5G NAS Authentication and Security Procedure Explained: Step-by-Step Call Flow
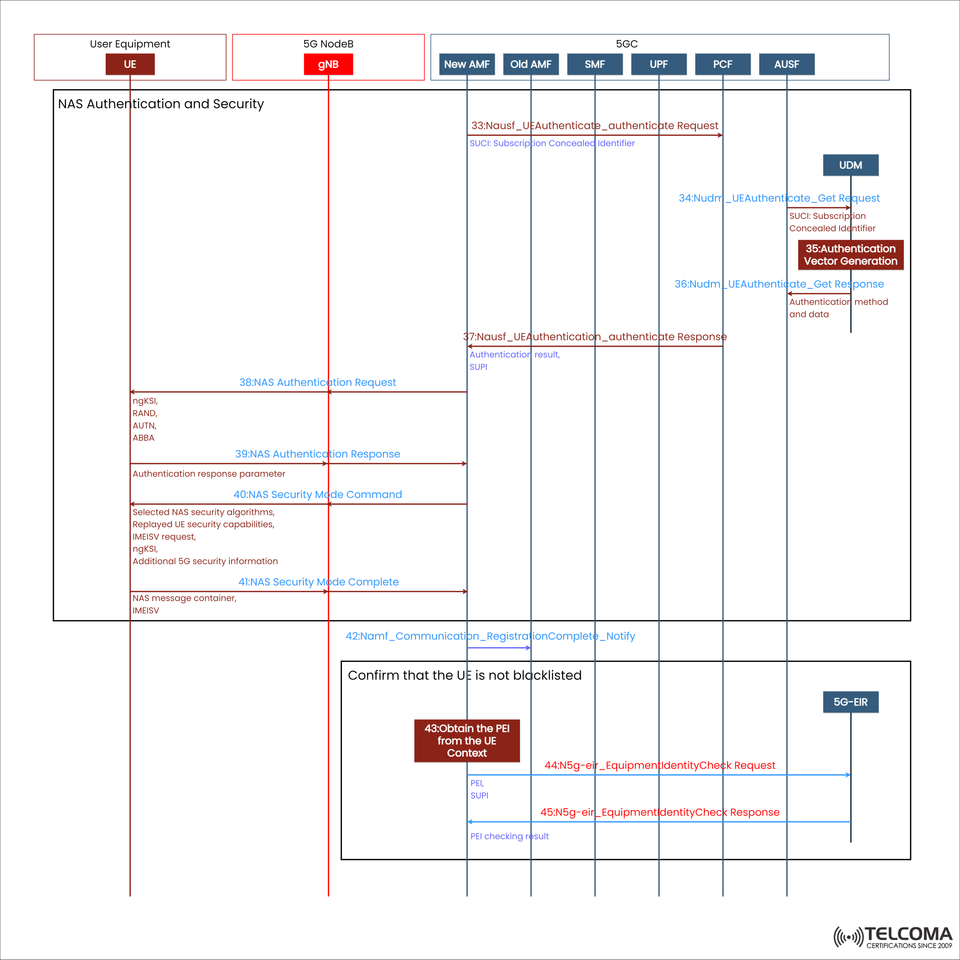

Explaining the 5G NAS Authentication and Security Call Flow
In 5G networks, the NAS (Non-Access Stratum) Authentication and Security processes are vital for confirming user identities and safeguarding data exchange between User Equipment (UE) and the 5G Core (5GC). This system ensures that only authorized users and devices can connect securely to the network.
The chart above details this process through a step-by-step signaling flow, involving several 5G components:
UE (User Equipment)
gNB (5G Node B)
AMF (Access and Mobility Management Function)
AUSF (Authentication Server Function)
UDM (Unified Data Management)
EIR (Equipment Identity Register)
Each of these parts plays a role in verifying user identity, setting up encryption, and confirming that equipment is legit before providing access to 5G services.
Getting to Know the 5G NAS Authentication and Security Framework
What’s NAS Authentication?
NAS Authentication in 5G checks that the user is who they say they are, using methods like 5G-AKA (Authentication and Key Agreement) or EAP-AKA’. This process includes cryptographic exchanges between the UE, AMF, AUSF, and UDM.
Why Does It Matter?
Stops unauthorized access to the network
Shields against identity theft and spoofing
Sets up secure communication channels
Allows for mutual authentication (where both UE and network verify each other)
Key Entities and Their Roles
Entity Full Form Role in Authentication UE ser Equipment Starts registration and responds to authentication challengesgNB5G Node B Relays NAS messages between UE and AMFAMF Access and Mobility Management Function Manages NAS signaling and requests authentication from AUSFAUSF Authentication Server Function Validates authentication responses and interacts with UDMUDM Unified Data Management Stores subscriber credentials and creates authentication vectors EIR Equipment Identity Register Confirms device identity (IMEI/PEI) against blacklist
Breaking Down the 5G NAS Authentication Process
Let’s go through the key signaling steps shown in the diagram:
Step 33: AUSF Authentication Request
The AMF kicks things off by sending a Nau sf_ UE Authentication _ authenticate Request to the AUSF.
