5G Identity Exchange Explained: SUPI, SUCI, and GUTI Authentication in 5G Networks

Identity management is crucial for keeping mobile communication secure. In LTE (4G), the exposure of IMSI created some vulnerabilities, like IMSI catchers. With 5G, there's a shift towards a privacy-first approach, which keeps permanent identifiers under wraps while still allowing for smooth authentication and mobility.
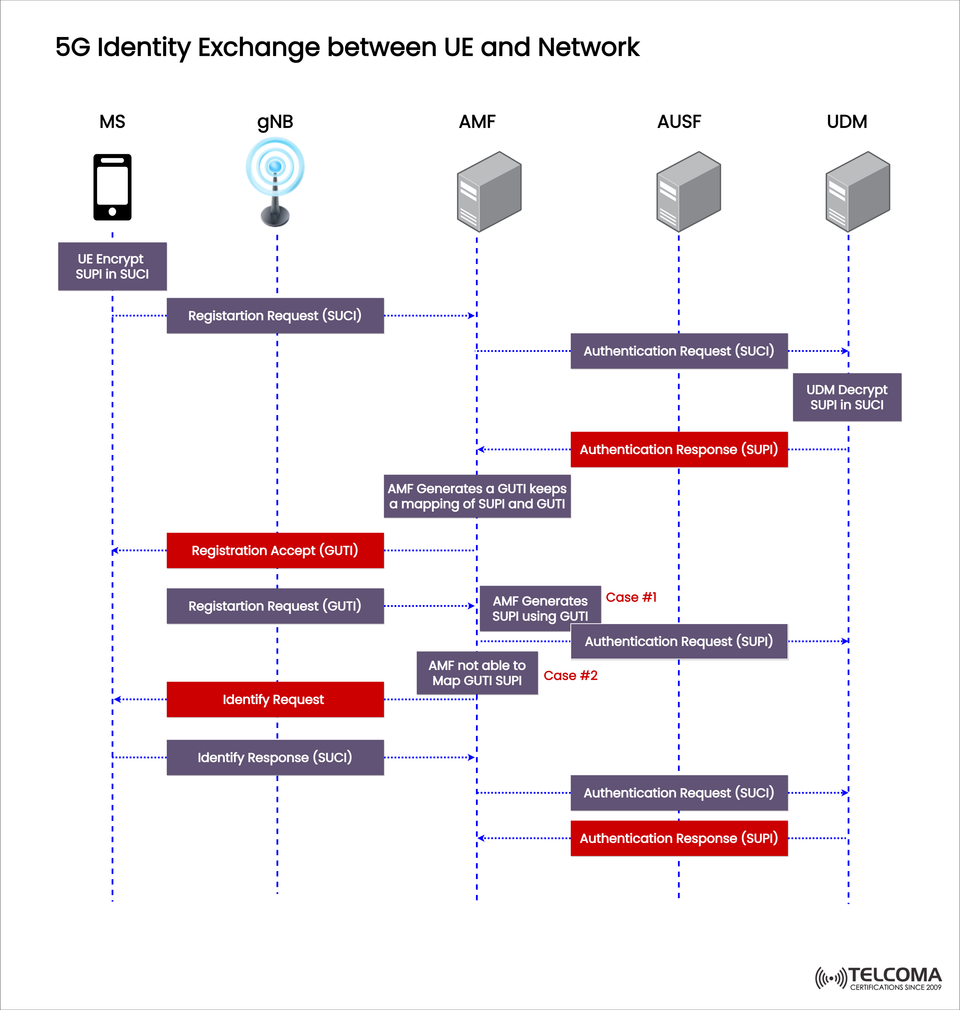
The diagram you've uploaded shows how the identity exchange in 5G works securely between the UE (User Equipment) and the core network using SUPI (Subscription Permanent Identifier), SUCI (Subscription Concealed Identifier), and GUTI (Globally Unique Temporary Identifier).
Key Players in 5G Identity Exchange
Before we dive into how it all flows, let’s outline the main players involved:
UE (User Equipment): This is basically the smartphone or IoT device that kicks off the registration.
bThis is the 5G base station that manages radio access.
AMF (Access and Mobility Management Function): This oversees registration, mobility, and security context.
AUSF (Authentication Server Function): This deals with authentication requests and responses.
UDM (Unified Data Management): It stores permanent subscriber data—like SUPI—and handles the decryption of SUCI.
These components together create the 5G core security and mobility framework.
Step-by-Step: 5G Identity Exchange Flow
Let’s break down the process into initial registration and subsequent registrations with GUTI.
- Initial Registration: Secure Start with SUCI
Step 1: The UE encrypts its permanent identity (SUPI) into a SUCI using the home network’s public key.
Step 2: The UE sends a Registration Request (SUCI) to the network via the gNB.
Step 3: The AMF forwards this request to the AUSF and UDM.
Step 4: The UDM decrypts SUCI to get the SUPI.
Step 5: The AUSF creates an Authentication Request and sends it back.
