Enhancing IMS Security: How NEC’s IMS Products Protect VoLTE and IP Networks

Boosting IMS Security: How NEC’s IMS Solutions Safeguard VoLTE and IP Networks
As telecom networks shift towards all-IP architectures, the IP Multimedia Subsystem (IMS) has emerged as a critical framework for delivering VoLTE, VoNR, and multimedia services. But with this IP-centric setup comes a host of cyber threats that can target both the signaling and media planes.
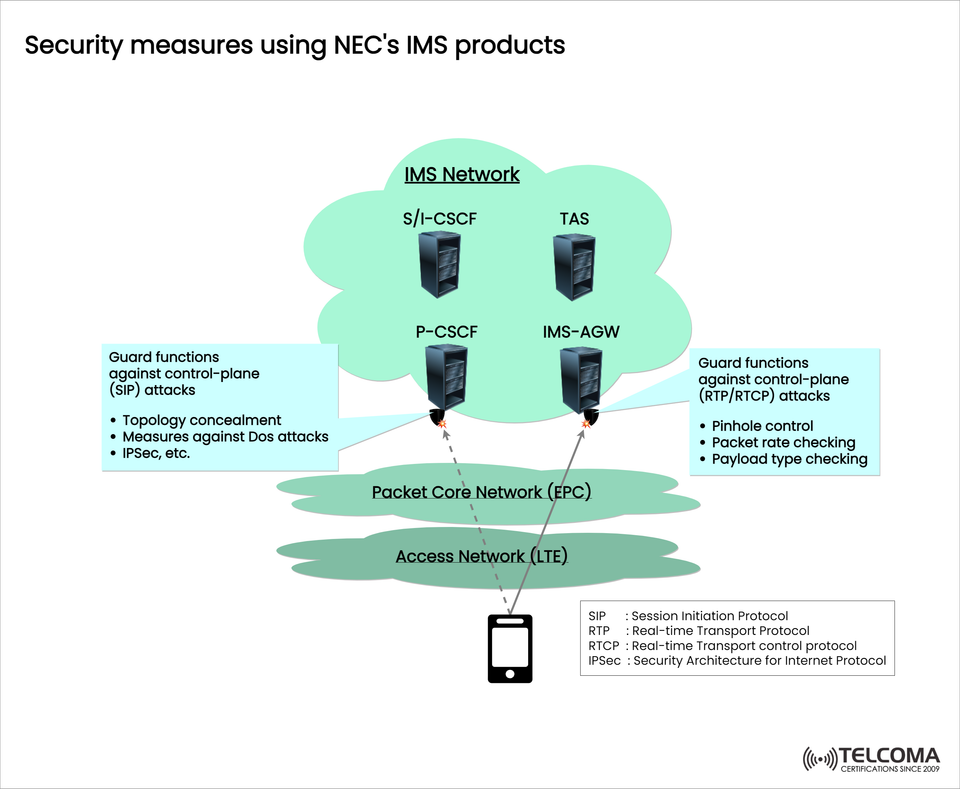
To tackle these challenges, NEC’s IMS products come with strong security features designed to shield both the control-plane and user-plane traffic. The diagram we've included illustrates how NEC’s IMS elements — like the P-CSCF, S/I-CSCF, TAS, and IMS-AGW — deploy layered defenses that guarantee service integrity, data confidentiality, and network resilience.
Grasping IMS Security in Contemporary Telecom Networks
The IP Multimedia Subsystem (IMS) manages voice, video, and data sessions over LTE and 5G networks, taking care of essential tasks like registration, authentication, call setup, and media routing.
However, since IMS operates on IP, it’s subject to the same vulnerabilities common to any IP system — think denial of service (DoS) attacks, spoofing, session hijacking, and protocol exploitation.
NEC’s IMS framework addresses these vulnerabilities with integrated guard functions that monitor, filter, and secure traffic across both signaling and media layers.
Security Layers in NEC’s IMS Structure
The diagram we provided showcases two key protection areas in NEC’s IMS security framework:
Control Plane Security — Safeguards SIP (Session Initiation Protocol) signaling traffic.
User Plane Security — Defends RTP/RTCP (media transport) data streams.
These layers are reinforced by means of encryption, firewalls, rate limiting, and protocol validation, ensuring comprehensive protection from access to the core network.
Guard Functions Against Control-Plane (SIP) Assaults
The control plane in IMS is where session signaling, authentication, and routing happen through SIP (Session Initiation Protocol). Since SIP messages traverse IP networks, they can be exploited to overwhelm the system or manipulate sessions.
NEC’s IMS incorporates advanced guard functions at the Proxy-CSCF (P-CSCF) interface — the gateway between the LTE access network and IMS core — to guard against these threats.
Key Protective Measures:
a. Topology Concealment
Keeps the internal IMS architecture (like IP addresses, hostnames, and routes) hidden from outsiders.
Anonymizes SIP headers, making it harder for attackers to pinpoint or target IMS components directly.