Input: SUCI (Subscription Concealed Identifier)
Purpose: To ask for subscriber authentication info.
The SUCI secures the SUPI (Subscription Permanent Identifier) with public key encryption, keeping the user’s permanent ID private.
Step 34: Request for UDM Authentication Vector
Next, the AUSF sends a Nudm_UEAuthenticate_Get Request to the UDM, again including the SUCI.
This prompts the UDM to create authentication vectors (AVs) for this particular subscriber.
Step 35: Generating Authentication Vectors
The UDM carries out cryptographic operations to produce authentication vectors, which include:
RAND: A random challenge
AUTN: An authentication token
HXRES*: The expected response hash
Kseaf: A session key for AMF
These AVs are sent back to the AUSF in the Nudm_ UE Authenticate _ Get Response. This step is crucial since these parameters set the stage for secure authentication.
Step 37: AUSF Authentication Response
The AUSF passes the response along to the AMF with the Nau sf_ UE Authentication _ authenticate Response, containing the authentication result and SUPI.
Step 38: Request for NAS Authentication
The AMF then sends a NAS Authentication Request to the UE through the gNB, including:
RAND
AUTN
ABBA (Anti-Bidding-Down parameter)
NgKSI (NAS key set identifier)
This prompts the UE to compute its own authentication response using its stored subscriber key.
Step 39: Response to NAS Authentication
The UE calculates a RES* (response value) using RAND and its key, then sends it back in a NAS Authentication Response to the AMF. The AMF checks this response against HXRES* from the AUSF to verify authentication.
Step 40: Sending NAS Security Mode Command
After successful authentication, the AMF sends a NAS Security Mode Command to the UE, specifying:
The selected NAS encryption and integrity algorithms
Replay protection parameters
Additional 5G security information
This ensures that the next messages are securely encrypted.
Step 41: Completing NAS Security Mode
The UE replies with NAS Security Mode Complete, indicating that it has activated the chosen security algorithms and is ready for encrypted NAS signaling.
Step 42: Notifying Registration Completion
The AMF then notifies other network functions (like SMF or PCF) that registration is done via Namf_Communication_RegistrationComplete_Notify.
At this point, the UE is authenticated and securely linked to the 5G Core.
Validating Equipment Legitimacy (PEI Check)
Aside from user authentication, 5G also checks the device itself through the PEI (Permanent Equipment Identifier).
Step 43: Getting PEI from UE Context
The AMF pulls the PEI (generally the IMEI) from the UE context.
Step 44: Requesting Equipment Identity Check
The AMF sends a N5g-eir_EquipmentIdentityCheck Request to the EIR, including:
PEI
SUPI
The aim here is to confirm that the device isn’t blacklisted (like being reported stolen).
Step 45: Response to Equipment Identity Check
The EIR gets back to the AMF with a N5g-eir_EquipmentIdentityCheck Response, indicating whether the device is allowed, unknown, or blacklisted.
If it’s confirmed as legitimate, the registration wraps up successfully.
Security Parameters and Algorithms Involved
Parameter Description RAND Random challenge produced by UDMAUTN Authentication token that verifies network authenticity RESUE’s computed response to RANDHXRES The expected hash of RES* stored in AUSFN g KSI Identifies the NAS key set K sea f Key created for security between UE and AMFABBA Protects against algorithm downgrade attacks
Key Advantages of NAS Authentication in 5G
Mutual Authentication: Both the UE and the network validate each other’s legitimacy.
Enhanced Privacy: SUCI conceals the permanent subscriber identity.
Improved Security Algorithms: Based on 256-bit encryption and integrity protection.
Equipment Validation: Ensures that only authorized devices can access the network.
Seamless Mobility: Authentication is compatible across AMFs and gNBs.
Tackling Common Authentication Problems
Typical Failure Points:
Issues with AV generation in the UDM
Network time sync problems affecting RAND/AUTN checks
UE key mismatches due to outdated SIM/USIM profiles
EIR not being available, leading to device rejection
Best Practices:
Keep AUSF-UDM sync for key creation
Regularly update subscriber data
Validate the PEI database often
Enable mutual authentication logs for auditing purposes
Final Thoughts
The 5G NAS Authentication and Security approach is crucial for making sure that only authorized users and devices can tap into the 5G Core Network. By combining cryptographic authentication, establishing NAS security modes, and verifying equipment, 5G offers strong protection against unauthorized access and identity fraud.
This detailed flow—from Nau sf _UE Authentication_ authenticate Request to Equipment Identity Check Response—shows how various network functions work together to create a secure, trustworthy connection between users and the 5G core infrastructure.
As 5G keeps developing, it’s essential for telecom engineers, network architects, and cybersecurity professionals to master these authentication steps for building resilient, future-ready networks.
