5G AUSF Authentication Server Function Explained: Workflow and Interactions in 5G Core

5G AUSF – A Closer Look at Authentication Server Function Interactions
One of the standout features of 5G technology is its robust security architecture. This system is built to safeguard user identities, secure access to the network, and accommodate various authentication methods. At the heart of this structure is the AUSF (Authentication Server Function), which plays a vital role in handling and verifying authentication procedures between the User Equipment (UE) and the 5G Core (5GC) network.
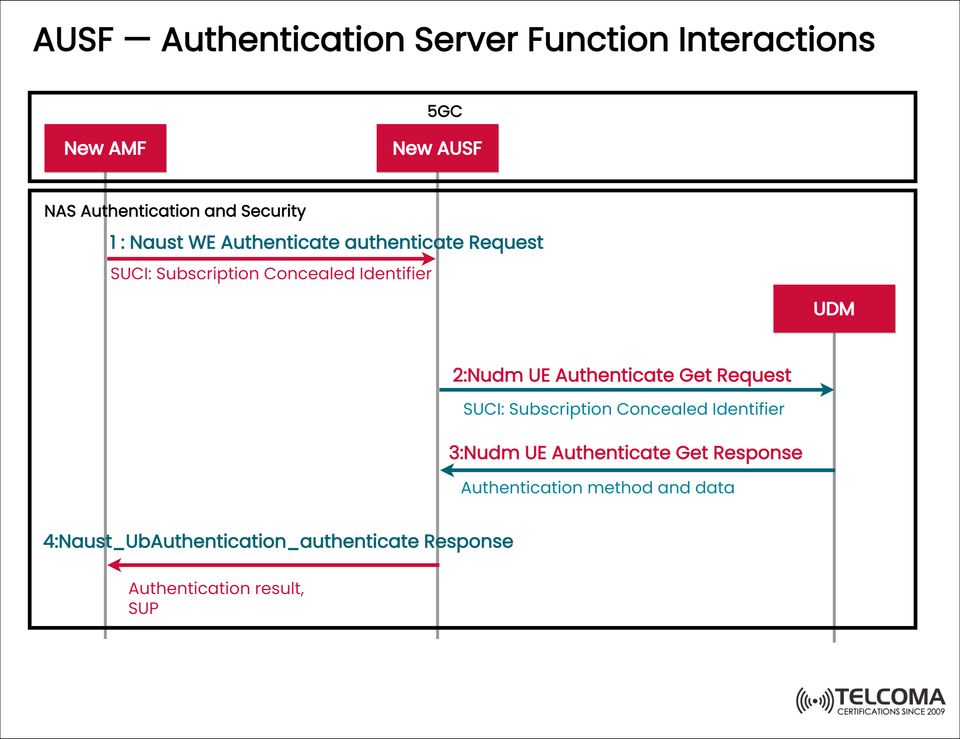
The image labeled “AUSF — Authentication Server Function Interactions” offers a straightforward visual representation of how the New AMF, AUSF, and UDM work together during the authentication phase. Let’s dive into the details to see how these interactions make sure only authorized users can connect to the 5G network securely.
- What Exactly is AUSF in the 5G Core?
The Authentication Server Function (AUSF) is an essential piece of the 5G Core (5GC), tasked with validating a subscriber’s identity using credentials stored in the Unified Data Management (UDM) function.
Its responsibilities include:
Overseeing authentication processes initiated by the Access and Mobility Management Function (AMF).
Communicating with the UDM to gather authentication vectors and subscriber data.
Supporting various authentication methods, like 5G-AKA and EAP-AKA'.
Delivering authentication results back to the AMF.
As a component of the 5G Service-Based Architecture (SBA), the AUSF allows other network functions (NFs) to tap into its services through secure service-based interfaces (SBIs) using HTTP/2 protocols.
- The Authentication Process in 5G
In the realm of 5G, authentication is all about ensuring that both the user (UE) and the network can confirm each other's identities. This process relies on the ideas of Subscription Concealed Identifier (SUCI) and Subscription Permanent Identifier (SUPI).
SUPI: The actual permanent identifier for the subscriber, which is similar to IMSI in LTE.
SUCI: A hidden version of SUPI, used to keep the user’s identity safe during transmission.
When a UE tries to connect, it sends the SUCI to the AMF, which starts the authentication process through the AUSF and UDM.
- Detailed Breakdown of AUSF Interaction Sequence
The depicted image outlines a four-step process that shows how messages flow between the AMF, AUSF, and UDM during authentication. Let’s take a closer look at each step:
Step 1: Nausf WE Authenticate Request
The New AMF sends an Authenticate Request to the AUSF.
The message contains:
SUCI (Subscription Concealed Identifier): The concealed identity of the UE.
