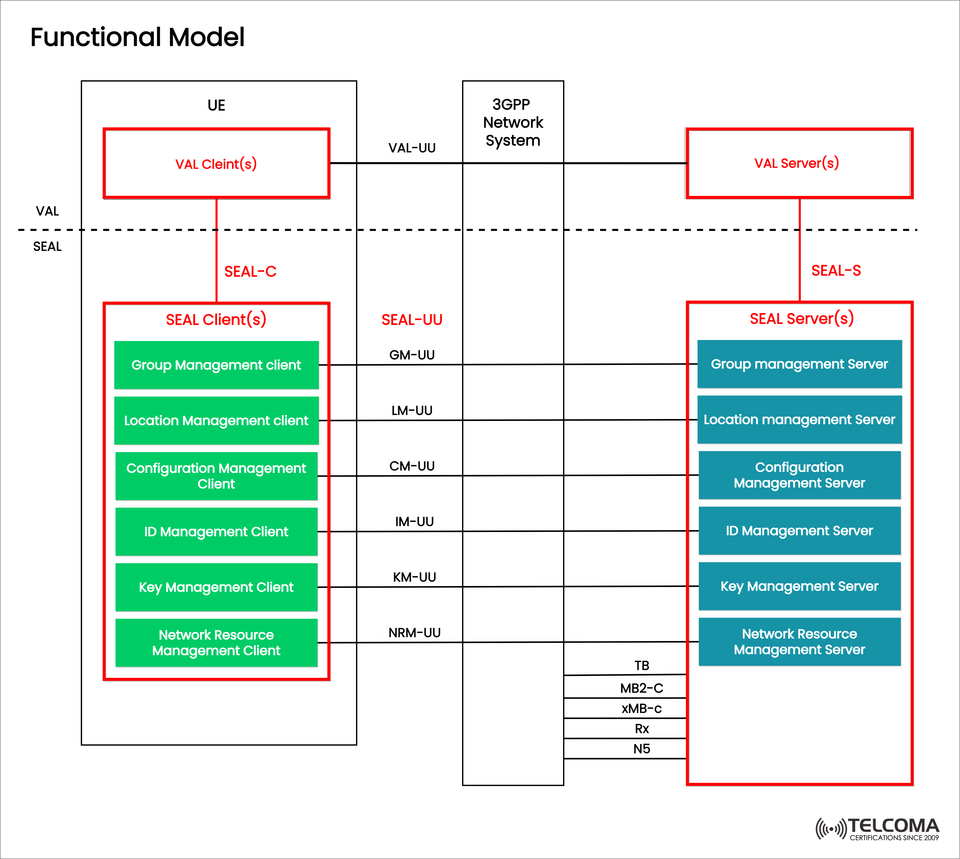
The Functional Model illustrated above clearly shows how SEAL operates within the 3GPP ecosystem, linking VAL Clients, VAL Servers, and SEAL components through clearly defined interfaces.
In this blog, we’ll dive into the SEAL Functional Model, its various components, interfaces, and how it fits into the wider 3GPP network landscape.
What Is SEAL in 3GPP Architecture?
SEAL (Service Enabler Architecture Layer) is a standardized framework established by 3GPP (in TS 23.434) to support vertical applications that function on mobile networks.
It offers core enablers—like group management, location tracking, configuration, and security—that can be reused across different application services.
Key Objectives of SEAL:
Enable cross-industry application support over 3GPP networks.
Provide secure, scalable, and interoperable communication between VAL entities.
Support both UE-based (User Equipment) and server-based functions.
Simplify service deployment across various vertical fields.
In short, SEAL acts like a middleware layer, bridging the gap between application services (VAL) and the network functions of 3GPP.
Overview of the Functional Model (Based on the Image)
The diagram titled “Functional Model” illustrates how SEAL and VAL components interact with one another and with the 3GPP network system.
The architecture consists of three main domains:
User Equipment (UE)
3GPP Network System
VAL Server Domain
Each domain has unique roles and communication interfaces—identified as VAL-UU, SEAL-C, SEAL-UU, and SEAL-S—that outline the data exchange paths between clients and servers.
User Equipment (UE)
The UE hosts two primary types of entities:
VAL Clients
SEAL Clients
These components work in tandem to provide communication and service logic for vertical applications running on end devices—think connected cars, smart sensors, or industrial controllers.