This cuts down the risk of network reconnaissance and targeted DoS attacks.
b. Defenses Against Denial-of-Service (DoS) Attacks
Employs rate limiting and SIP message filtering to block attempts to flood the network or send malformed packets.
Continuously watches message traffic and rejects unusual signaling requests.
Protects crucial nodes like S/I-CSCF and TAS from being overloaded.
c. IPSec (IP Security) Encryption
Guarantees secure communication channels between User Equipment (UE) and IMS nodes.
Shields signaling traffic from eavesdropping, tampering, and replay attacks.
Utilizes strong encryption (ESP and IKEv2) and mutual authentication during SIP registration.
These strategies ensure that all signaling activities — from device registration to initiating calls — are authenticated, encrypted, and monitored.
Guard Functions Against User-Plane (RTP/RTCP) Attacks
Once a call session is active, media (voice or video) is sent through RTP (Real-time Transport Protocol) and RTCP (Real-time Transport Control Protocol).
The IMS Access Gateway (IMS-AGW) plays a crucial role in managing these streams. NEC’s IMS-AGW features media security functions to protect the network from malformed packets, overflows, and media injection threats.
Key Protective Measures:
a. Pinhole Control
Opens and closes network ports dynamically, but only for verified and active sessions.
Prevents attackers from taking advantage of open ports or injecting unauthorized media.
Guarantees that communication channels are available only when needed.
b. Packet Rate Monitoring
Tracks the rate of RTP and RTCP packets in real-time.
Detects and blocks unusual packet floods that could disrupt calls or exhaust network resources.
Maintains Quality of Experience (QoE) by ensuring a stable data flow.
c. Payload Type Validation
Checks the media format (codec type, packet size, etc.) to confirm it meets expected standards.
Rejects suspicious payloads that might carry harmful data or trigger buffer overflows.
Guards endpoints and network elements from malformed packet threats.
Combined, these protections help ensure that media sessions remain secure, stable, and free from unauthorized disruptions.
IMS Core Security Components in NEC’s Design
The diagram outlines the interconnected functions of key IMS components in enforcing security at various stages:
Component | Primary Security Role | Description
P-CSCF (Proxy Call Session Control Function) | Entry point protection | Manages SIP signaling security — topology obscuring, DoS prevention, and IPSec tunnel oversight.
S/I-CSCF (Serving/Interrogating CSCF) | Authentication and routing | Confirms user credentials, routes call sessions, and ensures message integrity.
TAS (Telephony Application Server) | Service logic security | Safeguards VoLTE/VoNR applications from misuse or session spoofing.
IMS-AGW (Access Gateway) | Media plane security | Oversees RTP/RTCP flows with pinhole control, packet validation, and flow monitoring.
These layers collaborate with the Evolved Packet Core (EPC) and Access Network (LTE) to provide comprehensive, end-to-end security coverage.
Why IMS Security Matters in Telecom Networks
The transition to VoLTE and 5G Standalone (SA) networks has moved voice and messaging traffic from traditional circuit-switched systems to pure IP frameworks. This evolution increases attack surfaces and necessitates real-time security measures.
Key Risks Without IMS Security:
SIP message spoofing leading to fraudulent calls.
DoS attacks overwhelming signaling systems.
RTP injection altering voice streams or disrupting video calls.
Exposure of network topology to hackers.
Unauthorized session hijacking via replay attacks.
By adopting NEC’s integrated IMS security solutions, operators can reduce these risks, maintain service uptime, and foster customer trust in their VoLTE setups.
Additional Security Protocols Used in IMS
NEC’s architecture follows 3GPP standards, implementing vital security protocols:
Protocol | Full Form | Purpose
SIP | Session Initiation Protocol | Manages, modifies, and ends communication sessions.
RTP | Real-time Transport Protocol | Sends real-time voice and video data.
RTCP | Real-time Transport Control Protocol | Oversees and regulates RTP session performance.
IPSec | Internet Protocol Security | Encrypts signaling and media traffic between IMS nodes.
Together, these protocols form a multi-layered defense that secures the complete service lifecycle — from signaling initiation to media delivery.
Merging IMS Security with LTE and 5G Networks
NEC’s IMS security framework fits smoothly with:
Evolved Packet Core (EPC) for LTE.
5G Core (5GC) for Voice over New Radio (VoNR).
This means whether a call starts on 4G, 5G, or Wi-Fi, the signaling and media channels stay secure. This cross-generational compatibility simplifies network migration while keeping consistent security protocols intact.
Conclusion: Laying a Secure Groundwork for Future Communication
As telecom providers roll out VoLTE, VoNR, and IMS-based services, having strong security measures isn't just a nice-to-have; it's essential.
NEC’s IMS products offer a well-rounded defense framework — from SIP signaling protection to RTP stream validation — ensuring that IP communications are secure and reliable.
By implementing topology concealment, DoS defenses, IPSec encryption, and dynamic media control, NEC helps service providers maintain network integrity, performance, and customer trust in a time of rising cyber threats.
In this connected age, where every call and data packet counts, NEC’s IMS security framework serves as a cornerstone for safe, scalable, and future-ready telecommunications.