Optional parameters related to network slice or service request.
Purpose:
To kick off the authentication process by passing the UE’s hidden identity to the AUSF for verification.
What Happens Behind the Scenes:
The AUSF decodes the SUCI and gets ready to obtain the necessary authentication data from the UDM.
Step 2: Nudm UE Authenticate Get Request
The AUSF issues a Get Request to the UDM using the Nudm_UEAuthentication service.
This request includes:
SUCI – for fetching subscription information.
Authentication Type – indicating which method to use (like 5G-AKA or EAP-AKA’).
Purpose:
To ask the UDM for authentication vectors or credentials based on the subscriber identity provided by the AMF.
Step 3: Nudm UE Authenticate Get Response
The UDM replies to the AUSF with:
Authentication Method – either 5G-AKA or something based on EAP.
Authentication Data – keys and cryptographic values essential for authentication.
Response Example for 5G-AKA:
RAND (Random Challenge)
AUTN (Authentication Token)
HXRES* (Expected Response)
K ext{_AUSF} (Key created for securing communication)
Purpose:
This gives the AUSF the info it needs to verify the user and set up secure communication.
Step 4: Nausf Ub Authentication Authenticate Response
The AUSF sends back an Authenticate Response to the New AMF.
This message includes:
Authentication Result – whether it was successful or not.
SUP (Subscription Permanent Identifier) – if the authentication was successful.
Purpose:
To finalize the authentication process and let the AMF know that the subscriber has been confirmed. After receiving this, the AMF can establish a secure signaling connection and start the session setup.
Security Features in AUSF Interactions
The AUSF boosts security through multiple protective layers and privacy strategies:
a. Subscription Concealed Identifier (SUCI):
Shields the user’s permanent identity (SUPI) by encrypting it with the home network's public key.
Stops IMSI-catching attacks and eavesdropping.
b. Mutual Authentication:
Both the UE and the network confirm each other’s authenticity.
Helps fend off rogue base station or man-in-the-middle attacks.
c. Key Derivation and Distribution:
AUSF creates and shares the K ext{_SEAF} (Key for SEAF) with the AMF for ongoing secure dialogues.
Guarantees encrypted NAS signaling between UE and AMF.
Authentication Methods Supported by AUSF
The AUSF accommodates several authentication frameworks as outlined by 3GPP TS 33.501:
Authentication Method Description Use Case5G-AKABased on the LTE AKA method, with improved key separation. Main authentication method for 3GPP access. EAP-AKA'A variation of Extensible Authentication Protocol for non-3GPP access. Used in Wi-Fi offload and untrusted access. EAP-TLS Authentication using certificates. Typically in enterprise or private 5G networks.
Each method ensures that the subscriber’s identity and session keys stay protected, no matter how they are connecting.
Advantages of AUSF in the 5G Core
The AUSF’s role in the 5G security architecture offers numerous advantages for users and operators alike:
Better Identity Protection: Thanks to SUCI encryption and concealed identifiers.
Versatile Authentication: Supports various methods for both 3GPP and non-3GPP access.
Scalability: Its stateless design and SBA integration enable dynamic scaling according to demand.
Interoperability: Works effortlessly with UDM, AMF, and SEPP across roaming environments.
Secure Key Management: Establishes and distributes cryptographic keys securely.
Quick Summary of Authentication Flow
Step Entity Action Key Data1AMF → AUSFNausf_WE Authenticate RequestSUCI2AUSF → UDM Nudm_UE Authenticate Get RequestSUCI3UDM → AUSF Nudm_UE Authenticate Get Response Auth Method & Data4AUSF → AMFNausf_Ub Authentication Authenticate Response Auth Result & SUP
This streamlined flow promotes both security and efficiency, ensuring that sensitive identities and keys are exchanged over encrypted channels.
Real-World Implementation Insights
In real-world scenarios:
AUSF is usually deployed in cloud-native network functions (CNFs) within the 5G core.
It interacts through RESTful APIs using HTTP/2 and JSON payloads.
Operators may set up duplicate AUSF instances for load balancing and failover protection.
Integrating with the UDM is crucial for accessing subscriber data, especially for multi-network or roaming authentication.
Final Thoughts
The AUSF (Authentication Server Function) is a foundational element of the 5G security framework, ensuring that anyone connecting to the network is verified and authorized.
Through smooth interactions with the AMF and UDM, the AUSF facilitates:
Secure identity protection utilizing SUCI and SUPI.
Mutual authentication between the UE and the network.
Effective key management for encrypted communication.
The sequence illustrated in the AUSF Interaction Diagram emphasizes the organized and logical communication flow within the 5G Core (5GC), highlighting the sophistication and security that sets 5G apart from previous technologies.
