DU Virtualization Architecture in 5G Networks: Components, Layers, and Integration
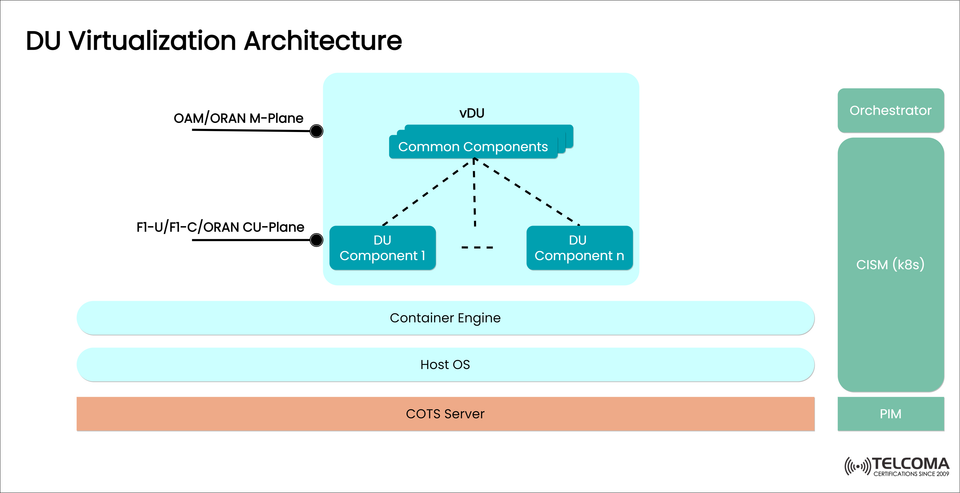

DU Virtualization Architecture Explained
As 5G continues to become more ubiquitous, the virtualization of Distributed Units (DUs) is a fundamental aspect of sufficiently scalable, resource-efficient, and flexible Radio Access Network (RAN) deployments. In this blog, I will explain DU Virtualization Architecture as depicted in the diagram, touching on its primary components, layered architecture, and orchestration ecosystem.
What is DU Virtualization (DU virtualization)?
DU virtualization is the process of deploying Distributed Unit (DU) functionality as software components—called vDU (virtual DU)—on standard commercial off-the-shelf (COTS) hardware, allowing for flexible scalability, hardware independence and centralized orchestration of the RAN in 5G networks.
Architecture Overview: Key Components
The image illustrates the DU virtualized architecture with the components below:
🔹 vDU (vDU)
Host multiple DU Components (DU Component 1 to n)
Contains Common Components that are common across DU functionalities
Communicates with CU (Central Unit) and OAM
🔹 Interface Planes
F1-U / F1-C / ORAN CU-Plane: Path for data and control communications with CU
OAM / ORAN M-Plane: for managing and monitoring the network
🔹 Contextual Execution Environment Layers
Layer Description
COTS Server Commodity hardware stack for virtualization
Host OS Operating system that manages the hardware stack and provides base OS services
Container Engine Software that harnesses the operating system, enabling containerized.
Orchestration and Management Components
☁️ CISM (Cloud Infrastructure and Service Management - Kubernetes)
Provides lifecycle management of vDU components using Kubernetes (k8s)
Provides scaling, deployment, and health management
🧩 Orchestrator
Controls service composition and auto-deployment of services across the virtualized network
⚙️ PIM (Platform Infrastructure Manager)
Manages platform resources
Communicates with CISM for orchestration of resources
Advantages of DU Virtualization in 5G
✅ Scalability: Easily scale DU components up/down based on demand
✅ Interoperability: Follows O-RAN standards for open architecture and interoperability with vendors
✅ Lower CAPEX/OPEX: Cost-driven model enabled by utilization of inexpensive COTS hardware instead of proprietary systems
✅ Quick Deployment: Deployment based on containers significantly reduces time to market
✅ Single Point of Control: Provides common management through Kubernetes and orchestration tools
Summary Table:
DU Virtualization Stack
Layer Example Technologies
DU Components PHY, MAC, RLC, RRC modules
Container Engine Docker, containerd
Host OS Linux-based OS
COTS Server x86 servers
Orchestration Layer Kubernetes (CISM), Helm
Management & Monitoring OAM, M-plane, Orchestrator
Conclusion
The DU Virtualization Architecture is a fundamental component for contemporary 5G deployments, creating an environment for a disaggregated, software-defined RAN ecosystem. By leveraging cloud-native principles (containers, Kubernetes orchestration, and COTS hardware), service providers can increase flexibility and performance in their networks while lowering costs. The architecture will be fundamental to enable scalable and future-proof 5G RAN deployments.