VAL Clients
VAL (Vertical Application Layer) clients are application-specific modules that implement logic for specific use cases—like vehicle communication, remote surgeries, or smart grid control. They interact directly with VAL Servers using the VAL-UU interface.
SEAL Clients
The SEAL Client(s) function as the middleware on the UE side. They deliver a variety of common enabler services to VAL clients—like identity management, group communication, and configuration—through SEAL-C.
Types of SEAL Clients:
Client Type Function Group Management Client Manages VAL group memberships and session info. Location Management Client Provides device geolocation services and updates. Configuration Management Client Handles configuration syncing between UE and server.ID Management Client Safeguards user and device identifiers. Key Management Client Manages the distribution and lifecycle of cryptographic keys. Network Resource Management Client Connects with network-level functions for resource allocation.
These SEAL Clients communicate with their respective SEAL Servers using the SEAL-UU interfaces.
- 3GPP Network System
The 3GPP Network System is the heart of the architecture, enabling connectivity between the UE and the VAL/SEAL Servers.
It manages both control plane (signaling) and user plane (data) communications over standardized interfaces like:
N5
Rx
xMB-C
MB2-C
TB
These interfaces facilitate network-aware service management, QoS control, and resource orchestration, ensuring that SEAL-based communications meet the latency, reliability, and security needs of 5G verticals.
- VAL Server and SEAL Server Domains
On the right side of the model, you'll find the VAL Server(s) and SEAL Server(s) that exist within the application domain.
VAL Servers
These servers manage application-specific logic, providing services to VAL clients through the VAL-UU interface. Examples include:
Vehicle data analytics servers for automotive cases.
Patient monitoring servers for eHealth solutions.
Energy management servers in smart grids.
SEAL Servers
The SEAL Servers carry out enabler functions that back VAL services. Each SEAL Server takes charge of a specific enabler domain, ensuring consistent and secure management of application resources.
Interfaces in SEAL Functional Model
The power of SEAL lies in its well-defined interface structure, which guarantees interoperability and modularity.
Interface Direction Function VAL-UU Between VAL Client and VAL Server Application-specific communication. SEAL-C Between VAL Client and SEAL Client Interface for service enabler access. SEAL-UU Between SEAL Client and SEAL Server Core enabler communication for group, location, and identity services. SEAL-S Between VAL Server and SEAL Server Coordination and resource sharing between servers.
This layered strategy allows VAL applications to leverage SEAL functionalities without needing to reimplement core communication or security measures.
How SEAL Enhances Vertical Applications
The SEAL Functional Model offers essential capabilities that boost vertical applications in 5G environments.
Key Benefits:
Reusability: Common service enablers (like identity and group management) can be utilized across various applications.
Interoperability: Standardized interfaces guarantee smooth communication across different devices and manufacturers.
Security: Embedded key and identity management systems protect both signaling and data exchanges.
Scalability: Accommodates extensive IoT deployments and high-mobility situations like V2X (Vehicle-to-Everything).
Efficiency: Centralized management minimizes signaling overhead and enhances system performance.
Use Cases of SEAL Functional Model
The SEAL architecture is crucial for enabling key vertical services in 5G, including:
V2X Communication (Vehicle-to-Everything): Manages secure communications between vehicles and infrastructure through SEAL’s identity and group management.
Mission-Critical Communications: Ensures dependable and prioritized message handling for emergency responses and defense applications.
Smart City Applications: Combines IoT device identity, location, and network management for streamlined urban infrastructure monitoring.
Industrial Automation (IIoT): Facilitates real-time configuration and control of devices in factory settings.
Functional Flow Example
Here’s a step-by-step look at how the SEAL functional model works:
A VAL Client (like a connected car app) kicks off a session through the SEAL Client.
The SEAL Client asks the SEAL Server for identity and group info.
The 3GPP Network System verifies credentials and allocates resources.
The SEAL Server sends back authorized session parameters.
The VAL Client securely communicates with the VAL Server to exchange application data.
This modular interaction guarantees security, control, and efficiency at every step.
Conclusion
The SEAL Functional Model stands as a fundamental component of 3GPP’s mission to standardize and enhance vertical application support in 5G networks.
By separating application logic (VAL) from enabling services (SEAL) and establishing clear interfaces for each interaction, SEAL delivers a scalable, secure, and interoperable framework for next-gen vertical services.
Whether it’s powering self-driving cars, mission-critical communications, or large-scale IoT systems, SEAL ensures that 3GPP networks remain adaptable, dependable, and prepared for future advancements.