Step 6: The UE responds with an Authentication Response (SUPI) to confirm its identity.
Benefit: The SUPI never travels in clear text, which reduces the risks of interception and identity theft.
- GUTI Assignment: Temporary Identity for Privacy
After successful authentication, the AMF generates a GUTI (Globally Unique Temporary Identifier).
This GUTI gets sent to the UE in the Registration Accept message.
From then on, the UE uses GUTI instead of SUCI for quicker, privacy-preserving registration.
Why GUTI?
It cuts down signaling overhead by avoiding the need to encrypt SUCI for every registration.
It prevents the frequent exposure of permanent identifiers.
Lets the AMF quickly identify users on the move.
- Subsequent Registrations: Using GUTI
Step 1: The UE sends a Registration Request (GUTI) to the AMF.
Case #1: If the AMF maps GUTI to SUPI successfully → An Authentication Request (SUPI) is initiated.
Case #2: If the AMF can’t map GUTI to SUPI → The UE has to resend SUCI again (through the Identify Request/Response flow).
This dual-path method provides resilience: if GUTI mapping fails or becomes invalid, the network defaults back to SUCI.
Step-by-Step Flow
- Initial Registration (SUCI)
The User Equipment (UE) encrypts the Subscription Permanent Identifier (SUPI) into a Subscription Concealed Identifier (SUCI).
Then, it sends a Registration Request containing the SUCI through the gNodeB (gNB).
The Access and Mobility Management Function (AMF) passes the SUCI to the Authentication Server Function/Unified Data Management (AUSF/UDM).
The UDM decrypts the SUCI, recovering the SUPI.
AUSF then validates the identity and sends back the Authentication Response.
- GUTI Assignment
The AMF assigns a Globally Unique Temporary Identifier (GUTI).
This is included in the Registration Accept message.
The UE saves this for future reference.
Subsequent Registration (GUTI)
The UE sends a Registration Request using the GUTI.
Case #1: If the AMF can map the GUTI back to the SUPI, the authentication process continues.
Case #2: If the mapping fails, it leads to an Identity Request, and the UE will then resend the SUCI.
Privacy Features in Exchange
The SUPI is never exposed, always remaining encrypted within the SUCI.
The GUTI refresh mechanism helps in preventing tracking.
There’s a fallback mechanism in place to ensure reliability, even if the mapping fails.
Cases in Identity Handling
The diagram shows two significant scenarios:
Case #1 (Success): * The AMF accurately maps GUTI to SUPI. * Authentication proceeds smoothly with minimal overhead. * Faster re-registration and reduced network signaling.
Case #2 (Fallback): * The AMF can’t map GUTI to SUPI. * The UE responds with SUCI in the Identity Response. * UDM decrypts SUCI, and authentication continues from there.
This layered approach helps ensure both speed and reliability while keeping user privacy intact.
SUPI, SUCI, and GUTI in Context
Let’s clarify the three identifiers used in 5G authentication:
SUPI (Subscription Permanent Identifier): * This is like IMSI in LTE. * It's permanent and highly sensitive. * It’s never sent in plaintext.
SUCI (Subscription Concealed Identifier): * This is the encrypted version of SUPI. * It’s sent during the initial registration. * Protects against IMSI-catcher attacks.
GUTI (Globally Unique Temporary Identifier): * Assigned after successful authentication. * Used for future registrations. * It refreshes regularly for extra privacy.
Why 5G Identity Exchange is More Secure than LTE
LTE networks used temporary identifiers (GUTI) but often transmitted the IMSI in plaintext during initial registration, leaving users vulnerable to IMSI catchers.
5G addresses this with:
SUCI encryption → Keeping the permanent identity concealed.
Frequent GUTI refresh → Makes it trickier for attackers to track users.
Fallback logic (Case #2) → This ensures continuous service without compromising privacy.
📊 LTE vs 5G Identity Exchange
FeatureLTE5GPermanent ID (IMSI/SUPI) exposure Yes (IMSI can be clear)No (SUPI always encrypted in SUCI)Temporary IDGUTIGUTI (more robust)Authentication entities MME, HSSAMF, AUSF, UDM Privacy level Medium High
Practical Benefits for Telecom Professionals
For telecom engineers and network planners, 5G identity management offers:
Better subscriber privacy → More protection against interception.
Efficient signaling → GUTI cuts down the repetitive encryption/decryption cycles.
Roaming support → Secure identity exchange works across different networks.
IoT readiness → Lightweight identity management handles massive device connectivity.
Conclusion: Identity Exchange as the Pillar of 5G Security
The 5G Identity Exchange process guarantees that mobile users are authenticated securely without revealing their permanent identifiers.
By combining SUPI (permanent ID), SUCI (encrypted ID), and GUTI (temporary ID) with smart fallback mechanisms, 5G achieves a solid balance of security, efficiency, and privacy.
For telecom professionals, grasping this identity exchange flow is vital as it underpins secure mobility management, authentication, and roaming in 5G networks.