Detailed Review of DU Components
🔧 Common Components
These are the shared libraries and services used by all DU components. These generally take care of:
Time Sync (PTP/eCPRI sync)
Intra-component Communications
Logging, tracing, and diagnostics
Security functions (authentication and encryption)
📦 DU Component Instances
Ultimately, each DU component has a specific Layer 1 (PHY), Layer 2 (MAC, RLC), and Layer 3 (PDCP, RRC) processing functions. As deployed as containers, this means:
Granular scale (add/remove containers based on traffic)
Fault isolation (crashing one component does not remove the service provided by the other components)
Easier updates and patches
Role of the Kubernetes (CISM) Layer in DU Virtualization
The Cloud Infrastructure and Service Management (CISM) layer powered by Kubernetes (k8s) provides, among others:
Automated scaling: during peak traffic hours, automatically add replicas of DU components
Self-healing: automatically restarts failed containers
Declarative deployments: Infrastructure-as-code via Helm charts
Service discovery: makes sure that one container can communicate with other containers
Kubernetes supports the hybrid-cloud or edge-cloud deployment of the vDUs to provide compute closer to the radio units (RUs) and minimize latency.
Orchestrator & PIM: Network-Wide Intelligence
🔄 Orchestrator
Integrates with the MANO (Management and Network Orchestration) layer of ETSI NFV architecture
Makes the placement decisions: which COTS server to run which vDU container
Enables OSS/BSS service management
🧱 Platform Infrastructure Manager (PIM)
Keeps an eye on hardware's health, power consumption, and performance
Ensures resource utilization meets SLAs
Triggers alarms, or migrations if physical resources are overloaded or failure occurs
Deployment Models for DU Virtualization
Deployment Type Characteristics Use Case
On-Prem (Edge) Low-latency, near RU, few hops Dense urban networks
Private Cloud Enterprise-managed, full control Industrial campuses, smart factories
Public Cloud Highly scalable, subscription-based Rural/low-density or trial networks
Hybrid deployments are also common, where some management functions can be in the cloud while the real-time DU workload is hosted on edge infrastructure.
DU Virtualization in Alignment with O-RAN
This architecture is in keeping with principles behind O-RAN Alliance as follows:
Open interface definitions: F1, E1, O1, A1, and E2
Cloud-native deployment and support for CNFs (containerized network functions) over containers
Disaggregation of vendor solutions: ability to run software from one vendor on hardware from another
Support for AI/ML based applications: can intelligently scale DUs or heal DUs based on xApps/rApps
Key Takeaways
Virtualized DU architecture enables open, scalable, and intelligent 5G networks. Telecom operators that deploy this architecture can benefit from:
Faster time to market for new features to subscribers,
Enablement of multi-vendor deployment with high levels of interoperability,
Choice of deployment option - on-premises or based in the cloud,
Alignment to O-RAN, ETSI NFV, and cloud-native computing principles.
When deploying vDUs, we must consider performance tuning both software and hardware to satisfy the real-time demands of radio signal processing.
✅ What matters?
Low Latency Processing: Done through CPU pinning, tuning the realtime kernel, and NUMA aware scheduling
High Throughput: Done with adding DPDK enabled NICs for fast packet processing
Deterministic Timing: Done with PTP (Precision Time Protocol) support across the vDU containers
Hardware Acceleration: Done with FPGA, SmartNICs, or GPU to offload PHY layer processing
⚙️ Performance Optimization Suggestions:
Use isolation techniques (e.g. CPU affinity for DU only cores)
Use hugepages for faster memory access
Apply SR-IOV (Single Root I/O Virtualization) for direct NIC access for containers
Security within the DU virtualized architecture
From a containerized framework, security is increasingly difficult, and as important.
🔒 Security considerations:
Container hardening: Use minimal images, non-root containers
Runtime protection: use Falco or AppArmor monitoring containers for malicious behavior
RBAC policies: Role-based access control within Kubernetes
Zero trust: implement mutual TLS between the DU microservices and management layer
🔍 Monitoring tools:
Prometheus + Grafana: use for metrics collection and displaying
ELK stack to centralize logs and analysis
Service mesh (e.g. Istio) to enforce policy and improve observability
